- 环境基于centos7.9
- k8s-1.22.x
- ingress-1.4.0
1. Ingress Yaml安装
There are multiple ways to install the Ingress-Nginx Controller:
安装Ingress-nginx控制器;
使⽤daemonSet⽅式部署,但需要通过nodeSelect来选择⼏个节点安装,并⾮所有节点都需要;
将Pod的端⼝与节点共享⽹络名称空间;设定为HostNetwork;
1.1 下载ingress文件
#云
wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.4.0/deploy/static/provider/cloud/deploy.yaml
# 非云环境
https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.4.0/deploy/static/provider/baremetal/deploy.yaml#云
wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.4.0/deploy/static/provider/cloud/deploy.yaml
# 非云环境
https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.4.0/deploy/static/provider/baremetal/deploy.yaml1.2 修改配置
kind: Daemonset #⽤DaemonSet确保每个节点都部署Ingress
type: NodePort
image:
registry.cn-hangzhou.aliyuncs.com/google_containers/nginx-ingress-controller:v1.4.0
registry.cn-zhangjiakou.aliyuncs.com/hsuing/kube-webhook-certgen:v20220916-gd32f8c343
去掉digtest 验证
dnsPolicy: ClusterFirstWithHostNet # 优先使⽤集群内的DNS解析服务
hostNetwork: true # 使⽤主机网络
nodeSelector: ## 节点选择器(选择哪些节点部署Ingress,默认所有)
node-role: ingress ## 如果节点有node-role=ingress 并且os=linux的标签,则在节点上运⾏Ingress Pod
kind: Daemonset #⽤DaemonSet确保每个节点都部署Ingress
type: NodePort
image:
registry.cn-hangzhou.aliyuncs.com/google_containers/nginx-ingress-controller:v1.4.0
registry.cn-zhangjiakou.aliyuncs.com/hsuing/kube-webhook-certgen:v20220916-gd32f8c343
去掉digtest 验证
dnsPolicy: ClusterFirstWithHostNet # 优先使⽤集群内的DNS解析服务
hostNetwork: true # 使⽤主机网络
nodeSelector: ## 节点选择器(选择哪些节点部署Ingress,默认所有)
node-role: ingress ## 如果节点有node-role=ingress 并且os=linux的标签,则在节点上运⾏Ingress Pod1.3 为节点打标签
#查看node
[root@kube-master ingress-nginx]# kubectl get node
NAME STATUS ROLES AGE VERSION
k8s-master01 Ready control-plane,master 40d v1.22.17
kube-node01 Ready <none> 38d v1.22.17
kube-node02 Ready <none> 39d v1.22.17
kube-node03 Ready <none> 39d v1.22.17
#为节点打上对应标签,否则Ingress⽆法正常调度到指定的节点运⾏
[root@kube-master ingress-nginx]# kubectl label nodes kube-node01 node-role=ingress
node/kube-node01 labeled
[root@kube-master ingress-nginx]# kubectl label nodes kube-node02 node-role=ingress
node/kube-node02 labeled#查看node
[root@kube-master ingress-nginx]# kubectl get node
NAME STATUS ROLES AGE VERSION
k8s-master01 Ready control-plane,master 40d v1.22.17
kube-node01 Ready <none> 38d v1.22.17
kube-node02 Ready <none> 39d v1.22.17
kube-node03 Ready <none> 39d v1.22.17
#为节点打上对应标签,否则Ingress⽆法正常调度到指定的节点运⾏
[root@kube-master ingress-nginx]# kubectl label nodes kube-node01 node-role=ingress
node/kube-node01 labeled
[root@kube-master ingress-nginx]# kubectl label nodes kube-node02 node-role=ingress
