1. nginx基于Secret实现TLS实践
需求:
运⾏⼀个Nginx容器
Nginx虚拟站点配置⽂件来源于ConfigMap
Nginx虚拟站点需要使⽤的TLS证书,来源于Secret
验证Nginx服务是否已提供Https访问访问。
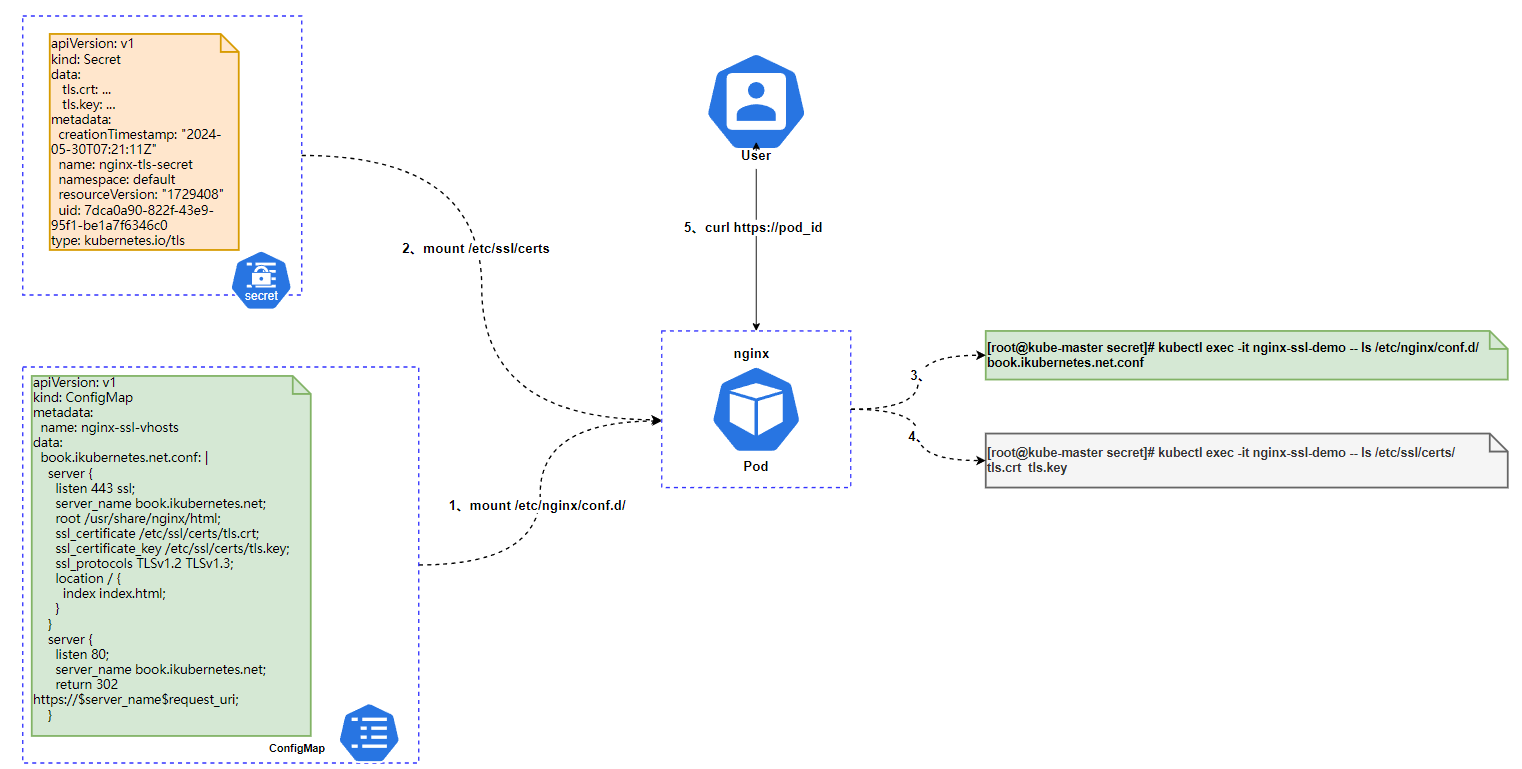
1.1 创建tls
bash
创建⾃签证书
#生成key
openssl genrsa -out nginx.key 2048
#生成crt
openssl req -new -x509 -key nginx.key -out nginx.crt -subj "/C=CN/ST=BJ/L=BJ/O=DevOps/CN=book.ikubernetes.net"
[root@kube-master secret]# kubectl create secret tls nginx-tls-secret --key=nginx.key --cert=nginx.crt
secret/nginx-tls-secret created创建⾃签证书
#生成key
openssl genrsa -out nginx.key 2048
#生成crt
openssl req -new -x509 -key nginx.key -out nginx.crt -subj "/C=CN/ST=BJ/L=BJ/O=DevOps/CN=book.ikubernetes.net"
[root@kube-master secret]# kubectl create secret tls nginx-tls-secret --key=nginx.key --cert=nginx.crt
secret/nginx-tls-secret created1.2 创建Configmap
yaml
cat 1.nginx-configmap.yaml
apiVersion: v1
kind: ConfigMap
metadata:
name: nginx-ssl-vhosts
data:
book.ikubernetes.net.conf: |
server {
listen 443 ssl;
server_name book.ikubernetes.net;
root /usr/share/nginx/html;
ssl_certificate /etc/ssl/certs/tls.crt;
ssl_certificate_key /etc/ssl/certs/tls.key;
ssl_protocols TLSv1.2 TLSv1.3;
location / {
index index.html;
}
}
server {
listen 80;
server_name book.ikubernetes.net;
return 302 https://$server_name$request_uri;
}cat 1.nginx-configmap.yaml
apiVersion: v1
kind: ConfigMap
metadata:
name: nginx-ssl-vhosts
data:
book.ikubernetes.net.conf: |
server {
listen 443 ssl;
server_name book.ikubernetes.net;
root /usr/share/nginx/html;
ssl_certificate /etc/ssl/certs/tls.crt;
ssl_certificate_key /etc/ssl/certs/tls.key;
ssl_protocols TLSv1.2 TLSv1.3;
location / {
index index.html;
}
}
server {
listen 80;
server_name book.ikubernetes.net;
return 302 https://$server_name$request_uri;
}bash
#执行
[root@kube-master secret]# kubectl apply -f 1.nginx-configmap.yaml
configmap/nginx-ssl-vhosts created#执行
[root@kube-master secret]# kubectl apply -f 1.nginx-configmap.yaml
