- CentOS 7.x
- OpenVPN 2.4.x
- Google Authenticator libPAM 1.0.1
1.google-authenticator
# 准备打包的软件环境
yum -y install git gcc libtool autoconf automake pam-devel rpm-build qrencode-libs;
# 抓取源代码,打包
git clone https://github.com/google/google-authenticator-libpam.git;
cd google-authenticator-libpam;
./bootstrap.sh;
./configure;
make dist;
mkdir ~/rpmbuild/SOURCES/
cp google-authenticator-*.tar.gz ~/rpmbuild/SOURCES/;
rpmbuild -ba contrib/rpm.spec;
# 成功以后,编好的rpm包路径在:
# ~/rpmbuild/RPMS/x86_64/google-authenticator-1.*.el6.x86_64.rpm
#安装
rpm -vih /root/rpmbuild/RPMS/x86_64/google-authenticator-1.09-1.el7.x86_64.rpm# 准备打包的软件环境
yum -y install git gcc libtool autoconf automake pam-devel rpm-build qrencode-libs;
# 抓取源代码,打包
git clone https://github.com/google/google-authenticator-libpam.git;
cd google-authenticator-libpam;
./bootstrap.sh;
./configure;
make dist;
mkdir ~/rpmbuild/SOURCES/
cp google-authenticator-*.tar.gz ~/rpmbuild/SOURCES/;
rpmbuild -ba contrib/rpm.spec;
# 成功以后,编好的rpm包路径在:
# ~/rpmbuild/RPMS/x86_64/google-authenticator-1.*.el6.x86_64.rpm
#安装
rpm -vih /root/rpmbuild/RPMS/x86_64/google-authenticator-1.09-1.el7.x86_64.rpm2.pamtester
#验证pam是否成功
yum install pamtester -y
#centos8
dnf install pam_ldap openvpn-auth-ldap pamtester#验证pam是否成功
yum install pamtester -y
#centos8
dnf install pam_ldap openvpn-auth-ldap pamtester3.openvpn_server配置
#vi server.conf
port 1194
proto tcp
dev tun
tun-mtu 9000
sndbuf 393216
rcvbuf 393216
ca ca.crt
cert server.crt
key server.key
dh dh.pem
cipher AES-256-CBC
auth SHA512
tls-auth ta.key 0
topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 114.114.114.114"
push "dhcp-option DNS 1.1.1.1"
push "route 172.26.0.0 255.255.255.0"
push "sndbuf 393216"
push "rcvbuf 393216"
verify-client-cert
keepalive 10 120
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
log-append openvpn.log
verb 3
crl-verify crl.pem
mute 20
max-clients 100
plugin /usr/lib64/openvpn/plugins/openvpn-plugin-auth-pam.so openvpn
client-cert-not-required
username-as-common-name
reneg-sec 36000#vi server.conf
port 1194
proto tcp
dev tun
tun-mtu 9000
sndbuf 393216
rcvbuf 393216
ca ca.crt
cert server.crt
