https://github.com/v2fly/fhs-install-v2ray
1.安装acme
ubuntu系统
安装acme: curl https://get.acme.sh
安装socat: apt install socat
添加软链接: ln -s /root/.acme.sh/acme.sh /usr/local/bin/acme.sh安装acme: curl https://get.acme.sh
安装socat: apt install socat
添加软链接: ln -s /root/.acme.sh/acme.sh /usr/local/bin/acme.sh2.注册账号
语法:
acme.sh --register-account -m my@example.com
root@iZj6c9jm2xw77w13d79ecbZ:~/vmess# acme.sh --register-account -m hsuing.hx@southhere.com
[Wed Apr 5 11:29:58 CST 2023] Create account key ok.
[Wed Apr 5 11:29:58 CST 2023] No EAB credentials found for ZeroSSL, let's get one
[Wed Apr 5 11:30:00 CST 2023] Registering account: https://acme.zerossl.com/v2/DV90
[Wed Apr 5 11:30:02 CST 2023] Registered
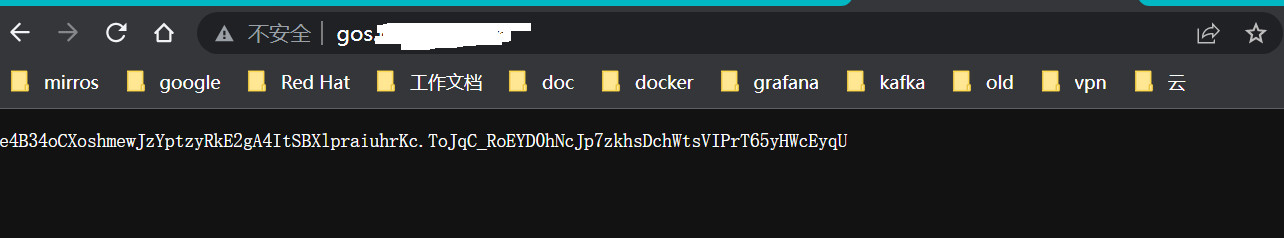
[Wed Apr 5 11:30:02 CST 2023] ACCOUNT_THUMBPRINT='ToJqC_RoEYD0hNcJp7zkhsDchWtsVIPrT65yHWcEyqU'root@iZj6c9jm2xw77w13d79ecbZ:~/vmess# acme.sh --register-account -m hsuing.hx@southhere.com
[Wed Apr 5 11:29:58 CST 2023] Create account key ok.
[Wed Apr 5 11:29:58 CST 2023] No EAB credentials found for ZeroSSL, let's get one
[Wed Apr 5 11:30:00 CST 2023] Registering account: https://acme.zerossl.com/v2/DV90
[Wed Apr 5 11:30:02 CST 2023] Registered
[Wed Apr 5 11:30:02 CST 2023] ACCOUNT_THUMBPRINT='ToJqC_RoEYD0hNcJp7zkhsDchWtsVIPrT65yHWcEyqU'3.申请证书
3.1 http方式
开放80端口: ufw allow 80
#这里的域名(申请证书的域名要提前解析到dns上面),要访问web服务,这个acme会自己提供
#acme.sh --issue -d domain.com --standalone -k ec-256#acme.sh --issue -d domain.com --standalone -k ec-256#成功现象
root@iZj6c9jm2xw77w13d79ecbZ:~# acme.sh --issue -d gos.xxx.info --standalone -k ec-256
[Thu Apr 6 12:51:26 CST 2023] Using CA: https://acme.zerossl.com/v2/DV90
[Thu Apr 6 12:51:26 CST 2023] Standalone mode.
[Thu Apr 6 12:51:27 CST 2023] Single domain='gos.naigosto.info'
[Thu Apr 6 12:51:27 CST 2023] Getting domain auth token for each domain
[Thu Apr 6 12:51:31 CST 2023] Getting webroot for domain='gos.naigosto.info'
[Thu Apr 6 12:51:31 CST 2023] Verifying: gos.naigosto.info
[Thu Apr 6 12:51:31 CST 2023] Standalone mode server
[Thu Apr 6 12:51:33 CST 2023] Processing, The CA is processing your order, please just wait. (1/30)
[Thu Apr 6 12:51:37 CST 2023] Success
[Thu Apr 6 12:51:37 CST 2023] Verify finished, start to sign.
