1.freeapi 介绍
FreeIPA是一个用于Linux/Unix环境的开源身份管理系统,它提供集中式帐户管理和身份验证,如Microsoft Active Directory或LDAP。FreeIPA集成389目录服务器、MIT Kerberos、Apache HTTP服务器、NTP、DNS、Dogtag(证书系统)和SSSD,使其成为管理标识、策略和执行审计跟踪的单一集成安全解决方案。FreeIPA支持通过Web UI和命令行工具来执行管理任务
主要功能包括:
身份识别: (机器、用户、虚拟机、组、身份验证凭据)
策略: (配置设置,访问控制信息)
审计跟踪: (事件、日志、分析)主要功能包括:
身份识别: (机器、用户、虚拟机、组、身份验证凭据)
策略: (配置设置,访问控制信息)
审计跟踪: (事件、日志、分析)2.安装
https://github.com/freeipa/ansible-freeipa
- 注意
- centos7
- 内存至少 1.5 G 以上。
- Host 列请改为您自己的主机名。
- 本文都是以 root 用户进行操作,您可以使用其他有相应 sudo 权限的用户。
- 建议使用三级域名,如本例为
corp.example.com因为example.com一般为公网使用。 - 本机 IP 的子网掩码不能是
/32(255.255.255.255), 至少是/24(255.255.255.0) 或/16(255.255.0.0)。 - 启动防火墙,因为 LDAP 是非常重要的服务,安全性很重要
防火墙
FreeIPA可以选择关闭防火墙,或者打开防火墙需要使用的端口。如果防火墙关闭,则忽略该步剩下内容
firewall-cmd --permanent --add-port={80/tcp,443/tcp,389/tcp,636/tcp,88/tcp,464/tcp,53/tcp,88/udp,464/udp,53/udp,123/udp}
firewall-cmd --reload
#查看防火墙开放端口
firewall-cmd --zone=public --list-portsfirewall-cmd --permanent --add-port={80/tcp,443/tcp,389/tcp,636/tcp,88/tcp,464/tcp,53/tcp,88/udp,464/udp,53/udp,123/udp}
firewall-cmd --reload
#查看防火墙开放端口
firewall-cmd --zone=public --list-ports配置hosts文件
#添加
[root@ipa openldap]# cat /etc/hosts
172.18.106.132 ipa.freehan.ink ipa#添加
[root@ipa openldap]# cat /etc/hosts
172.18.106.132 ipa.freehan.ink ipa配置随机数生成器
设置FreeIPA需要大量随机数据来运行它的加密操作。默认情况下,虚拟机将很快耗尽随机数据或熵。为了解决这个问题,我们将使用rngd软件随机数生成器。rngd通过从连接到其他服务器的硬件设备获取数据并将其提供给内核的随机数生成器来工作
yum -y install rng-toolsyum -y install rng-tools启用
systemctl start rngd
systemctl enable rngd
systemctl status rngdsystemctl start rngd
systemctl enable rngd
systemctl status rngd安装
#安装ipa-server,也就是FreeIPA服务。如果不需要配置dns,也可以不安装ipa-server-dns包
[root@ipa ~]#yum -y install bind bind-utils bind-dyndb-ldap
[root@ipa ~]# yum -y install ipa-server ipa-server-dns
vi /etc/named.conf -- 将以下两个参数改为 yes
dnssec-enable yes;
dnssec-validation yes;
[root@ipa ~]# ipa-server-install --allow-zone-overlap
The log file for this installation can be found in /var/log/ipaserver-install.log
==============================================================================
This program will set up the IPA Server.
This includes:
* Configure a stand-alone CA (dogtag) for certificate management
* Configure the Network Time Daemon (ntpd)
* Create and configure an instance of Directory Server
* Create and configure a Kerberos Key Distribution Center (KDC)
* Configure Apache (httpd)
* Configure the KDC to enable PKINIT
To accept the default shown in brackets, press the Enter key.
Do you want to configure integrated DNS (BIND)? [no]: no --->用不到dns
Enter the fully qualified domain name of the computer
on which you're setting up server software. Using the form
<hostname>.<domainname>
Example: master.example.com.
Server host name [ipa.freehan.ink]: ipa.freehan.ink
Warning: skipping DNS resolution of host ipa.kclouder.local
The domain name has been determined based on the host name.
