- ubuntu20.04
- openvpn2.4
- freeradius3.6.0
- privacyIDEA 3.6.3
- 172.18.106.134----->radius
- 172.18.106.135----->openvpn
1.介绍
RSA提供了完整的身份认证解决方案,特别是RSA SecurID双因素身份认证解决方案,已成为该领域的事实标准,该解决方案以易于实现、成熟、可靠等特点在信息安全领域赢得广泛信赖。RSA的产品覆盖 也非常的广,除了传统的硬件token设备,也有在智能设备上使用的软token,非常方便
但是对于中小型公司来讲,使用RSA这种商用身份认证解决方案成本高昂。往往因为IT预算不足限制了企业对双因素方案的选择
Google Authenticator项目是可用于多手机平台的生成一次性密码的软件实现,包含可插拔验证模块(PAM)的实现。通过使用开放标准的 Initiative for Open Authentication (OATH,与OAuth不同)来生成一次性密码。支持RFC 4226文档定义的基于HMAC的一次性密码(HOTP)算法和由 RFC 6238文档定义的基于时间的一次性密码 (TOTP)算法。
随着google-authenticator的成熟,使用openvpn和双因素认证系统结合,让搭建完全基于开源软件的安全远程接入系统成为可能。
OpenVPN是一个用于创建虚拟专用网络(Virtual Private Network)加密通道的免费开源软件。使用OpenVPN可以方便地在家庭、办公场所、住宿酒店等不同网络访问场所之间搭建类似于局域网的专用网络通道。
在PAM中使用Google Authenticator,提供双因素认证已经实现。但是管理维护非常麻烦,也不直观。用户必须是系统账户,用户修改pin码或者生成新的token需 要登陆系统,执行命令,对于小白用户的使用有些困难,登录系统也会有潜在的安全风险。对于管理员来讲,不能使用公司现有的账户系统,需要在认证系统上创建 管理另一套账户系统。
PrivacyIDEA是一个模块化的认证系统,认证服务器。使用privacyIDEA可以增强本地登录,VPN,远程访问,SSH连接,在认证 期间访问网站或门户网站是很好使用的双因素,提高现有应用程序的安全性。它最初被用于OTP(一次性密码),认证设备来作为一个OTP服务器。但其他的 “设备”之类的挑战响应,SSH密钥和X509证书也可提供。它可以运行在Linux系统并且是完全开源的。
PrivacyIDEA有着友好的管理界面。无论是管理员管理系统还是用户自管理,都可以非常方便轻松的在Web上完成操作。PrivacyIDEA可以读取本地文件中的用户、数据库中的用户,也可以读取LDAP中的用户。这样就可以完全和公司的账户系统联动,非常方便
PrivacyIDEA的HOTP、TOTP使用Google Authenticator。这样,我们在智能手机上的使用Google Authenticator的APP将非常方便。
PrivacyIDEA提供了三种方式和OpenVPN集成。第一种,使用PAM的privacyidea_pam.py模块。OpneVPN使用 PAM认证,PAM调用privacyidea_pam.py模块和PrivacyIDEA做验证。第二种,直接集成OpenVPN和 FreeRADIUS。OpenVPN使用radius认证,FreeRADIUS向PrivacyIDEA验证。第三种,在OpenVPN中使用 RADIUS的PAM模块
2.方案
OpenVPN+FreeRADIUS+PrivacyIDEA
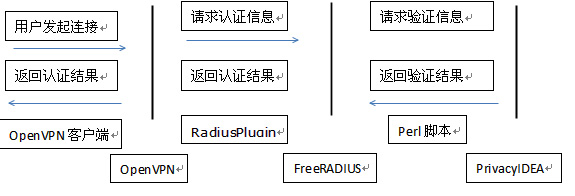
首先远端用户发起VPN连接,提供认证信息。然后,OpenVPN向FreeRADIUS去做认证并提供用户认证信息。接 着,FreeRADIUS通过perl脚本向PrivacyIDEA验证信息正确与否。然后,PrivacyIDEA将验证结果发给 FreeRADIUS,FreeRADIUS再将认证结果发送OpenvVPN。最后,OpenvVPN查看结果,认证成功建立连接。如果认证失败,断开 连接,发送失败信息
3.privacyIDEA
Add repository
apt update
apt install software-properties-common
wget https://lancelot.netknights.it/NetKnights-Release.asc
gpg --import --import-options show-only --with-fingerprint NetKnights-Release.asc
add-apt-repository http://lancelot.netknights.it/community/focal/stableapt update
apt install software-properties-common