key server.key
dh dh.pem
cipher AES-256-CBC
auth SHA512
tls-auth ta.key 0
topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 114.114.114.114"
push "dhcp-option DNS 1.1.1.1"
push "route 172.26.0.0 255.255.255.0"
push "sndbuf 393216"
push "rcvbuf 393216"
verify-client-cert
keepalive 10 120
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
log-append openvpn.log
verb 3
crl-verify crl.pem
mute 20
max-clients 100
plugin /usr/lib64/openvpn/plugins/openvpn-plugin-auth-pam.so openvpn
client-cert-not-required
username-as-common-name
reneg-sec 360004.client配置
client
dev tun
proto tcp
tun-mtu 9000
sndbuf 393216
rcvbuf 393216
remote 39.98.112.233 1194
resolv-retry infinite
nobind
persist-key
persist-tun
remote-cert-tls server
auth SHA512
cipher AES-256-CBC
setenv opt block-outside-dns
key-direction 1
verb 3
auth-nocache
route-method exe
route-delay 2
auth-user-pass
reneg-sec 36000
《证书省。。。》client
dev tun
proto tcp
tun-mtu 9000
sndbuf 393216
rcvbuf 393216
remote 39.98.112.233 1194
resolv-retry infinite
nobind
persist-key
persist-tun
remote-cert-tls server
auth SHA512
cipher AES-256-CBC
setenv opt block-outside-dns
key-direction 1
verb 3
auth-nocache
route-method exe
route-delay 2
auth-user-pass
reneg-sec 36000
《证书省。。。》5.pam配置
#cat /etc/pam.d/openvpn
auth [user_unknown=ignore success=ok ignore=ignore default=bad] pam_securetty.so
auth required /usr/lib64/security/pam_google_authenticator.so secret=/etc/openvpn/google-authenticator/${USER} user=gauth forward_pass
auth include system-auth
account include system-auth
password include system-auth#cat /etc/pam.d/openvpn
auth [user_unknown=ignore success=ok ignore=ignore default=bad] pam_securetty.so
auth required /usr/lib64/security/pam_google_authenticator.so secret=/etc/openvpn/google-authenticator/${USER} user=gauth forward_pass
auth include system-auth
account include system-auth
password include system-auth6.配置google验证
#create user ,用于google验证
useradd gauth
#Create directory to store google authenticator files and change ownership to gauth
mkdir /etc/openvpn/google-authenticator
chown gauth:gauth /etc/openvpn/google-authenticator