[Thu Apr 6 12:51:37 CST 2023] Lets finalize the order.
[Thu Apr 6 12:51:37 CST 2023] Le_OrderFinalize='https://acme.zerossl.com/v2/DV90/order/Mth3kUpt_ANMr3xrfT94sg/finalize'
[Thu Apr 6 12:51:38 CST 2023] Order status is processing, lets sleep and retry.
[Thu Apr 6 12:51:39 CST 2023] Retry after: 15
[Thu Apr 6 12:51:55 CST 2023] Polling order status: https://acme.zerossl.com/v2/DV90/order/Mth3kUpt_ANMr3xrfT94sg
[Thu Apr 6 12:51:56 CST 2023] Downloading cert.
[Thu Apr 6 12:51:56 CST 2023] Le_LinkCert='https://acme.zerossl.com/v2/DV90/cert/2QU0KxSksAAtC7fzQdxzhQ'
[Thu Apr 6 12:51:57 CST 2023] Cert success.
-----BEGIN CERTIFICATE-----
MIIEBjCCA4ygAwIBAgIRAJTDtMaaTte2W7mIXyeoF98wCgYIKoZIzj0EAwMwSzEL
MAkGA1UEBhMCQVQxEDAOBgNVBAoTB1plcm9TU0wxKjAoBgNVBAMTIVplcm9TU0wg
RUNDIERvbWFpbiBTZWN1cmUgU2l0ZSBDQTAeFw0yMzA0MDYwMDAwMDBaFw0yMzA3
MDUyMzU5NTlaMBwxGjAYBgNVBAMTEWdvcy5uYWlnb3N0by5pbmZvMFkwEwYHKoZI
zj0CAQYIKoZIzj0DAQcDQgAEJbby2wcHB6OgwcdU4C+Tyuo7sbqF2oxfmBHUtI5E
sZO+aHfG7SzD+pSUXslAjDZhfr5EEkC4SamRmIcFYAtudqOCAn4wggJ6MB8GA1Ud
IwQYMBaAFA9r5kvOOUeu9n6QHnnwMJGSyF+jMB0GA1UdDgQWBBQs5kJ/z/D88jwS
C/Y7YVenJOKNUjAOBgNVHQ8BAf8EBAMCB4AwDAYDVR0TAQH/BAIwADAdBgNVHSUE
FjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwSQYDVR0gBEIwQDA0BgsrBgEEAbIxAQIC
TjAlMCMGCCsGAQUFBwIBFhdodHRwczovL3NlY3RpZ28uY29tL0NQUzAIBgZngQwB
AgEwgYgGCCsGAQUFBwEBBHwwejBLBggrBgEFBQcwAoY/aHR0cDovL3plcm9zc2wu
Y3J0LnNlY3RpZ28uY29tL1plcm9TU0xFQ0NEb21haW5TZWN1cmVTaXRlQ0EuY3J0
MCsGCCsGAQUFBzABhh9odHRwOi8vemVyb3NzbC5vY3NwLnNlY3RpZ28uY29tMIIB
BQYKKwYBBAHWeQIEAgSB9gSB8wDxAHYArfe++nz/EMiLnT2cHj4YarRnKV3PsQwk
yoWGNOvcgooAAAGHVOfwqgAABAMARzBFAiEAw+MQPi+jYxnPsAFfp0fgqe1qBIqV
a4YAqJbe6tJlgiECIG6k4m75tq0JYa8HuoXfcMvRW+7UUXQG/yGisYqrGRQOAHcA
ejKMVNi3LbYg6jjgUh7phBZwMhOFTTvSK8E6V6NS61IAAAGHVOfw/wAABAMASDBG
AiEA5e/LDLwFIOz0HNLLOu9vHfMM0rHMX9j7/Uy8licGSN4CIQDMdbQ7tune0lCt
VVR+YWesbfLuXP0v6FyNeitVRRrS/jAcBgNVHREEFTATghFnb3MubmFpZ29zdG8u
aW5mbzAKBggqhkjOPQQDAwNoADBlAjBgFji3ea/AxurHp8msibPhPrErnXQkVQLA
OC0YBvVDEzqgY63A+eSHb6nibwE2s1gCMQDaSr20Bm0J1EWm9x42KmY1+gW0k87I
Ii09QL2hunLTMV72jvg22dUBDBSvdvJ0hhM=
-----END CERTIFICATE-----
[Thu Apr 6 12:51:57 CST 2023] Your cert is in: /root/.acme.sh/gos.naigosto.info_ecc/gos.naigosto.info.cer
[Thu Apr 6 12:51:57 CST 2023] Your cert key is in: /root/.acme.sh/gos.naigosto.info_ecc/gos.naigosto.info.key
[Thu Apr 6 12:51:57 CST 2023] The intermediate CA cert is in: /root/.acme.sh/gos.naigosto.info_ecc/ca.cer
[Thu Apr 6 12:51:57 CST 2023] And the full chain certs is there: /root/.acme.sh/gos.naigosto.info_ecc/fullchain.cer#成功现象
root@iZj6c9jm2xw77w13d79ecbZ:~# acme.sh --issue -d gos.xxx.info --standalone -k ec-256
[Thu Apr 6 12:51:26 CST 2023] Using CA: https://acme.zerossl.com/v2/DV90
[Thu Apr 6 12:51:26 CST 2023] Standalone mode.