wget https://lancelot.netknights.it/NetKnights-Release.asc
gpg --import --import-options show-only --with-fingerprint NetKnights-Release.asc
add-apt-repository http://lancelot.netknights.it/community/focal/stableInstallation of privacyIDEA 3.x
#apt install privacyidea-apache2
#或者nginx
#privacyidea-nginx#apt install privacyidea-apache2
#或者nginx
#privacyidea-nginx配置管理员用户
pi-manage admin add admin -e admin@freehan.inkpi-manage admin add admin -e admin@freehan.ink登录
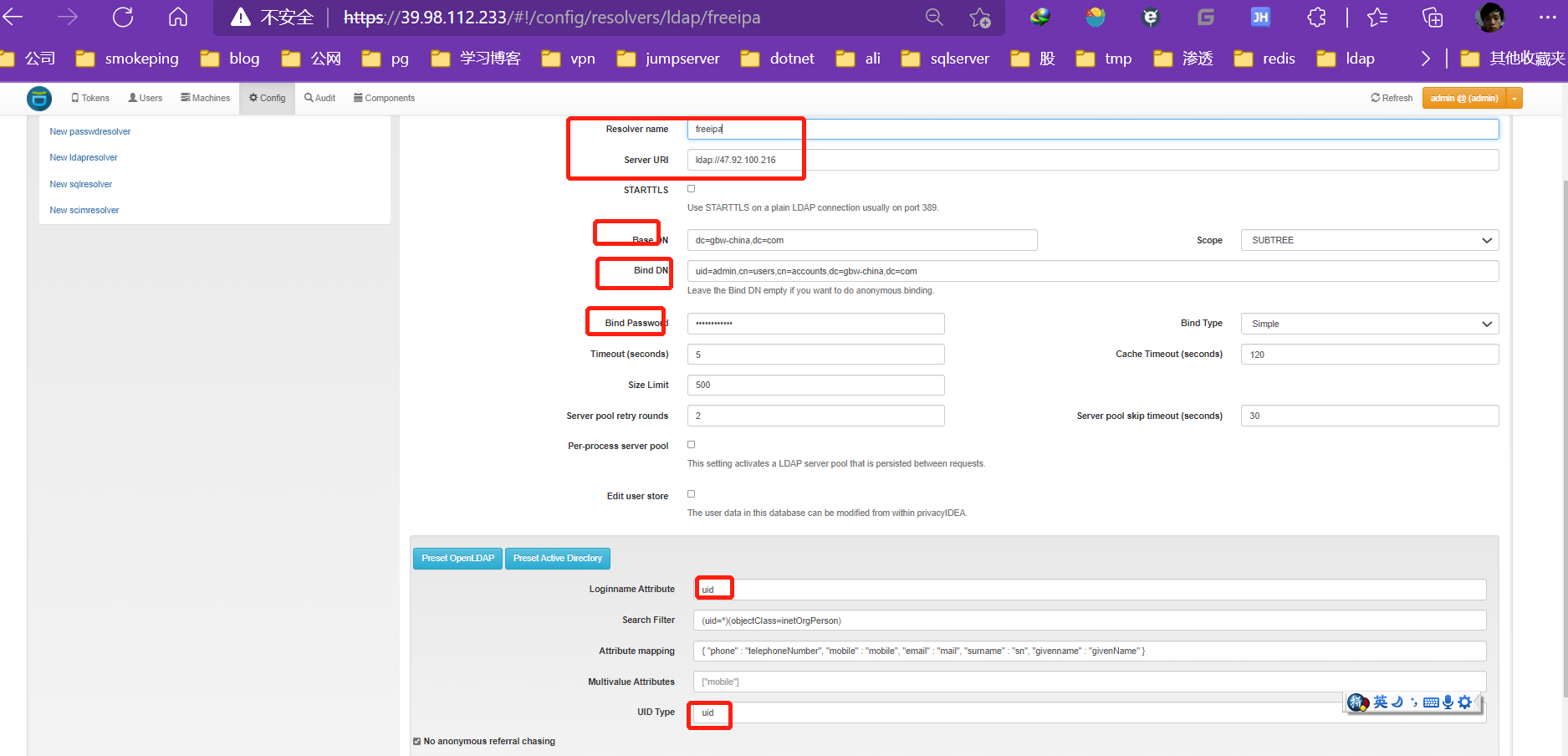
配置ldap
4.FreeRADIUS
apt-get install freeradius privacyidea-radius freeradius-rest freeradius-utilsapt-get install freeradius privacyidea-radius freeradius-rest freeradius-utils- 官方文档
https://privacyidea.readthedocs.io/en/latest/installation/ubuntu.html#add-ubuntu-repository
配置rlm_rest
cp /etc/freeradius/3.0/mods-available/rest{,.old}
ln -vs /etc/freeradius/3.0/mods-available/rest /etc/freeradius/3.0/mods-enabled/restcp /etc/freeradius/3.0/mods-available/rest{,.old}
ln -vs /etc/freeradius/3.0/mods-available/rest /etc/freeradius/3.0/mods-enabled/restvim rest
#修改3处地方,如下
connect_uri = "https://172.18.106.134"
authenticate
uri = "${..connect_uri}/validate/radiuscheck"
method = 'post'
body = 'post'
data = "user=%{urlquote:%{User-Name}}&pass=%{urlquote:%{User-Password}}"
force_to = 'plain'
tls = ${..tls}
}
#添加detail
accounting {
。。。
detail
}vim rest
#修改3处地方,如下
connect_uri = "https://172.18.106.134"
authenticate
uri = "${..connect_uri}/validate/radiuscheck"
method = 'post'
body = 'post'
data = "user=%{urlquote:%{User-Name}}&pass=%{urlquote:%{User-Password}}"
force_to = 'plain'
tls = ${..tls}
}
#添加detail
accounting {
。。。
detail
}配置users
vi /etc/freeradius/3.0/users
#末尾添加
DEFAULT Auth-Type := restvi /etc/freeradius/3.0/users
#末尾添加
DEFAULT Auth-Type := rest配置clients.conf
#egrep -v "#|^$" /etc/freeradius/3.0/clients.conf
#本地测试验证
client localhost {
ipaddr = 172.18.106.134
proto = *
secret = testing123
require_message_authenticator = no
limit {
max_connections = 16
lifetime = 0
idle_timeout = 30
}
}
client localhost_ipv6 {
ipv6addr = ::1
secret = testing123
}
#openvpn验证
client openvpn {
ipaddr = 0.0.0.0/0
proto = *
secret = testing123