node/kube-node02 labeled1.4 创建ingress
[root@kube-master ingress-nginx]# kubectl apply -f deploy-1.4.0.yaml
namespace/ingress-nginx unchanged
serviceaccount/ingress-nginx unchanged
serviceaccount/ingress-nginx-admission unchanged
role.rbac.authorization.k8s.io/ingress-nginx unchanged
role.rbac.authorization.k8s.io/ingress-nginx-admission unchanged
clusterrole.rbac.authorization.k8s.io/ingress-nginx unchanged
clusterrole.rbac.authorization.k8s.io/ingress-nginx-admission unchanged
rolebinding.rbac.authorization.k8s.io/ingress-nginx unchanged
rolebinding.rbac.authorization.k8s.io/ingress-nginx-admission unchanged
clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx unchanged
clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx-admission unchanged
configmap/ingress-nginx-controller unchanged
service/ingress-nginx-controller created
service/ingress-nginx-controller-admission unchanged
daemonset.apps/ingress-nginx-controller configured
job.batch/ingress-nginx-admission-create unchanged
job.batch/ingress-nginx-admission-patch unchanged
ingressclass.networking.k8s.io/nginx unchanged
validatingwebhookconfiguration.admissionregistration.k8s.io/ingress-nginx-admission configured[root@kube-master ingress-nginx]# kubectl apply -f deploy-1.4.0.yaml
namespace/ingress-nginx unchanged
serviceaccount/ingress-nginx unchanged
serviceaccount/ingress-nginx-admission unchanged
role.rbac.authorization.k8s.io/ingress-nginx unchanged
role.rbac.authorization.k8s.io/ingress-nginx-admission unchanged
clusterrole.rbac.authorization.k8s.io/ingress-nginx unchanged
clusterrole.rbac.authorization.k8s.io/ingress-nginx-admission unchanged
rolebinding.rbac.authorization.k8s.io/ingress-nginx unchanged
rolebinding.rbac.authorization.k8s.io/ingress-nginx-admission unchanged
clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx unchanged
clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx-admission unchanged
configmap/ingress-nginx-controller unchanged
service/ingress-nginx-controller created
service/ingress-nginx-controller-admission unchanged
daemonset.apps/ingress-nginx-controller configured
job.batch/ingress-nginx-admission-create unchanged
job.batch/ingress-nginx-admission-patch unchanged
ingressclass.networking.k8s.io/nginx unchanged
validatingwebhookconfiguration.admissionregistration.k8s.io/ingress-nginx-admission configured❌ 注意
报错,The Service "ingress-nginx-controller" is invalid: spec.externalTrafficPolicy: Invalid value: "Local": ExternalTrafficPolicy can onlybe set on NodePort and LoadBalancer service