Please confirm the domain name [kclouder.local]: freehan.ink
The kerberos protocol requires a Realm name to be defined.
This is typically the domain name converted to uppercase.
-------------------------------------
警告:不要将您的根域(example.com)用作您的IPA域名。这可能会导致DNS问题
Server host name [ipa.example.org]: ipa.example.org
Please confirm the domain name [example.org]: ipa.example.org
Please provide a realm name [EXAMPLE.ORG]: IPA.EXAMPLE.ORG
-------------------------------------
Please provide a realm name [KCLOUDER.LOCAL]: FREEHAN.INK
Certain directory server operations require an administrative user.
This user is referred to as the Directory Manager and has full access
to the Directory for system management tasks and will be added to the
instance of directory server created for IPA.
The password must be at least 8 characters long.
Directory Manager password: <--输入密码(Directory manager password)
Password (confirm): <--输入密码(Directory manager password)
The IPA server requires an administrative user, named 'admin'.
This user is a regular system account used for IPA server administration.
IPA admin password: <--输入密码(IPA Admin password)
Password (confirm): <--输入密码(IPA Admin password)#安装ipa-server,也就是FreeIPA服务。如果不需要配置dns,也可以不安装ipa-server-dns包
[root@ipa ~]#yum -y install bind bind-utils bind-dyndb-ldap
[root@ipa ~]# yum -y install ipa-server ipa-server-dns
vi /etc/named.conf -- 将以下两个参数改为 yes
dnssec-enable yes;
dnssec-validation yes;
[root@ipa ~]# ipa-server-install --allow-zone-overlap
The log file for this installation can be found in /var/log/ipaserver-install.log
==============================================================================
This program will set up the IPA Server.
This includes:
* Configure a stand-alone CA (dogtag) for certificate management
* Configure the Network Time Daemon (ntpd)
* Create and configure an instance of Directory Server
* Create and configure a Kerberos Key Distribution Center (KDC)
* Configure Apache (httpd)
* Configure the KDC to enable PKINIT
To accept the default shown in brackets, press the Enter key.
Do you want to configure integrated DNS (BIND)? [no]: no --->用不到dns
Enter the fully qualified domain name of the computer
on which you're setting up server software. Using the form
<hostname>.<domainname>
Example: master.example.com.
Server host name [ipa.freehan.ink]: ipa.freehan.ink
Warning: skipping DNS resolution of host ipa.kclouder.local
The domain name has been determined based on the host name.
Please confirm the domain name [kclouder.local]: freehan.ink
The kerberos protocol requires a Realm name to be defined.
This is typically the domain name converted to uppercase.
-------------------------------------
警告:不要将您的根域(example.com)用作您的IPA域名。这可能会导致DNS问题
Server host name [ipa.example.org]: ipa.example.org
Please confirm the domain name [example.org]: ipa.example.org
Please provide a realm name [EXAMPLE.ORG]: IPA.EXAMPLE.ORG
-------------------------------------
Please provide a realm name [KCLOUDER.LOCAL]: FREEHAN.INK
Certain directory server operations require an administrative user.
This user is referred to as the Directory Manager and has full access
to the Directory for system management tasks and will be added to the
instance of directory server created for IPA.
The password must be at least 8 characters long.
Directory Manager password: <--输入密码(Directory manager password)
Password (confirm): <--输入密码(Directory manager password)
The IPA server requires an administrative user, named 'admin'.
This user is a regular system account used for IPA server administration.