require_message_authenticator = no
nastype = other
limit {
max_connections = 1000
lifetime = 0
idle_timeout = 30
}
}#egrep -v "#|^$" /etc/freeradius/3.0/clients.conf
#本地测试验证
client localhost {
ipaddr = 172.18.106.134
proto = *
secret = testing123
require_message_authenticator = no
limit {
max_connections = 16
lifetime = 0
idle_timeout = 30
}
}
client localhost_ipv6 {
ipv6addr = ::1
secret = testing123
}
#openvpn验证
client openvpn {
ipaddr = 0.0.0.0/0
proto = *
secret = testing123
require_message_authenticator = no
nastype = other
limit {
max_connections = 1000
lifetime = 0
idle_timeout = 30
}
}配置rlm_perl.ini
root@radius:/etc/privacyidea# egrep -v "#|^$" rlm_perl.ini
[Default]
URL = https://172.18.106.134/validate/check
SSL_CHECK = false
DEBUG = true
[Mapping]
[Mapping user]
[Attribute Filter-Id]
[Attribute otherAttribute]
[Attribute Class]root@radius:/etc/privacyidea# egrep -v "#|^$" rlm_perl.ini
[Default]
URL = https://172.18.106.134/validate/check
SSL_CHECK = false
DEBUG = true
[Mapping]
[Mapping user]
[Attribute Filter-Id]
[Attribute otherAttribute]
[Attribute Class]配置privacyidea
root@radius:/etc/freeradius/3.0# egrep -v "#|^$" sites-enabled/privacyidea
server {
accounting {
detail
}
authorize {
update request {
Packet-Src-IP-Address = "%{Packet-Src-IP-Address}"
}
perl-privacyidea
if (ok || updated) {
update control {
Auth-Type := Perl
}
}
digest
unix
}
listen {
type = auth
ipaddr = *
port = 0
}
authenticate {
Auth-Type rest {
rest
}
digest
Auth-Type Perl {
perl-privacyidea
}
}
}root@radius:/etc/freeradius/3.0# egrep -v "#|^$" sites-enabled/privacyidea
server {
accounting {
detail
}
authorize {
update request {
Packet-Src-IP-Address = "%{Packet-Src-IP-Address}"
}
perl-privacyidea
if (ok || updated) {
update control {
Auth-Type := Perl
}
}
digest
unix
}
listen {
type = auth
ipaddr = *
port = 0
}
authenticate {
Auth-Type rest {
rest
}
digest
Auth-Type Perl {
perl-privacyidea
}
}
}配置token

测试
root@radius:/etc/privacyidea#freeradius -X
root@radius:/etc/privacyidea# echo "User-Name=han, User-Password=PIN+OTP" | radclient -sx 172.18.106.134 auth testing123
Sent Access-Request Id 154 from 0.0.0.0:57117 to 172.18.106.134:1812 length 68