configmap/nginx-ssl-vhosts created1.3 创建Pod
创建Nginxpod,挂载 ConfigMap 的虚拟主机配置,⽽后挂载虚拟主机所需要依赖的 tls 证书⽂件
yaml
[root@kube-master secret]# cat 2.nginx-pod-ssl.yaml
apiVersion: v1
kind: Pod
metadata:
name: nginx-ssl-demo
spec:
volumes:
- name: nginx-ssl-certs
secret:
secretName: nginx-tls-secret
- name: nginx-ssl-conf
configMap:
name: nginx-ssl-vhosts
items:
- key: book.ikubernetes.net.conf
path: book.ikubernetes.net.conf
containers:
- name: nginx-ssl-demo
image: nginx:latest
ports:
- containerPort: 80
- containerPort: 443
volumeMounts:
- name: nginx-ssl-certs
mountPath: /etc/ssl/certs/
readOnly: true
- name: nginx-ssl-conf
mountPath: /etc/nginx/conf.d/
readOnly: true[root@kube-master secret]# cat 2.nginx-pod-ssl.yaml
apiVersion: v1
kind: Pod
metadata:
name: nginx-ssl-demo
spec:
volumes:
- name: nginx-ssl-certs
secret:
secretName: nginx-tls-secret
- name: nginx-ssl-conf
configMap:
name: nginx-ssl-vhosts
items:
- key: book.ikubernetes.net.conf
path: book.ikubernetes.net.conf
containers:
- name: nginx-ssl-demo
image: nginx:latest
ports:
- containerPort: 80
- containerPort: 443
volumeMounts:
- name: nginx-ssl-certs
mountPath: /etc/ssl/certs/
readOnly: true
- name: nginx-ssl-conf
mountPath: /etc/nginx/conf.d/
readOnly: truebash
#执行
[root@kube-master secret]# kubectl apply -f 2.nginx-pod-ssl.yaml
#查看pod
[root@kube-master secret]# kubectl get pod nginx-ssl-demo -owide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-ssl-demo 1/1 Running 1 (5m35s ago) 176m 172.30.0.177 kube-node01 <none> <none>#执行
[root@kube-master secret]# kubectl apply -f 2.nginx-pod-ssl.yaml
#查看pod
[root@kube-master secret]# kubectl get pod nginx-ssl-demo -owide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-ssl-demo 1/1 Running 1 (5m35s ago) 176m 172.30.0.177 kube-node01 <none> <none>- 验证效果
bash
[root@kube-master secret]# curl -I -k https://172.30.0.177
HTTP/1.1 200 OK
Server: nginx/1.25.5