IPA admin password: <--输入密码(IPA Admin password)
Password (confirm): <--输入密码(IPA Admin password)状态
[root@ipa openldap]# ipactl status
Directory Service: RUNNING
krb5kdc Service: RUNNING
kadmin Service: RUNNING
httpd Service: RUNNING
ipa-custodia Service: RUNNING
ntpd Service: RUNNING
pki-tomcatd Service: RUNNING
ipa-otpd Service: RUNNING
ipa: INFO: The ipactl command was successful[root@ipa openldap]# ipactl status
Directory Service: RUNNING
krb5kdc Service: RUNNING
kadmin Service: RUNNING
httpd Service: RUNNING
ipa-custodia Service: RUNNING
ntpd Service: RUNNING
pki-tomcatd Service: RUNNING
ipa-otpd Service: RUNNING
ipa: INFO: The ipactl command was successful验证FreeIPA服务功能
#通过尝试为admin用户初始化Kerberos令牌来验证Kerberos域是否已正确安装
[root@ipa openldap]# kinit admin
Password for admin@FREEHAN.INK: 输入admin密码
[root@ipa openldap]# klist
Ticket cache: KEYRING:persistent:0:0
Default principal: admin@FREEHAN.INK
Valid starting Expires Service principal
11/25/2021 16:19:35 11/26/2021 16:19:32 krbtgt/FREEHAN.INK@FREEHAN.INK
#验证IPA服务器是否正常运行
[root@ipa openldap]# ipa user-find admin
--------------
1 user matched
--------------
User login: admin
Last name: Administrator
Home directory: /home/admin
Login shell: /bin/bash
Principal alias: admin@FREEHAN.INK
UID: 428200000
GID: 428200000
Account disabled: False
----------------------------
Number of entries returned 1
----------------------------#通过尝试为admin用户初始化Kerberos令牌来验证Kerberos域是否已正确安装
[root@ipa openldap]# kinit admin
Password for admin@FREEHAN.INK: 输入admin密码
[root@ipa openldap]# klist
Ticket cache: KEYRING:persistent:0:0
Default principal: admin@FREEHAN.INK
Valid starting Expires Service principal
11/25/2021 16:19:35 11/26/2021 16:19:32 krbtgt/FREEHAN.INK@FREEHAN.INK
#验证IPA服务器是否正常运行
[root@ipa openldap]# ipa user-find admin
--------------
1 user matched
--------------
User login: admin
Last name: Administrator
Home directory: /home/admin
Login shell: /bin/bash
Principal alias: admin@FREEHAN.INK
UID: 428200000
GID: 428200000
Account disabled: False
----------------------------
Number of entries returned 1
----------------------------DNS说明