[Thu Apr 6 12:51:27 CST 2023] Single domain='gos.naigosto.info'
[Thu Apr 6 12:51:27 CST 2023] Getting domain auth token for each domain
[Thu Apr 6 12:51:31 CST 2023] Getting webroot for domain='gos.naigosto.info'
[Thu Apr 6 12:51:31 CST 2023] Verifying: gos.naigosto.info
[Thu Apr 6 12:51:31 CST 2023] Standalone mode server
[Thu Apr 6 12:51:33 CST 2023] Processing, The CA is processing your order, please just wait. (1/30)
[Thu Apr 6 12:51:37 CST 2023] Success
[Thu Apr 6 12:51:37 CST 2023] Verify finished, start to sign.
[Thu Apr 6 12:51:37 CST 2023] Lets finalize the order.
[Thu Apr 6 12:51:37 CST 2023] Le_OrderFinalize='https://acme.zerossl.com/v2/DV90/order/Mth3kUpt_ANMr3xrfT94sg/finalize'
[Thu Apr 6 12:51:38 CST 2023] Order status is processing, lets sleep and retry.
[Thu Apr 6 12:51:39 CST 2023] Retry after: 15
[Thu Apr 6 12:51:55 CST 2023] Polling order status: https://acme.zerossl.com/v2/DV90/order/Mth3kUpt_ANMr3xrfT94sg
[Thu Apr 6 12:51:56 CST 2023] Downloading cert.
[Thu Apr 6 12:51:56 CST 2023] Le_LinkCert='https://acme.zerossl.com/v2/DV90/cert/2QU0KxSksAAtC7fzQdxzhQ'
[Thu Apr 6 12:51:57 CST 2023] Cert success.
-----BEGIN CERTIFICATE-----
MIIEBjCCA4ygAwIBAgIRAJTDtMaaTte2W7mIXyeoF98wCgYIKoZIzj0EAwMwSzEL
MAkGA1UEBhMCQVQxEDAOBgNVBAoTB1plcm9TU0wxKjAoBgNVBAMTIVplcm9TU0wg
RUNDIERvbWFpbiBTZWN1cmUgU2l0ZSBDQTAeFw0yMzA0MDYwMDAwMDBaFw0yMzA3
MDUyMzU5NTlaMBwxGjAYBgNVBAMTEWdvcy5uYWlnb3N0by5pbmZvMFkwEwYHKoZI
zj0CAQYIKoZIzj0DAQcDQgAEJbby2wcHB6OgwcdU4C+Tyuo7sbqF2oxfmBHUtI5E
sZO+aHfG7SzD+pSUXslAjDZhfr5EEkC4SamRmIcFYAtudqOCAn4wggJ6MB8GA1Ud
IwQYMBaAFA9r5kvOOUeu9n6QHnnwMJGSyF+jMB0GA1UdDgQWBBQs5kJ/z/D88jwS
C/Y7YVenJOKNUjAOBgNVHQ8BAf8EBAMCB4AwDAYDVR0TAQH/BAIwADAdBgNVHSUE
FjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwSQYDVR0gBEIwQDA0BgsrBgEEAbIxAQIC
TjAlMCMGCCsGAQUFBwIBFhdodHRwczovL3NlY3RpZ28uY29tL0NQUzAIBgZngQwB
AgEwgYgGCCsGAQUFBwEBBHwwejBLBggrBgEFBQcwAoY/aHR0cDovL3plcm9zc2wu
Y3J0LnNlY3RpZ28uY29tL1plcm9TU0xFQ0NEb21haW5TZWN1cmVTaXRlQ0EuY3J0
MCsGCCsGAQUFBzABhh9odHRwOi8vemVyb3NzbC5vY3NwLnNlY3RpZ28uY29tMIIB
BQYKKwYBBAHWeQIEAgSB9gSB8wDxAHYArfe++nz/EMiLnT2cHj4YarRnKV3PsQwk
yoWGNOvcgooAAAGHVOfwqgAABAMARzBFAiEAw+MQPi+jYxnPsAFfp0fgqe1qBIqV
a4YAqJbe6tJlgiECIG6k4m75tq0JYa8HuoXfcMvRW+7UUXQG/yGisYqrGRQOAHcA
ejKMVNi3LbYg6jjgUh7phBZwMhOFTTvSK8E6V6NS61IAAAGHVOfw/wAABAMASDBG