Date: Thu, 30 May 2024 13:27:04 GMT
Content-Type: text/html
Content-Length: 615
Last-Modified: Tue, 16 Apr 2024 14:29:59 GMT
Connection: keep-alive
ETag: "661e8b67-267"
Accept-Ranges: bytes
#查看ssl
[root@kube-master secret]# curl -I -v -k https://172.30.0.177
* About to connect() to 172.30.0.177 port 443 (#0)
* Trying 172.30.0.177...
* Connected to 172.30.0.177 (172.30.0.177) port 443 (#0)
* Initializing NSS with certpath: sql:/etc/pki/nssdb
* skipping SSL peer certificate verification
* SSL connection using TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
* Server certificate:
* subject: CN=book.ikubernetes.net,O=DevOps,L=BJ,ST=BJ,C=CN
* start date: 5月 30 07:18:43 2024 GMT
* expire date: 6月 29 07:18:43 2024 GMT
* common name: book.ikubernetes.net
* issuer: CN=book.ikubernetes.net,O=DevOps,L=BJ,ST=BJ,C=CN
> HEAD / HTTP/1.1
> User-Agent: curl/7.29.0
> Host: 172.30.0.177
> Accept: */*
>[root@kube-master secret]# curl -I -k https://172.30.0.177
HTTP/1.1 200 OK
Server: nginx/1.25.5
Date: Thu, 30 May 2024 13:27:04 GMT
Content-Type: text/html
Content-Length: 615
Last-Modified: Tue, 16 Apr 2024 14:29:59 GMT
Connection: keep-alive
ETag: "661e8b67-267"
Accept-Ranges: bytes
#查看ssl
[root@kube-master secret]# curl -I -v -k https://172.30.0.177
* About to connect() to 172.30.0.177 port 443 (#0)
* Trying 172.30.0.177...
* Connected to 172.30.0.177 (172.30.0.177) port 443 (#0)
* Initializing NSS with certpath: sql:/etc/pki/nssdb
* skipping SSL peer certificate verification
* SSL connection using TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
* Server certificate:
* subject: CN=book.ikubernetes.net,O=DevOps,L=BJ,ST=BJ,C=CN
* start date: 5月 30 07:18:43 2024 GMT
* expire date: 6月 29 07:18:43 2024 GMT
* common name: book.ikubernetes.net
* issuer: CN=book.ikubernetes.net,O=DevOps,L=BJ,ST=BJ,C=CN
> HEAD / HTTP/1.1
> User-Agent: curl/7.29.0
> Host: 172.30.0.177
> Accept: */*
>