DNS用于机器名解析,如果安装FreeIPA双机(即主从Server),那就需要DNS 原因:我们需要执行类似于如下的命令:
ipa-replica-prepare hadoop197.example.com --ip-address 192.168.116.197ipa-replica-prepare hadoop197.example.com --ip-address 192.168.116.197此时它就会去DNS上面的解析,找不到,就直接报错。此时就导致从节点无法安装。如果我们只安装freeipa的单节点,就可以不使用DNS
登录web界面

更换证书ssl
一般有 3 个文件
- ca.crt(CA 证书)
- your_domain.crt(域名的公钥证书)
- your_domain.key(域名的私钥证书)
通过如下命令配置,这个命令不会将密码保存到 shell 的历史中,更安全。
# ipa-cacert-manage -p your_directory_manager_password -n httpcrt -t C,, install ca.crt# ipa-cacert-manage -p your_directory_manager_password -n httpcrt -t C,, install ca.crt更新证书到数据库
ipa-certupdateipa-certupdate安装站点的公钥和私钥
# ipa-server-certinstall -w -d your_domain.key your_domain.crt# ipa-server-certinstall -w -d your_domain.key your_domain.crt重启服务
sysmtemctl restart ipasysmtemctl restart ipa2.用户管理
配置IPA用户
FreeIPA拥有非常广泛的用户管理和策略功能。与标准Unix用户类似,FreeIPA用户可以属于组。可以允许或拒绝组或个人用户基于策略访问主机(客户端计算机)或主机组(主机组)。FreeIPA还可以管理sudo访问,可以在主机或主机组上授予组或用户sudo访问权限
要添加用户,请单击“ 标识”选项卡,然后单击“用户”。这将显示一个用户表。单击表格上方的+添加按钮以添加新用户。在打开的表单中填写必填字段(如名字和姓氏),然后单击添加以按原样添加用户或添加和编辑以配置高级详细信息。
单击原始表中的用户也可以访问高级详细信息。这是管理员在查看用户详细信息时看到的内容
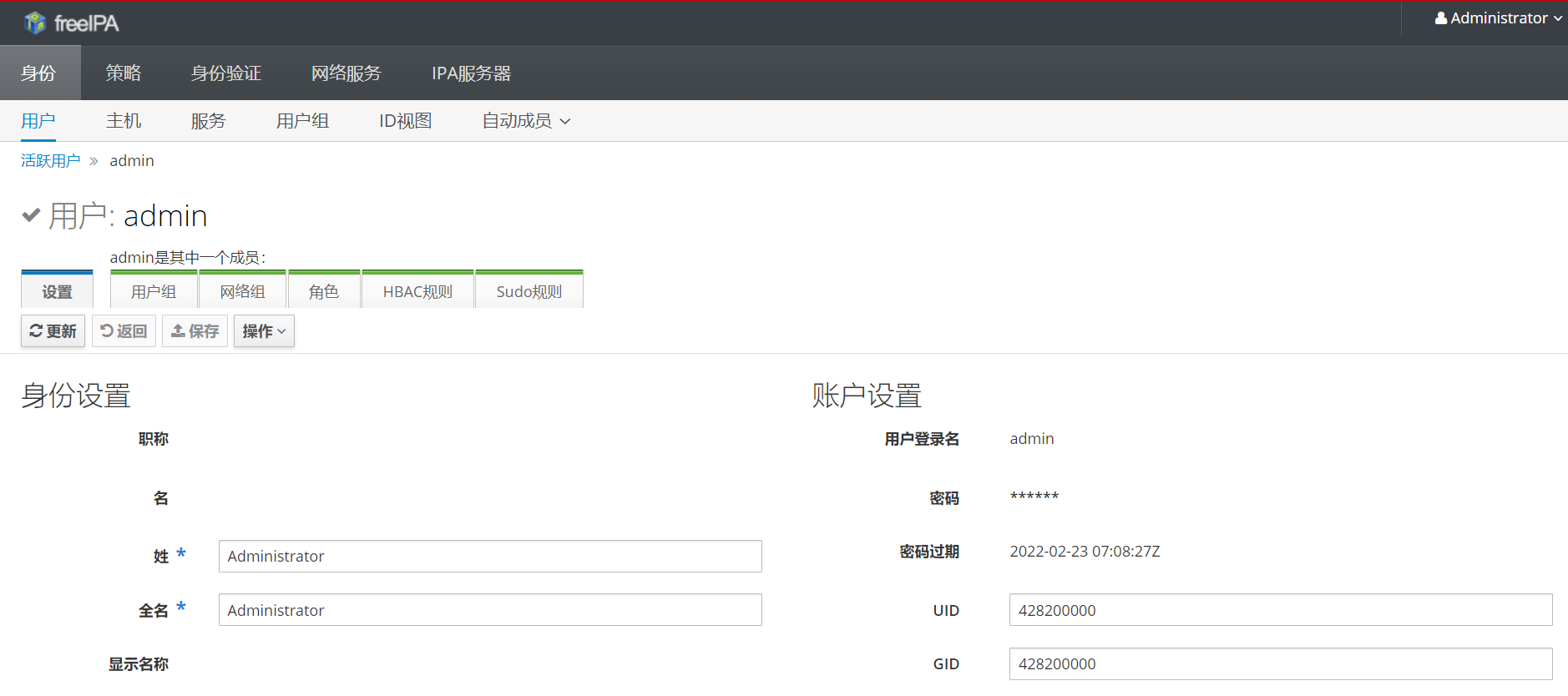
普通用户也可以登录IPA GUI。他们将能够查看自己的权限并编辑个人详细信息。
首次登录IPA计算机时,系统会要求新用户更改密码。这适用于IPA GUI以及SSH。IPA可以添加添加SSH密钥的能力。用户可以上传他们的公共SSH密钥并将它们传播到IPA机器,允许无密码登录。然后,用户可以随时删除SSH密钥,无需担心它仍存在于各个服务器上。
通过列表添加用户帐户和列出帐户进行测试
[root@ipa openldap]# ipa user-add jmumr --first=Josphatmr --last=Mutaimr --email=jmutai@computingforgeeks.com --shell=/bin/bash --password
Password:
Enter Password again to verify:
------------------
Added user "jmumr"
------------------
User login: jmumr
First name: Josphatmr
Last name: Mutaimr
Full name: Josphatmr Mutaimr
Display name: Josphatmr Mutaimr
Initials: JM
Home directory: /home/jmumr
GECOS: Josphatmr Mutaimr
Login shell: /bin/bash
Principal name: jmumr@FREEHAN.INK
Principal alias: jmumr@FREEHAN.INK
User password expiration: 20211125084700Z
Email address: jmutai@computingforgeeks.com
UID: 428200003
GID: 428200003
Password: True
Member of groups: ipausers
Kerberos keys available: True[root@ipa openldap]# ipa user-add jmumr --first=Josphatmr --last=Mutaimr --email=jmutai@computingforgeeks.com --shell=/bin/bash --password
