- centos7_x86
- privacyIDEA 3.3.1
- apache
- mariadb-5.5
- python2.7
官方文档
- ldap配置
https://privacyidea.readthedocs.io/en/latest/configuration/useridresolvers.html#ldap-resolver
- 安装
https://privacyidea.readthedocs.io/en/latest/installation/centos.html
git clone https://github.com/privacyidea/privacyidea.gitgit clone https://github.com/privacyidea/privacyidea.git1.privacyIDEA的介绍
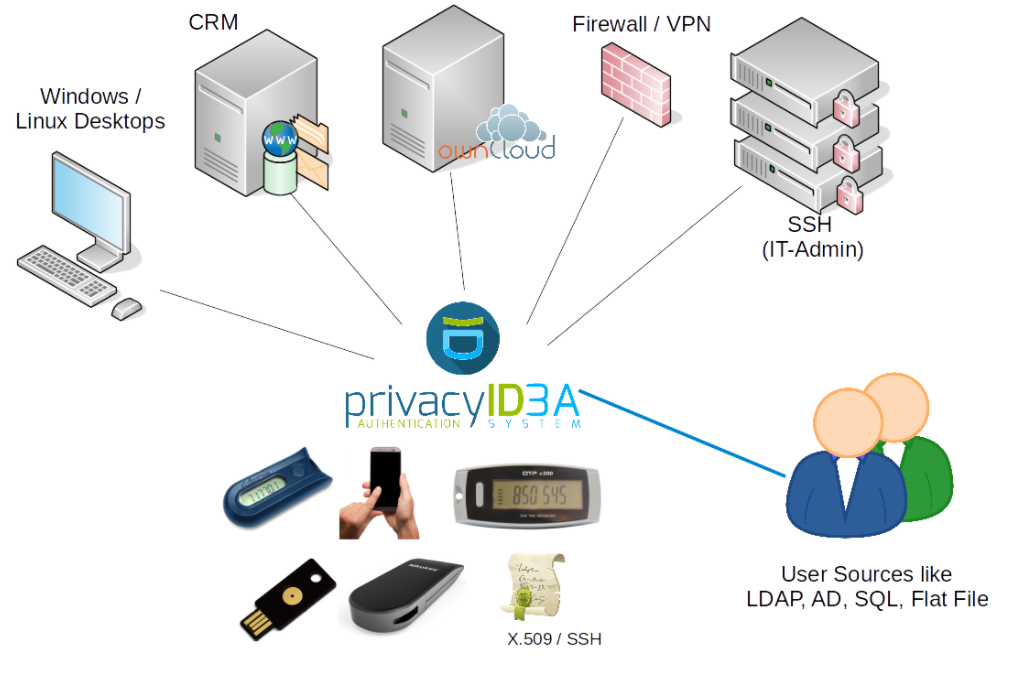
privacyIDEA是什么
– 模块化的身份验证服务器
– 可通过双因素身份验证来增强应用程序的安全
privacyIDEA的作用
– 可增强本地登录的安全性
– 可增强VPN的安全性
– 可增强远程访问的安全性
– 可增强SSH连接的安全性
– 可增强访问网站或Web门户网站的安全性
注,
privacyIDEA最初有如下作用,
– 作为OTP服务器的提供OTP(一次性密码)认证设备
– 也可用户其他设备的Challenge Response、U2F、Yubikeys、SSH秘钥和x509证书
软件特点
– 运行于Linux系统
– 完全开源,基于AGPLv3的许可发布
– 系统由Python语言编写
– 使用Flask的Web框架
– 使用SQL数据库作为数据存储
支持的用户来源
– LDAP服务
– Active Directory
– SQL数据库
– 平面文件
– SCIM服务
privacyIDEA的功能
支持的认证设备
– Simple pass token,即简单的令牌传递(实际总回应ACCEPTED)
– HOTP/TOTP,支持的品牌有SafeNet/eToken Pass、Safeword、Feitian、Smartdisplayer(所有OATH令牌)
– Push-Button key fobs,即按钮式密码卡
– OTP cards,即One-time Password或称动态口令
– Smartphone Apps,如Google Authenticator或FreeOTP
– MOTP,即移动密码系统
– QR code,即通过扫描QR码验证TiQR令牌
– RADIUS token,即将身份验证请求转发给RADIUS服务器
– REMOTE token,即将身份验证请求转发给别的privacyIDEA服务器
– Email-Token,即通过电子邮件发送的一次性密码
– SMS-Token,即通过短信发送一次性密码(SMSOTP,mTAN,mobileTAN)
– Yubikey in all Modes,即Yubikey的所有模式,包括OATH HOTP、Challenge Response、Yubico AES
– Day OTP token,即通过一天使用一个密码并在第二天更改令牌的密码的验证设备
– Password token,即将OTP PIN与附加密码的组合,适用于内部丢失令牌的场景
– SSH public key,即SSH令牌包含公共的SSH秘钥,此SSH秘钥可分发到计算机用于SSH登录
– x509 certificates,即由证书颁发机构颁发的x509证书
– Registration Token,即注册令牌,便于部署