User-Name = "han"
User-Password = "han123449104"
Cleartext-Password = "han123449104"
Received Access-Accept Id 154 from 172.18.106.134:1812 to 172.18.106.134:57117 length 48
Reply-Message = "privacyIDEA access granted"
Packet summary:
Accepted : 1
Rejected : 0
Lost : 0
Passed filter : 1
Failed filter : 0
#提示如上信息说明成功root@radius:/etc/privacyidea#freeradius -X
root@radius:/etc/privacyidea# echo "User-Name=han, User-Password=PIN+OTP" | radclient -sx 172.18.106.134 auth testing123
Sent Access-Request Id 154 from 0.0.0.0:57117 to 172.18.106.134:1812 length 68
User-Name = "han"
User-Password = "han123449104"
Cleartext-Password = "han123449104"
Received Access-Accept Id 154 from 172.18.106.134:1812 to 172.18.106.134:57117 length 48
Reply-Message = "privacyIDEA access granted"
Packet summary:
Accepted : 1
Rejected : 0
Lost : 0
Passed filter : 1
Failed filter : 0
#提示如上信息说明成功5.配置openvpn
安装radiusplugin
- 下载radiusplugin
wget http://www.nongnu.org/radiusplugin/radiusplugin_v2.1a_beta1.tar.gzwget http://www.nongnu.org/radiusplugin/radiusplugin_v2.1a_beta1.tar.gz- 安装依赖
yum install gcc gcc-c++ libgcrypt*yum install gcc gcc-c++ libgcrypt*- 编译
tarzxvf radiusplugin_v2.1a_beta1.tar.gz
cd radiusplugin_v2.1a_beta1
make
cp radiusplugin.so /etc/openvpn
cp radiusplugin.cnf /etc/openvpntarzxvf radiusplugin_v2.1a_beta1.tar.gz
cd radiusplugin_v2.1a_beta1
make
cp radiusplugin.so /etc/openvpn
cp radiusplugin.cnf /etc/openvpn配置radiusplugin.cnf
[root@vpn openvpn]# cat radiusplugin.cnf
NAS-Identifier=other
Service-Type=5
Framed-Protocol=1
NAS-Port-Type=5
NAS-IP-Address=172.18.106.135
OpenVPNConfig=/etc/openvpn/server/server.conf
subnet=255.255.255.0
overwriteccfiles=true
nonfatalaccounting=true
server
{
acctport=1813
authport=1812
name=172.18.106.134
retry=1
wait=2
sharedsecret=testing123
}[root@vpn openvpn]# cat radiusplugin.cnf
NAS-Identifier=other
Service-Type=5
Framed-Protocol=1
NAS-Port-Type=5
NAS-IP-Address=172.18.106.135
OpenVPNConfig=/etc/openvpn/server/server.conf
subnet=255.255.255.0
overwriteccfiles=true
nonfatalaccounting=true
server
{
acctport=1813
authport=1812
name=172.18.106.134
retry=1
wait=2
sharedsecret=testing123
}配置vpn
server端