Password:
Enter Password again to verify:
------------------
Added user "jmumr"
------------------
User login: jmumr
First name: Josphatmr
Last name: Mutaimr
Full name: Josphatmr Mutaimr
Display name: Josphatmr Mutaimr
Initials: JM
Home directory: /home/jmumr
GECOS: Josphatmr Mutaimr
Login shell: /bin/bash
Principal name: jmumr@FREEHAN.INK
Principal alias: jmumr@FREEHAN.INK
User password expiration: 20211125084700Z
Email address: jmutai@computingforgeeks.com
UID: 428200003
GID: 428200003
Password: True
Member of groups: ipausers
Kerberos keys available: True- web界面查看
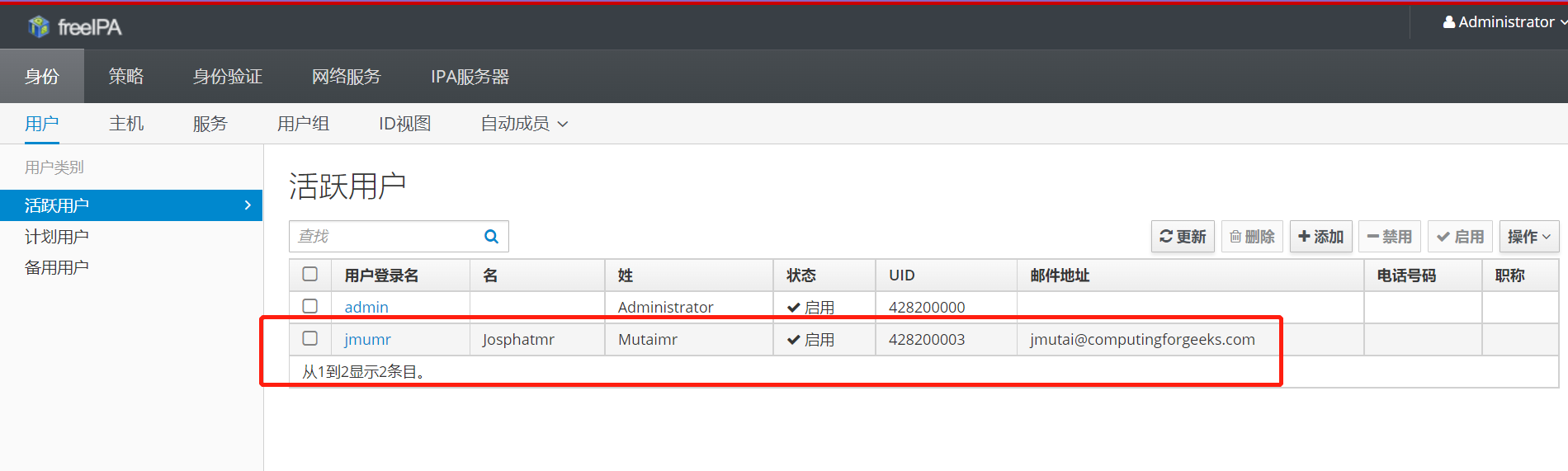
过滤用户
[root@ipa openldap]# ipa user-find |grep User |awk -F':' '{print $2}'
admin
jmumr[root@ipa openldap]# ipa user-find |grep User |awk -F':' '{print $2}'
admin
jmumr设置otp
3.安装client端
FreeIPA的客户端软件
yum -y install ipa-client ntpFreeIPA的客户端软件
yum -y install ipa-client ntp执行客户端安装
客户端安装有两种方式,交互式和非交互式
非交互式安装
[root@ipa112 ~]# ipa-client-install --domain=example.com --realm=EXAMPLE.COM --principal=admin@EXAMPLE.COM --password=hadoop123 --enable-dns-updates --permit --no-ntp
Provide your IPA server name (ex:ipa.example.com): ipa110.example.com --输入ipaserver,需要注意后面一定不要带空格,否则就会抛出异常[root@ipa112 ~]# ipa-client-install --domain=example.com --realm=EXAMPLE.COM --principal=admin@EXAMPLE.COM --password=hadoop123 --enable-dns-updates --permit --no-ntp
Provide your IPA server name (ex:ipa.example.com): ipa110.example.com --输入ipaserver,需要注意后面一定不要带空格,否则就会抛出异常交互式安装
执行下列的命令来执行安装
ipa-client-installipa-client-install开始安装:
[root@ipa ~]#ipa-client-install
WARNING: ntpd time&date synchronizationservice will not be configured as
conflicting service (chronyd) is enabled
Use --force-ntpd option to disable it and forceconfiguration of ntpd
DNS discovery failed to determine your DNS domain
Provide the domain name ofyour IPA server (ex: example.com): gce.cloudera.com
Provide your IPA server name(ex: ipa.example.com): wang-1.gce.cloudera.com
The failure to use DNS to find your IPA serverindicates that your resolv.conf file is not properly configured.