AiEA5e/LDLwFIOz0HNLLOu9vHfMM0rHMX9j7/Uy8licGSN4CIQDMdbQ7tune0lCt
VVR+YWesbfLuXP0v6FyNeitVRRrS/jAcBgNVHREEFTATghFnb3MubmFpZ29zdG8u
aW5mbzAKBggqhkjOPQQDAwNoADBlAjBgFji3ea/AxurHp8msibPhPrErnXQkVQLA
OC0YBvVDEzqgY63A+eSHb6nibwE2s1gCMQDaSr20Bm0J1EWm9x42KmY1+gW0k87I
Ii09QL2hunLTMV72jvg22dUBDBSvdvJ0hhM=
-----END CERTIFICATE-----
[Thu Apr 6 12:51:57 CST 2023] Your cert is in: /root/.acme.sh/gos.naigosto.info_ecc/gos.naigosto.info.cer
[Thu Apr 6 12:51:57 CST 2023] Your cert key is in: /root/.acme.sh/gos.naigosto.info_ecc/gos.naigosto.info.key
[Thu Apr 6 12:51:57 CST 2023] The intermediate CA cert is in: /root/.acme.sh/gos.naigosto.info_ecc/ca.cer
[Thu Apr 6 12:51:57 CST 2023] And the full chain certs is there: /root/.acme.sh/gos.naigosto.info_ecc/fullchain.cer浏览器现象
3.2 dns方式
- 获取证书
acme.sh --issue --dns -d *.xxx.infoacme.sh --issue --dns -d *.xxx.info执行后退出,提示有:
Add the following txt record:
Domain:_acme-challenge.xxx.info
Txt value:9ihDbjYfTExAYeDs4DBUeuTo18KBzwvTEjUnSwd32-cAdd the following txt record:
Domain:_acme-challenge.xxx.info
Txt value:9ihDbjYfTExAYeDs4DBUeuTo18KBzwvTEjUnSwd32-c这时,修改DNS记录,增加
_acme-challenge.xxx.info IN TXT "9ihDbjYfTExAYeDs4DBUeuTo18KBzwvTEjUnSwd32-c"_acme-challenge.xxx.info IN TXT "9ihDbjYfTExAYeDs4DBUeuTo18KBzwvTEjUnSwd32-c"然后继续获取证书的过程,注意下面的命令行中的”renew”
./acme.sh --renew -d *.xxx.info./acme.sh --renew -d *.xxx.info4.安装证书
acme.sh --installcert -d domain.com --ecc --key-file /root/trojan/serverkey -fulchain-file /root/trojan/server.crt
acme.sh --installcert -d gos.naigosto.info --ecc --key-file /usr/local/etc/v2ray/server.key --fullchain-file /usr/local/etc/v2ray/server.crtacme.sh --installcert -d gos.naigosto.info --ecc --key-file /usr/local/etc/v2ray/server.key --fullchain-file /usr/local/etc/v2ray/server.crt如果默认CA无法颁发,则可以切换下列CA:
切换 Let's Encrypt: acme.sh --set-default-ca --server letsencrypt
切换 Buypass: acme.sh --setdefault-ca --server buypass
切换 ZeroSSL: acme.sh --set-default-ca --server zerossl (默认)切换 Let's Encrypt: acme.sh --set-default-ca --server letsencrypt
切换 Buypass: acme.sh --setdefault-ca --server buypass
切换 ZeroSSL: acme.sh --set-default-ca --server zerossl (默认)4.1自动升级acme.sh
root@iZj6c9jm2xw77w13d79ecbZ:~# acme.sh --upgrade --auto-upgrade
[Mon May 22 15:40:39 CST 2023] Installing from online archive.