To resolve this issue, you need to make sure that the externalTrafficPolicy field is only set for NodePort or LoadBalancer
- 查看
[root@kube-master ingress]# kubectl get pod,svc,ds -n ingress-nginx
pod/ingress-nginx-admission-create-c799q 0/1 Completed 0 2d1h
pod/ingress-nginx-admission-patch-wzm82 0/1 Completed 0 2d1h
pod/ingress-nginx-controller-gcv4v 1/1 Running 0 3h39m
pod/ingress-nginx-controller-hs58n 1/1 Running 0 3h39m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/ingress-nginx-controller NodePort 192.168.104.132 <none> 80:31592/TCP,443:31125/TCP 2d
service/ingress-nginx-controller-admission ClusterIP 192.168.53.76 <none> 443/TCP 2d1h
NAME DESIRED CURRENT READY UP-TO-DATE AVAILABLE NODE SELECTOR AGE
daemonset.apps/ingress-nginx-controller 2 2 2 2 2 kubernetes.io/os=linux,node-role=ingress 2d1h[root@kube-master ingress]# kubectl get pod,svc,ds -n ingress-nginx
pod/ingress-nginx-admission-create-c799q 0/1 Completed 0 2d1h
pod/ingress-nginx-admission-patch-wzm82 0/1 Completed 0 2d1h
pod/ingress-nginx-controller-gcv4v 1/1 Running 0 3h39m
pod/ingress-nginx-controller-hs58n 1/1 Running 0 3h39m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/ingress-nginx-controller NodePort 192.168.104.132 <none> 80:31592/TCP,443:31125/TCP 2d
service/ingress-nginx-controller-admission ClusterIP 192.168.53.76 <none> 443/TCP 2d1h
NAME DESIRED CURRENT READY UP-TO-DATE AVAILABLE NODE SELECTOR AGE
daemonset.apps/ingress-nginx-controller 2 2 2 2 2 kubernetes.io/os=linux,node-role=ingress 2d1h- pod介绍
ingress-nginx-controllerService:这个Service负责将请求转发到ingress-nginx-controller Pods。它通常会将流量分发到ingress-nginx-controller的多个副本中,并确保副本集的负载平衡。这个Service可以被配置为使用NodePort、LoadBalancer或ClusterlP类型,根据需要进行暴露。
ingress-nginx-controller-admissionService:用于检查和验证Ingress中定义的规则和设置是否正确。它可以确保在创建、更新或删除Ingress资源时,所有必需的配置项都已正确设置,并防止不正确的配置影响到您的应用程序的运行。此服务还可以执行一些自动化的操作,例如生成TLs证书并将其与相应的Ingress资源关联,以确保通过Ingress的所有流量都以加密的方式传输。该Service也可以被配置为使用NodePort、LoadBalancer或ClusterlP类型,根据需要进行暴露。
2. Ingress Controller的暴露方式
当使用k8s中的Ingress资源对象来暴露应用时,用户访问应用的入口是IngressController 的地址。
Ingress Controller会根据Ingress 规则将请求路由到相应的服务,并将服务的响应返回给客户端。
要把Ingress Controller暴露出去暴露方式有以下几种:
NodePort:使用 NodePort 服务类型来暴露Ingress Controller,这种方式可以将Ingress Controller 暴露到长uibernetes 集群的所有节点上,通过节点的IP地址和NodePort 可以访问到Ipgress Controller。
- 优点:比较简单,易于配置和管理
- 缺点:需要暴露每个节点的端口,容易造成端口泛滥,不易于后续管理,或者在安全方面存在一些隐患。
LoadBalancer(推荐):使用LoadBalancer服务类型来暴露IngressController,这种方式可以将IngressController暴露到云服务提供商的负载均衡器上,从而可以通过负载均衡器的IP地址来访问IngressController。可以实现更好的负载均衡和高可用性。
- 优点:可以自动创建负载均衡器,可以动态地分配IP地址,易于管理和扩展