Autodiscovery of servers for failover cannot workwith this configuration.
If you proceed with the installation, serviceswill be configured to always access the discovered server for all operationsand will not fail over to other servers in case of failure.
Proceed with fixed values andno DNS discovery? [no]: yes
Client hostname: wang-2.gce.cloudera.com
Realm: GCE.CLOUDERA.COM
DNS Domain: gce.cloudera.com
IPA Server: wang-1.gce.cloudera.com
BaseDN: dc=gce,dc=cloudera,dc=com
Continue to configure thesystem with these values? [no]: yes
Skipping synchronizing time with NTP server.
User authorized to enroll computers: admin
Password for admin@GCE.CLOUDERA.COM:
Successfully retrieved CA cert
Subject: CN=CertificateAuthority,O=GCE.CLOUDERA.COM
Issuer: CN=CertificateAuthority,O=GCE.CLOUDERA.COM
ValidFrom: 2019-08-11 13:44:00
ValidUntil: 2039-08-11 13:44:00
Enrolled in IPA realm GCE.CLOUDERA.COM
Created /etc/ipa/default.conf
New SSSD config will be created
Configured sudoers in /etc/nsswitch.conf
Configured /etc/sssd/sssd.conf
Configured /etc/krb5.conf for IPA realmGCE.CLOUDERA.COM
trying https://wang-1.gce.cloudera.com/ipa/json
[try 1]: Forwarding 'schema' to json server'https://wang-1.gce.cloudera.com/ipa/json'
trying https://wang-1.gce.cloudera.com/ipa/session/json
[try 1]: Forwarding 'ping' to json server'https://wang-1.gce.cloudera.com/ipa/session/json'
[try 1]: Forwarding 'ca_is_enabled' to json server'https://wang-1.gce.cloudera.com/ipa/session/json'
Systemwide CA database updated.
Adding SSH public key from/etc/ssh/ssh_host_rsa_key.pub
Adding SSH public key from/etc/ssh/ssh_host_ecdsa_key.pub
Adding SSH public key from/etc/ssh/ssh_host_ed25519_key.pub
[try 1]: Forwarding 'host_mod' to json server'https://wang-1.gce.cloudera.com/ipa/session/json'
Could not update DNS SSHFP records.
SSSD enabled
Configured /etc/openldap/ldap.conf
Configured /etc/ssh/ssh_config
Configured /etc/ssh/sshd_config
Configuring gce.cloudera.com as NIS domain.
Client configuration complete.
The ipa-client-install command was successful[root@ipa ~]#ipa-client-install
WARNING: ntpd time&date synchronizationservice will not be configured as
conflicting service (chronyd) is enabled
Use --force-ntpd option to disable it and forceconfiguration of ntpd
DNS discovery failed to determine your DNS domain
Provide the domain name ofyour IPA server (ex: example.com): gce.cloudera.com
Provide your IPA server name(ex: ipa.example.com): wang-1.gce.cloudera.com
The failure to use DNS to find your IPA serverindicates that your resolv.conf file is not properly configured.
Autodiscovery of servers for failover cannot workwith this configuration.
If you proceed with the installation, serviceswill be configured to always access the discovered server for all operationsand will not fail over to other servers in case of failure.
Proceed with fixed values andno DNS discovery? [no]: yes
Client hostname: wang-2.gce.cloudera.com
Realm: GCE.CLOUDERA.COM
DNS Domain: gce.cloudera.com
IPA Server: wang-1.gce.cloudera.com
BaseDN: dc=gce,dc=cloudera,dc=com
Continue to configure thesystem with these values? [no]: yes
Skipping synchronizing time with NTP server.