[Mon May 22 15:40:39 CST 2023] Downloading https://github.com/acmesh-official/acme.sh/archive/master.tar.gz
[Mon May 22 15:40:40 CST 2023] Extracting master.tar.gz
[Mon May 22 15:40:41 CST 2023] Installing to /root/.acme.sh
[Mon May 22 15:40:41 CST 2023] Installed to /root/.acme.sh/acme.sh
[Mon May 22 15:40:41 CST 2023] Good, bash is found, so change the shebang to use bash as preferred.
[Mon May 22 15:40:42 CST 2023] OK
[Mon May 22 15:40:42 CST 2023] Install success!
[Mon May 22 15:40:42 CST 2023] Upgrade success!root@iZj6c9jm2xw77w13d79ecbZ:~# acme.sh --upgrade --auto-upgrade
[Mon May 22 15:40:39 CST 2023] Installing from online archive.
[Mon May 22 15:40:39 CST 2023] Downloading https://github.com/acmesh-official/acme.sh/archive/master.tar.gz
[Mon May 22 15:40:40 CST 2023] Extracting master.tar.gz
[Mon May 22 15:40:41 CST 2023] Installing to /root/.acme.sh
[Mon May 22 15:40:41 CST 2023] Installed to /root/.acme.sh/acme.sh
[Mon May 22 15:40:41 CST 2023] Good, bash is found, so change the shebang to use bash as preferred.
[Mon May 22 15:40:42 CST 2023] OK
[Mon May 22 15:40:42 CST 2023] Install success!
[Mon May 22 15:40:42 CST 2023] Upgrade success!4.2更新证书
目前证书在 60 天以后会自动更新,你无需任何操作,因为在acme.sh安装时,已经把相关的自动更新程序写入到crontab中,如果想要查看,可以通过以下命令
crontab -lcrontab -l4.3停止自动更新证书
acme.sh --remove -d example.comacme.sh --remove -d example.com或者手动在~/.acme.sh/目录下删除对应的域名目录,如~/.acme.sh/a.com
4.4手动
# 颁发泛域名证书
acme.sh --issue -d '*.xxx.com' --dns --yes-I-know-dns-manual-mode-enough-go-ahead-please
# 按提示在DNS解析上增加TXT_VALUE等值,等待生效
# 使用dig查看是否生效
dig -t txt _acme-challenge.xxx.com @8.8.8.8
# renew,重新颁发
acme.sh --renew -d *.xxx.com \
--yes-I-know-dns-manual-mode-enough-go-ahead-please
# 重新install即可
acme.sh --install-cert -d *.xxx.com \
--key-file /etc/nginx/conf.d/ssl/common.xxx.com.key.pem \
--fullchain-file /etc/nginx/conf.d/ssl/common.xxx.com.cert.pem \
--reloadcmd "systemctl restart nginx"# 颁发泛域名证书
acme.sh --issue -d '*.xxx.com' --dns --yes-I-know-dns-manual-mode-enough-go-ahead-please
# 按提示在DNS解析上增加TXT_VALUE等值,等待生效
# 使用dig查看是否生效
dig -t txt _acme-challenge.xxx.com @8.8.8.8
# renew,重新颁发
acme.sh --renew -d *.xxx.com \
--yes-I-know-dns-manual-mode-enough-go-ahead-please
# 重新install即可
acme.sh --install-cert -d *.xxx.com \
--key-file /etc/nginx/conf.d/ssl/common.xxx.com.key.pem \
--fullchain-file /etc/nginx/conf.d/ssl/common.xxx.com.cert.pem \
--reloadcmd "systemctl restart nginx"5.服务端配置
5.0安装
https://github.com/v2fly/fhs-install-v2ray
// 安裝執行檔和 .dat 資料檔
# bash <(curl -L https://raw.githubusercontent.com/v2fly/fhs-install-v2ray/master/install-release.sh)https://github.com/v2fly/fhs-install-v2ray
// 安裝執行檔和 .dat 資料檔
# bash <(curl -L https://raw.githubusercontent.com/v2fly/fhs-install-v2ray/master/install-release.sh)5.1vmess+tls
uuid生成
cat /proc/sys/kernel/random/uuidcat /proc/sys/kernel/random/uuidvim config.json
{
"inbounds": [
{
"port":8388,
"protocol":"vmess",
"settings": {
"clients": [
{
"id":"5eeb28d6-d439-11ed-afa1-0242ac120002",
"alterId":0
}
]
},
"streamSettings": {
"network":"tcp",
"security":"tls",
"tlsSettings": {
"certificates": [
{
"certificateFile":"/usr/local/etc/v2ray/server.crt",
"keyFile":"/usr/local/etc/v2ray/server.key"
}
]
}
}
}
],
"outbounds": [
{
"protocol":"freedom",
"settings": {}
}
]
}{
"inbounds": [
{
"port":8388,
"protocol":"vmess",
"settings": {
"clients": [
{
"id":"5eeb28d6-d439-11ed-afa1-0242ac120002",
"alterId":0
}
]
},
"streamSettings": {