chmod 700 /etc/openvpn/google-authenticator#create user ,用于google验证
useradd gauth
#Create directory to store google authenticator files and change ownership to gauth
mkdir /etc/openvpn/google-authenticator
chown gauth:gauth /etc/openvpn/google-authenticator
chmod 700 /etc/openvpn/google-authenticator- Create script file with the content below for the creation of the OTP username
chmod 700 /root/create-gauth.sh
vi create-gauth.sh
#!/bin/sh
# Parse arguments
USERNAME="$1"
if [ -z "$USERNAME" ]; then
echo "Usage: $(basename $0) "
exit 2
fi
# Set the label the user will see when importing the token:
LABEL='OpenVPN Server'
su -c "google-authenticator -t -d -r3 -R30 -W -f -l \"${LABEL}\" -s /etc/openvpn/google-authenticator/${USERNAME}" - gauthchmod 700 /root/create-gauth.sh
vi create-gauth.sh
#!/bin/sh
# Parse arguments
USERNAME="$1"
if [ -z "$USERNAME" ]; then
echo "Usage: $(basename $0) "
exit 2
fi
# Set the label the user will see when importing the token:
LABEL='OpenVPN Server'
su -c "google-authenticator -t -d -r3 -R30 -W -f -l \"${LABEL}\" -s /etc/openvpn/google-authenticator/${USERNAME}" - gauth- Create vpn user with the OS command below
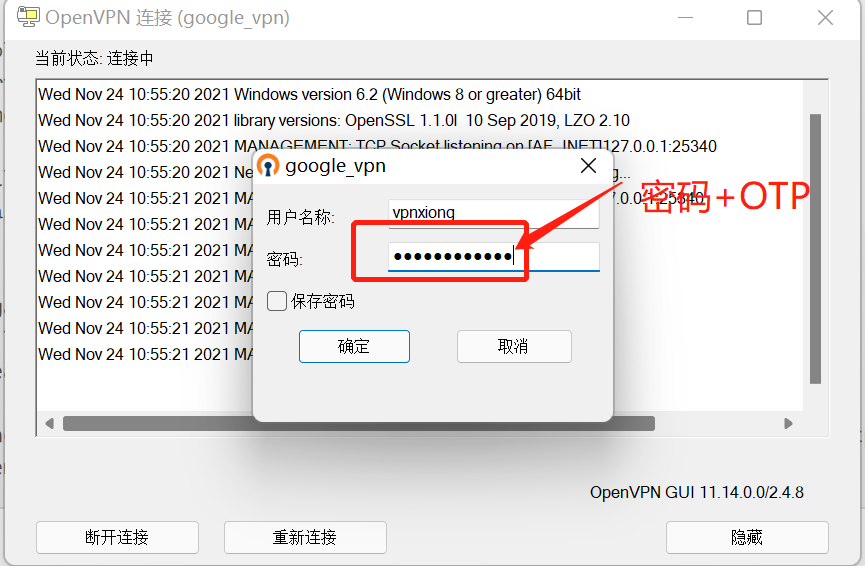
useradd -M -c "google_auth_vpnxiong" -s /sbin/false vpnxiong
passwd vpnxiong
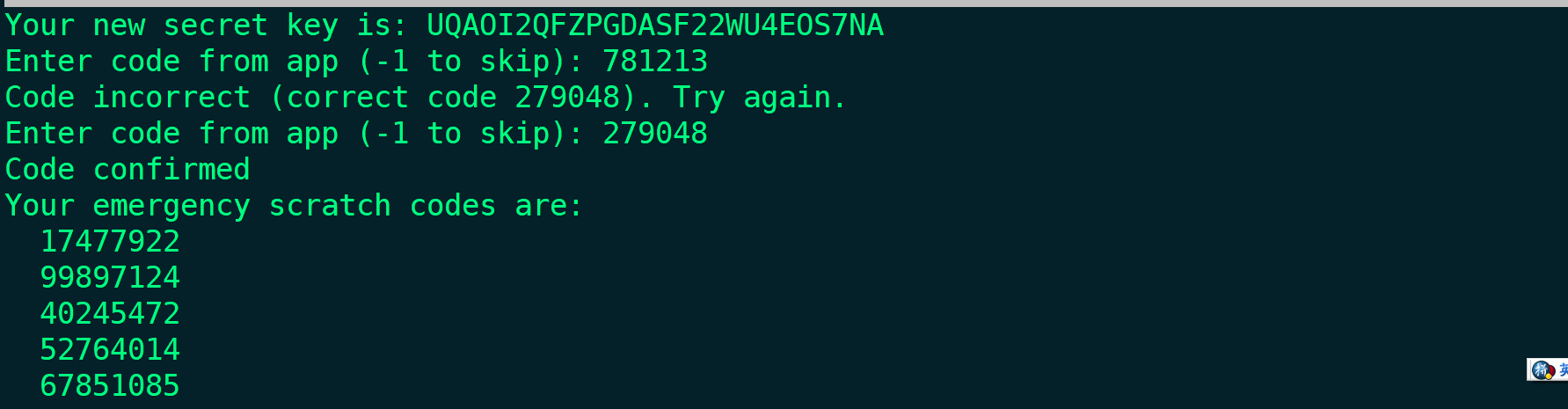
sh create-gauth.sh vpnxionguseradd -M -c "google_auth_vpnxiong" -s /sbin/false vpnxiong
passwd vpnxiong
sh create-gauth.sh vpnxiong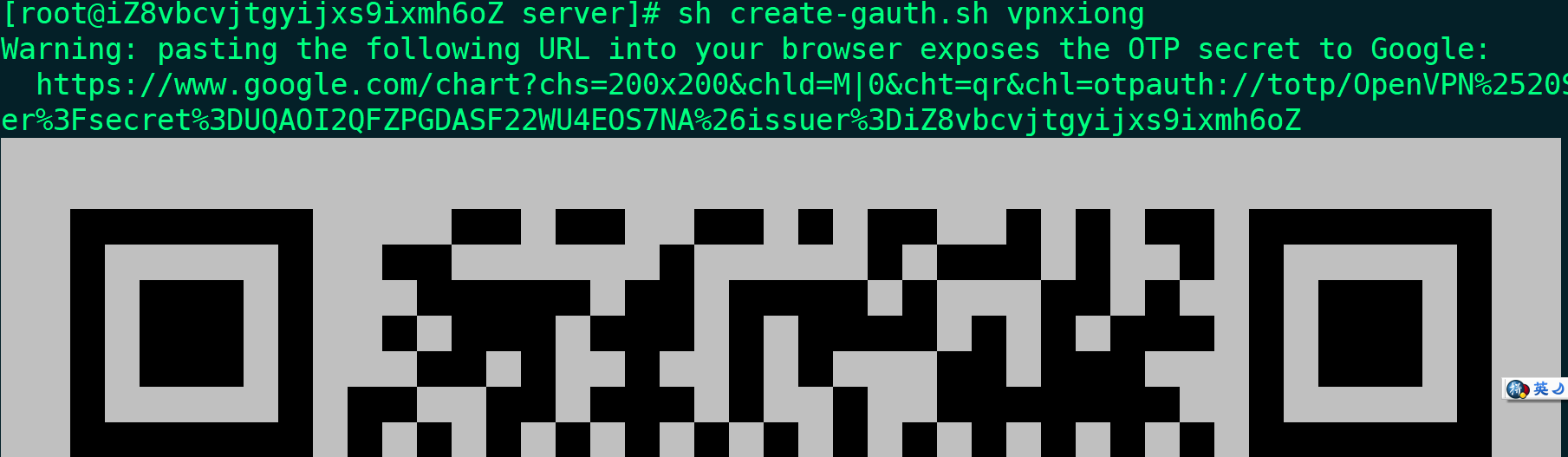
7.pam测试
[root@iZ8vbcvjtgyijxs9ixmh6oZ pam.d]# pamtester openvpn vpnxiong authenticate;
Password & verification code: 密码+google验证
pamtester: successfully authenticated[root@iZ8vbcvjtgyijxs9ixmh6oZ pam.d]# pamtester openvpn vpnxiong authenticate;
Password & verification code: 密码+google验证
pamtester: successfully authenticated8.额外
#vpn 发邮件
vi server.conf
client-connect /etc/openvpn/scripts/up.sh
#chmod 755 /etc/openvpn/scripts/up.sh
#vi /etc/openvpn/scripts/up.sh
#!/bin/bash
smtp="A.B.C.D"
from="vpnadmin@dilli.com.np"
full_name=$(/usr/bin/getent passwd $common_name | /usr/bin/cut -d: -f5 | /usr/bin/awk -F "," '{print $1}')