User authorized to enroll computers: admin
Password for admin@GCE.CLOUDERA.COM:
Successfully retrieved CA cert
Subject: CN=CertificateAuthority,O=GCE.CLOUDERA.COM
Issuer: CN=CertificateAuthority,O=GCE.CLOUDERA.COM
ValidFrom: 2019-08-11 13:44:00
ValidUntil: 2039-08-11 13:44:00
Enrolled in IPA realm GCE.CLOUDERA.COM
Created /etc/ipa/default.conf
New SSSD config will be created
Configured sudoers in /etc/nsswitch.conf
Configured /etc/sssd/sssd.conf
Configured /etc/krb5.conf for IPA realmGCE.CLOUDERA.COM
trying https://wang-1.gce.cloudera.com/ipa/json
[try 1]: Forwarding 'schema' to json server'https://wang-1.gce.cloudera.com/ipa/json'
trying https://wang-1.gce.cloudera.com/ipa/session/json
[try 1]: Forwarding 'ping' to json server'https://wang-1.gce.cloudera.com/ipa/session/json'
[try 1]: Forwarding 'ca_is_enabled' to json server'https://wang-1.gce.cloudera.com/ipa/session/json'
Systemwide CA database updated.
Adding SSH public key from/etc/ssh/ssh_host_rsa_key.pub
Adding SSH public key from/etc/ssh/ssh_host_ecdsa_key.pub
Adding SSH public key from/etc/ssh/ssh_host_ed25519_key.pub
[try 1]: Forwarding 'host_mod' to json server'https://wang-1.gce.cloudera.com/ipa/session/json'
Could not update DNS SSHFP records.
SSSD enabled
Configured /etc/openldap/ldap.conf
Configured /etc/ssh/ssh_config
Configured /etc/ssh/sshd_config
Configuring gce.cloudera.com as NIS domain.
Client configuration complete.
The ipa-client-install command was successful4.FreeIPA热备配置
文档建议,每个数据中心推荐2-3个副本,但不要超过4个
先在主服务器ipa server上执行
kinit admin
ipa-replica-prepare wang-3.gce.cloudera.com
Replicacreation using 'ipa-replica-prepare' to generate replica file
is supported only in 0-level IPA domain.
The current IPA domain level is 1 and thus thereplica must
be created by promoting an existing IPA client.
To set up a replica use the following procedure:
1.) set up a client on the hostusing 'ipa-client-install'
2.) promote the client to replicarunning 'ipa-replica-install'
*without* replica filespecified
'ipa-replica-prepare' is allowed only in domainlevel 0
The ipa-replica-prepare command failed.kinit admin
ipa-replica-prepare wang-3.gce.cloudera.com
Replicacreation using 'ipa-replica-prepare' to generate replica file
is supported only in 0-level IPA domain.
The current IPA domain level is 1 and thus thereplica must
be created by promoting an existing IPA client.
To set up a replica use the following procedure:
1.) set up a client on the hostusing 'ipa-client-install'
2.) promote the client to replicarunning 'ipa-replica-install'
*without* replica filespecified
'ipa-replica-prepare' is allowed only in domainlevel 0
The ipa-replica-prepare command failed.以上操作报错:所以,先在 副本服务器安装 ipa-client及安装ipa-replica
主服务器添加节点
在 wang-3副本服务器安装ipa-client 安装之前,先执行添加服务器操作
[root@wang-2 ~]# ipa host-add --force--ip-address=172.31.115.236 wang-3.gce.cloudera.com
------------------------------------
Added host "wang-3.gce.cloudera.com"
------------------------------------
Host name:wang-3.gce.cloudera.com
Principalname: host/wang-3.gce.cloudera.com@GCE.CLOUDERA.COM
Principalalias: host/wang-3.gce.cloudera.com@GCE.CLOUDERA.COM
Password:False
Keytab:False
Managedby: wang-3.gce.cloudera.com[root@wang-2 ~]# ipa host-add --force--ip-address=172.31.115.236 wang-3.gce.cloudera.com