"network":"tcp",
"security":"tls",
"tlsSettings": {
"certificates": [
{
"certificateFile":"/usr/local/etc/v2ray/server.crt",
"keyFile":"/usr/local/etc/v2ray/server.key"
}
]
}
}
}
],
"outbounds": [
{
"protocol":"freedom",
"settings": {}
}
]
}- 验证语法是否有问题
/usr/local/bin/v2ray test -c /usr/local/etc/v2ray/config.json
V2Ray 5.3.0 (V2Fly, a community-driven edition of V2Ray.) Custom (go1.20 linux/amd64)
A unified platform for anti-censorship.
Configuration OK./usr/local/bin/v2ray test -c /usr/local/etc/v2ray/config.json
V2Ray 5.3.0 (V2Fly, a community-driven edition of V2Ray.) Custom (go1.20 linux/amd64)
A unified platform for anti-censorship.
Configuration OK.5.2vmess_tls_web
vim nginx.conf
http {
##
# Basic Settings
##
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
server_tokens off;
include /etc/nginx/mime.types;
default_type application/octet-stream;
access_log /var/log/nginx/access.log;
error_log /var/log/nginx/error.log;
gzip on;
server {
listen 443 ssl;
listen [::]:443 ssl;
server_name gos.xxx.info;
ssl_certificate /etc/nginx/ssl/server.crt;
ssl_certificate_key /etc/nginx/ssl/server.key;
ssl_session_timeout 1d;
ssl_session_cache shared:MozSSL:10m;
ssl_session_tickets off;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers 'EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH';
ssl_prefer_server_ciphers off;
location / {
proxy_pass https://nextcloud.com; #伪装网址
proxy_redirect off;
proxy_ssl_server_name on;
sub_filter_once off;
sub_filter "nextcloud.com" $server_name;
proxy_set_header Host "nextcloud.com";
proxy_set_header Referer $http_referer;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header User-Agent $http_user_agent;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto https;
proxy_set_header Accept-Encoding "";
proxy_set_header Accept-Language "zh-CN";
}
location /goray {
if ($http_upgrade != "websocket") {
return 404;
}
proxy_redirect off;
proxy_pass http://127.0.0.1:8388;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
server {
listen 80;
server_name gos.naigosto.info;
location / {
rewrite ^(.*)$ https://$host$1 permanent;
}
}
}http {
##
# Basic Settings
##
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
server_tokens off;
include /etc/nginx/mime.types;
default_type application/octet-stream;
access_log /var/log/nginx/access.log;
error_log /var/log/nginx/error.log;
gzip on;
server {
listen 443 ssl;
listen [::]:443 ssl;
server_name gos.xxx.info;
ssl_certificate /etc/nginx/ssl/server.crt;
ssl_certificate_key /etc/nginx/ssl/server.key;
ssl_session_timeout 1d;
ssl_session_cache shared:MozSSL:10m;
ssl_session_tickets off;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers 'EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH';
ssl_prefer_server_ciphers off;
location / {
proxy_pass https://nextcloud.com; #伪装网址
proxy_redirect off;
proxy_ssl_server_name on;
sub_filter_once off;
sub_filter "nextcloud.com" $server_name;
proxy_set_header Host "nextcloud.com";
proxy_set_header Referer $http_referer;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header User-Agent $http_user_agent;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto https;
proxy_set_header Accept-Encoding "";
proxy_set_header Accept-Language "zh-CN";
}
location /goray {
if ($http_upgrade != "websocket") {
return 404;
}
proxy_redirect off;
proxy_pass http://127.0.0.1:8388;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
server {
listen 80;