email_address=$(/usr/bin/getent passwd $common_name | /usr/bin/cut -d: -f5 | /usr/bin/awk -F "," '{print $2}')
subject="VPN connected from $untrusted_ip\nContent-Type: text/html"
date_n_time=$(date +%c)
Message=$(echo "Dear ${full_name},
Your VPN Username $common_name has been connected from IP Address: $untrusted_ip. Make sure it is you or you are aware of it.
Please change your password if it is not you and contact System administrator for further assistance.
Following is the details
==========================================
Connected Since: ${date_n_time}
Public Address: $untrusted_ip
Virtual Address: $ifconfig_pool_remote_ip
Name: $common_name
Full Name: $full_name
Email Address: $email_address
Regards,
IT Team
Idealab.")
echo $Message | /bin/mailx -r ${from} -s "$(echo -e ${subject})" -S smtp="${smtp}" ${email_address}#vpn 发邮件
vi server.conf
client-connect /etc/openvpn/scripts/up.sh
#chmod 755 /etc/openvpn/scripts/up.sh
#vi /etc/openvpn/scripts/up.sh
#!/bin/bash
smtp="A.B.C.D"
from="vpnadmin@dilli.com.np"
full_name=$(/usr/bin/getent passwd $common_name | /usr/bin/cut -d: -f5 | /usr/bin/awk -F "," '{print $1}')
email_address=$(/usr/bin/getent passwd $common_name | /usr/bin/cut -d: -f5 | /usr/bin/awk -F "," '{print $2}')
subject="VPN connected from $untrusted_ip\nContent-Type: text/html"
date_n_time=$(date +%c)
Message=$(echo "Dear ${full_name},
Your VPN Username $common_name has been connected from IP Address: $untrusted_ip. Make sure it is you or you are aware of it.
Please change your password if it is not you and contact System administrator for further assistance.
Following is the details
==========================================
Connected Since: ${date_n_time}
Public Address: $untrusted_ip
Virtual Address: $ifconfig_pool_remote_ip
Name: $common_name
Full Name: $full_name
Email Address: $email_address
Regards,
IT Team
Idealab.")
echo $Message | /bin/mailx -r ${from} -s "$(echo -e ${subject})" -S smtp="${smtp}" ${email_address}- 关闭systemd 保护模式
vi /usr/lib/systemd/system/openvpn-server@.service
[Service]
...
ProtectHome=truevi /usr/lib/systemd/system/openvpn-server@.service
[Service]
...
ProtectHome=true9.测试