port 10020
proto tcp
dev tun
tun-mtu 9000
sndbuf 393216
rcvbuf 393216
ca ca.crt
cert server.crt
key server.key
dh dh.pem
cipher AES-256-CBC
auth SHA512
tls-auth ta.key 0
topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 114.114.114.114"
push "dhcp-option DNS 1.1.1.1"
push "sndbuf 393216"
push "rcvbuf 393216"
route 192.168.1.0 255.255.255.0
push "route 172.18.106.133 255.255.255.0"
client-to-client
verify-client-cert
keepalive 10 120
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
log-append openvpn.log
verb 3
crl-verify crl.pem
mute 20
max-clients 100
plugin /etc/openvpn/radiusplugin.so /etc/openvpn/radiusplugin.cnf
client-cert-not-required
username-as-common-name
reneg-sec 36000port 10020
proto tcp
dev tun
tun-mtu 9000
sndbuf 393216
rcvbuf 393216
ca ca.crt
cert server.crt
key server.key
dh dh.pem
cipher AES-256-CBC
auth SHA512
tls-auth ta.key 0
topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 114.114.114.114"
push "dhcp-option DNS 1.1.1.1"
push "sndbuf 393216"
push "rcvbuf 393216"
route 192.168.1.0 255.255.255.0
push "route 172.18.106.133 255.255.255.0"
client-to-client
verify-client-cert
keepalive 10 120
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
log-append openvpn.log
verb 3
crl-verify crl.pem
mute 20
max-clients 100
plugin /etc/openvpn/radiusplugin.so /etc/openvpn/radiusplugin.cnf
client-cert-not-required
username-as-common-name
reneg-sec 36000client端
client
dev tun
proto tcp
tun-mtu 9000
sndbuf 393216
rcvbuf 393216
remote 39.99.129.148 10020
resolv-retry infinite
nobind
persist-key
persist-tun
remote-cert-tls server
auth SHA512
cipher AES-256-CBC
setenv opt block-outside-dns
key-direction 1
verb 3
auth-nocache
route-method exe
route-delay 2
auth-user-pass
reneg-sec 36000client
dev tun
proto tcp
tun-mtu 9000
sndbuf 393216
rcvbuf 393216
remote 39.99.129.148 10020
resolv-retry infinite
nobind
persist-key
persist-tun
remote-cert-tls server
auth SHA512
cipher AES-256-CBC
setenv opt block-outside-dns
key-direction 1
verb 3
auth-nocache
route-method exe
route-delay 2
auth-user-pass
reneg-sec 36000注意,
ProtectSystem=true
ProtectHome=true -->必须关闭这个ProtectSystem=true
ProtectHome=true -->必须关闭这个