server_name gos.naigosto.info;
location / {
rewrite ^(.*)$ https://$host$1 permanent;
}
}
}cdn方式
http {
##
# Basic Settings
##
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
server_tokens off;
include /etc/nginx/mime.types;
default_type application/octet-stream;
access_log /var/log/nginx/access.log;
error_log /var/log/nginx/error.log;
gzip on;
server {
listen 80;
listen 443 ssl;
server_name gos.xxx.info;
ssl_certificate /etc/nginx/ssl/server.crt;
ssl_certificate_key /etc/nginx/ssl/server.key;
ssl_protocols TLSv1 TLSv1.2 TLSv1.3;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
ssl_prefer_server_ciphers off;
ssl_session_timeout 1d;
ssl_session_cache shared:MozSSL:20m;
ssl_session_tickets off;
location / {
proxy_pass https://nextcloud.com; #伪装网址
proxy_redirect off;
proxy_ssl_server_name on;
sub_filter_once off;
sub_filter "nextcloud.com" $server_name;
proxy_set_header Host "nextcloud.com";
proxy_set_header Referer $http_referer;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header User-Agent $http_user_agent;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto https;
proxy_set_header Accept-Encoding "";
proxy_set_header Accept-Language "zh-CN";
}
location /goray {
proxy_redirect off;
proxy_pass http://127.0.0.1:8388;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
}http {
##
# Basic Settings
##
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
server_tokens off;
include /etc/nginx/mime.types;
default_type application/octet-stream;
access_log /var/log/nginx/access.log;
error_log /var/log/nginx/error.log;
gzip on;
server {
listen 80;
listen 443 ssl;
server_name gos.xxx.info;
ssl_certificate /etc/nginx/ssl/server.crt;
ssl_certificate_key /etc/nginx/ssl/server.key;
ssl_protocols TLSv1 TLSv1.2 TLSv1.3;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
ssl_prefer_server_ciphers off;
ssl_session_timeout 1d;
ssl_session_cache shared:MozSSL:20m;
ssl_session_tickets off;
location / {
proxy_pass https://nextcloud.com; #伪装网址
proxy_redirect off;
proxy_ssl_server_name on;
sub_filter_once off;
sub_filter "nextcloud.com" $server_name;
proxy_set_header Host "nextcloud.com";
proxy_set_header Referer $http_referer;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header User-Agent $http_user_agent;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto https;
proxy_set_header Accept-Encoding "";
proxy_set_header Accept-Language "zh-CN";
}
location /goray {
proxy_redirect off;
proxy_pass http://127.0.0.1:8388;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
}vim config.json
{
"inbounds": [
{
"listen":"127.0.0.1",
"port":8388,
"protocol":"vmess",
"settings": {
"clients": [
{
"id":"5eeb28d6-d439-11ed-afa1-0242ac120002",
"alterId":0
}
]
},
"streamSettings": {
"network":"ws",
"wsSettings":{
"path":"/goray"
}
}
}
],
"outbounds": [
{
"protocol":"freedom",
"settings": {}
}
]
}{
"inbounds": [
{
"listen":"127.0.0.1",
"port":8388,
"protocol":"vmess",
"settings": {
"clients": [
{
"id":"5eeb28d6-d439-11ed-afa1-0242ac120002",
"alterId":0
}
]
},
"streamSettings": {
"network":"ws",
"wsSettings":{
"path":"/goray"
}
}
}
],
"outbounds": [
{
"protocol":"freedom",
"settings": {}
}
]
}6. client端下载
https://github.com/2dust/v2rayN
伪站的选择
伪装网站的选择
使用VPS自建Xray代理在流量的常见特征有 单点性 、 大流量性 、 长时间性 、 GO-TLS指纹特性 、 出入相同性 等。
- 单点性 指使用的人少,一般只有自己,即使分享给朋友,一般也不会太多。
- 长时间性 不单指时间长,也指坚持一个月或一年每天都使用代理。
- GO-TLS指纹特性 在不伪装浏览器指纹的前提下,从TLS握手信息中可以判断出客户端是GO程序,详见此处。
- 出入相同性 指入VPS和出VPS的流量在时间和大小上几乎相同,比如使用Xray代理浏览