- 缺点:需要依赖云尺商提供的负载均衡器服务,对于一些不支持负载均衡器服务的云平台或者本地环境不太适用
案例
创建deployment yaml文件
[root@kube-master ingress]# cat dp.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-dm
spec:
selector:
matchLabels:
name: nginx
replicas: 2
template:
metadata:
labels:
name: nginx
spec:
containers:
- name: nginx
image: registry.cn-zhangjiakou.aliyuncs.com/hsuing/demoapp:v1
imagePullPolicy: IfNotPresent
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: nginx-svc
spec:
type: NodePort
ports:
- port: 80
targetPort: 80
protocol: TCP
selector:
name: nginx[root@kube-master ingress]# cat dp.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-dm
spec:
selector:
matchLabels:
name: nginx
replicas: 2
template:
metadata:
labels:
name: nginx
spec:
containers:
- name: nginx
image: registry.cn-zhangjiakou.aliyuncs.com/hsuing/demoapp:v1
imagePullPolicy: IfNotPresent
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: nginx-svc
spec:
type: NodePort
ports:
- port: 80
targetPort: 80
protocol: TCP
selector:
name: nginx- 创建
[root@kube-master ingress]# kubectl apply -f dp.yaml
deployment.apps/nginx-dm created[root@kube-master ingress]# kubectl apply -f dp.yaml
deployment.apps/nginx-dm created- 查看
[root@kube-master ingress]# kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
nginx-svc NodePort 192.168.26.95 <none> 80/TCP 10s[root@kube-master ingress]# kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
nginx-svc NodePort 192.168.26.95 <none> 80/TCP 10s创建ingres文件
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: my-ingress
spec:
ingressClassName: "nginx"
rules:
- host: my.host.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx-svc
port:
number: 80apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: my-ingress
spec:
ingressClassName: "nginx"
rules:
- host: my.host.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx-svc
port:
number: 80- 创建
[root@kube-master ingress]# kubectl apply -f ingres-nginx.yaml
ingress.networking.k8s.io/my-ingress created[root@kube-master ingress]# kubectl apply -f ingres-nginx.yaml
ingress.networking.k8s.io/my-ingress created- 查看
[root@kube-master ingress]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
my-ingress nginx my.host.com 192.168.104.132 80 105s[root@kube-master ingress]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
my-ingress nginx my.host.com 192.168.104.132 80 105s- 客户端测试
配置windows,C:\Windows\System32\drivers\etc,将域名解析安装了Ingress节点的地址,然后测试访问
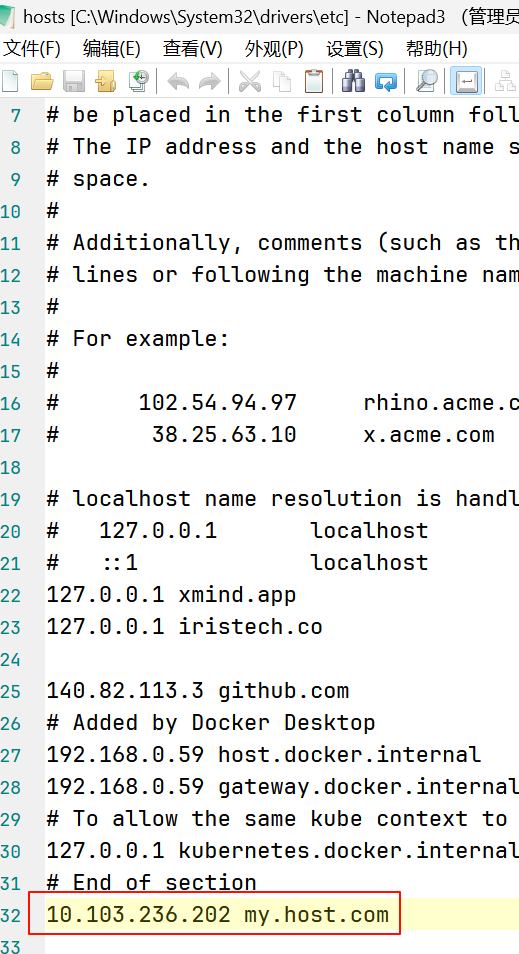
- 查看效果
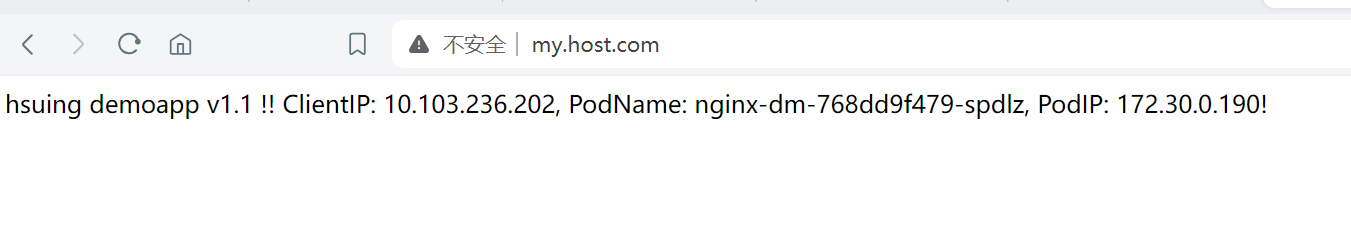
视频
https://www.taohui.tech/2021/05/17/k8s/在线课程:K8S-Ingress-Controller技术细节探讨/