------------------------------------
Added host "wang-3.gce.cloudera.com"
------------------------------------
Host name:wang-3.gce.cloudera.com
Principalname: host/wang-3.gce.cloudera.com@GCE.CLOUDERA.COM
Principalalias: host/wang-3.gce.cloudera.com@GCE.CLOUDERA.COM
Password:False
Keytab:False
Managedby: wang-3.gce.cloudera.com检查是否添加成功
[root@wang-2 ~]# ipa host-find
---------------
2 hosts matched
---------------
Host name:wang-2.gce.cloudera.com
Principalname: host/wang-2.gce.cloudera.com@GCE.CLOUDERA.COM
Principalalias: host/wang-2.gce.cloudera.com@GCE.CLOUDERA.COM
SSH publickey fingerprint: SHA256:rwMkR/W/nz4EIzH3b+BLFLjb0tr7UA4vDR4wmBp4l9o root@wang-2(ssh-rsa),
SHA256:ppQgDl79Xw/IBqhzutNgqsLgvxAOfSGVOl1OhtV00cY root@wang-2(ecdsa-sha2-nistp256),
SHA256:IwracriO47xdmQLkvUODn47swUpp0f4tQ2OcmodVqQg root@wang-2(ssh-ed25519)
Host name:wang-3.gce.cloudera.com
Principalname: host/wang-3.gce.cloudera.com@GCE.CLOUDERA.COM
Principalalias: host/wang-3.gce.cloudera.com@GCE.CLOUDERA.COM
----------------------------
Number of entries returned 2
----------------------------[root@wang-2 ~]# ipa host-find
---------------
2 hosts matched
---------------
Host name:wang-2.gce.cloudera.com
Principalname: host/wang-2.gce.cloudera.com@GCE.CLOUDERA.COM
Principalalias: host/wang-2.gce.cloudera.com@GCE.CLOUDERA.COM
SSH publickey fingerprint: SHA256:rwMkR/W/nz4EIzH3b+BLFLjb0tr7UA4vDR4wmBp4l9o root@wang-2(ssh-rsa),
SHA256:ppQgDl79Xw/IBqhzutNgqsLgvxAOfSGVOl1OhtV00cY root@wang-2(ecdsa-sha2-nistp256),
SHA256:IwracriO47xdmQLkvUODn47swUpp0f4tQ2OcmodVqQg root@wang-2(ssh-ed25519)
Host name:wang-3.gce.cloudera.com
Principalname: host/wang-3.gce.cloudera.com@GCE.CLOUDERA.COM
Principalalias: host/wang-3.gce.cloudera.com@GCE.CLOUDERA.COM
----------------------------
Number of entries returned 2
----------------------------热备服务器安装client
[root@wang-2 ~]# ipa host-find
5.卸载
ipa-server-install -U --uninstall #服务端卸
ipa-client-install -U --uninstall #客户端卸载
#删除残留文件,避免二次安装失败
cd /var/lib/ipa/
rm -f ca*
rm -f *.txt
rm -f sysrestore/*
cd /var/lib/dirsrv/
rm -rf scripts*
cd /var/run/dirsrv/
rm -rf slapd*
cd /etc/ipa
rm -f ca.crt
cd /var/log/dirsrv
rm -rf slapd*
rm -rf /var/lib/pki* /var/log/pki* /etc/init.d/pki*
rm -rf /usr/share/pki /usr/share/tomcat5/var/lib/tomcat5/
#卸载软件包
yum erase -y `rpmquery -a | grep freeipa``rpmquery -a | grep ^pki-` `rpmquery -a | grep tomcat6` `rpmquery -a | grep httpd` 389-ds-base bindipa-server-install -U --uninstall #服务端卸
ipa-client-install -U --uninstall #客户端卸载
#删除残留文件,避免二次安装失败
cd /var/lib/ipa/
rm -f ca*
rm -f *.txt
rm -f sysrestore/*
cd /var/lib/dirsrv/
rm -rf scripts*
cd /var/run/dirsrv/
rm -rf slapd*
cd /etc/ipa
rm -f ca.crt
cd /var/log/dirsrv
rm -rf slapd*
rm -rf /var/lib/pki* /var/log/pki* /etc/init.d/pki*
rm -rf /usr/share/pki /usr/share/tomcat5/var/lib/tomcat5/
#卸载软件包
yum erase -y `rpmquery -a | grep freeipa``rpmquery -a | grep ^pki-` `rpmquery -a | grep tomcat6` `rpmquery -a | grep httpd` 389-ds-base bindFAQ
ipa: ERROR: did not receive Kerberos credentials
#解决方式
kinit username(根据自己的修改)
解锁用户的话再执行
ipa user-unlock usernameipa: ERROR: did not receive Kerberos credentials
#解决方式
kinit username(根据自己的修改)
解锁用户的话再执行
ipa user-unlock username