BiliBili,从BiliBili到VPS(Xray服务端)的流量,和从VPS到Xray客户端的流量在时间上和大小上是几乎相同的。出入相同性 是所有代理的通病,目前还没有太好的伪装方法,但是因为VPS不在大陆,如果不是被特别关注的对象,一般不会被审查。
既然使用Xray进行代理的全部流量都将伪装成访问这个网站的流量,那么我们选择伪装网站就是要尽量选择流量特征与Xray代理的流量特征相同的网站。
- Cloudreve 和 Nextcloud
他们都是个人网盘,个人网盘可以理解为使用自己的VPS搭建起来的百度网盘,区别就是文件都存放在VPS中,并且自己是网盘的管理员。
个人网盘与上面所说特征的吻合数最多,包括 单点性 、 大流量性 、 GO-TLS指纹特性 、 长时间性 等,建议选择。
关于GO-TLS指纹特性,在不伪装浏览器指纹的前提下,将alpn设置为http/1.1,可以伪装成GO语言实现的WebDav客户端,详见此处。
线上
user www-data;
worker_processes auto;
pid /run/nginx.pid;
include /etc/nginx/modules-enabled/*.conf;
events {
worker_connections 768;
# multi_accept on;
}
http {
##
# Basic Settings
##
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
server_tokens off;
include /etc/nginx/mime.types;
default_type application/octet-stream;
access_log /var/log/nginx/access.log;
error_log /var/log/nginx/error.log;
gzip on;
server {
listen 80;
listen 443 ssl;
server_name nais.xxx.info;
ssl_certificate /usr/local/etc/v2ray/server.crt;
ssl_certificate_key /usr/local/etc/v2ray/server.key;
ssl_protocols TLSv1 TLSv1.2 TLSv1.3;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
ssl_prefer_server_ciphers off;
ssl_session_timeout 1d;
ssl_session_cache shared:MozSSL:20m;
ssl_session_tickets off;
location / {
proxy_pass https://nextcloud.com; #伪装网址
proxy_redirect off;
proxy_ssl_server_name on;
sub_filter_once off;
sub_filter "nextcloud.com" $server_name;
proxy_set_header Host "nextcloud.com";
proxy_set_header Referer $http_referer;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header User-Agent $http_user_agent;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto https;
proxy_set_header Accept-Encoding "";
proxy_set_header Accept-Language "zh-CN";
}
location /goray {
proxy_redirect off;
proxy_pass http://127.0.0.1:8388;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
#server {
# listen 80;
# server_name gos.naigosto.info;
# rewrite ^(.*)$ https://$host$1 permanent;
#}
}user www-data;
worker_processes auto;
pid /run/nginx.pid;
include /etc/nginx/modules-enabled/*.conf;
events {
worker_connections 768;
# multi_accept on;
}
http {
##
# Basic Settings
##
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
server_tokens off;
include /etc/nginx/mime.types;
default_type application/octet-stream;
access_log /var/log/nginx/access.log;
error_log /var/log/nginx/error.log;
gzip on;
server {
listen 80;
listen 443 ssl;
server_name nais.xxx.info;
ssl_certificate /usr/local/etc/v2ray/server.crt;
ssl_certificate_key /usr/local/etc/v2ray/server.key;
ssl_protocols TLSv1 TLSv1.2 TLSv1.3;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
ssl_prefer_server_ciphers off;
ssl_session_timeout 1d;
ssl_session_cache shared:MozSSL:20m;
ssl_session_tickets off;
location / {
proxy_pass https://nextcloud.com; #伪装网址
proxy_redirect off;
proxy_ssl_server_name on;
sub_filter_once off;
sub_filter "nextcloud.com" $server_name;
proxy_set_header Host "nextcloud.com";
proxy_set_header Referer $http_referer;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header User-Agent $http_user_agent;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto https;
proxy_set_header Accept-Encoding "";
proxy_set_header Accept-Language "zh-CN";
}
location /goray {
proxy_redirect off;
proxy_pass http://127.0.0.1:8388;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
#server {
# listen 80;
# server_name gos.naigosto.info;
# rewrite ^(.*)$ https://$host$1 permanent;
#}
}