– python class inherited from TokenClass,即从TokenClass继承的新Python类来添加新的身份验证设备
支持的认证接口
– 支持REST API(符合RESTful设计架构的接口)和JWT(JSON Web Token)身份验证
– 支持返回JSON输出
– 支持与SimpleSAMLphp一起充当SAML身份提供程序
– 插件可用于,
– – FreeRADIUS
– – PAM(支持离线OTP)
– – Apache2
– – OTRS
– – Django
– – ownCloud
– – WordPress
– – TYPO3
– – Contao
– – dokuwiki等等
支持的登录方式
– 用户或管理员可以登录privacyIDEA WebUI
– 用户或管理员可针对其他用户(例如域密码)或针对privacyIDEA(使用OTP)进行身份验证
支持的管理
– 支持创建解析器和领域
– 支持查看审核日志
– 支持管理令牌,具体是注册或删除、分配或取消分配、设置PIN、导入、启用或禁用、重新同步令牌、查看令牌详情
– 支持获取特定的令牌OTP值
– 支持获取特定OTP值的令牌序列号
– 支持定义令牌默认设置
– 支持令牌有效期
– 支持令牌最大使用量(根据每天或单个令牌的使用计数,例如可限制10此成功登录或20此尝试登录,或多少周内有效)
– 支持创建丢失的令牌,即将临时令牌注册给丢失令牌的用户
– 支持定义策略
– 支持通过RADIUS侧列进行简单迁移
– 支持定义根据任何的操作定义任何操作
支持的自助服务
– 支持用户可通过WebUI自行管理自己的令牌
– 支持通过QR码(Google身份验证器)、通过种子或令牌的序列号注册新令牌
– 支持删除、禁用、启用和设置PIN
– 支持查看与用户相关的账号、令牌的审核日志
支持的用户来源
– 支持用户的来源有,平面文件、SQL数据库、LDAP、openLDAP、Active Directory或其他LDAP服务器或SCIM服务器
– 支持根据SQL用户表定义设置,有些程序包含预定义配置,如WordPress、OTRS、onwCloud和Tine 2.0
– 支持根据LDAP目录定义设置,有些程序包含预定义配置,如openLDAP和Active Directory
– 支持将一个领域组合到另外一个领域,privacyIDEA可管理无限个领域
– 支持在SQL用户存储中增删改查privacyIDEA用户
支持的策略
– 支持详细的行为配置(由复杂的策略模块支持)
– 支持为令牌管理、系统配置、自助服务、身份验证、授权 、注册和审核定义策略
– 支持针对某些用户、领域、管理员、管理员操作、请求的客户端、请求令牌的类型等使用策略
– 支持管理范围策略,如定义管理界面中允许管理员执行的操作(每个操作)
– 支持系统范围策略,如定义允许那个管理员配置privacyIDEA
– 支持自助服务范围策略,如定义允许用户在自助服务门户中使用它的令牌执行操作(定制从本地网络或因特网登录权限不同)
– 支持身份验证范围策略,如定义要求用户使用OTP值以外的OTP PIN登录或额外使用LDAP密码登陆
– 支持授权范围策略,如定义需要某些类型的令牌或序列号登录
– 支持注册范围策略,如定义允许用户分配的令牌数或领域包含的令牌数或注册期间的随机OTP PIN或OTP PIN强度
– 支持审计范围,如定义允许那个管理严查看审计日志
– 支持导入和导出、启用或禁用策略
支持的事件处理程序
– 支持响应事件的电子邮件通知
– 支持定义已处理事件不会更改原始行为
– 支持通过简单的模块设置增强时间处理
支持的审计
– 详细的审计日志存储到SQL数据库
– 审计条目经过数据签名和检查以防止删除(防篡改)
– 审计日志会跟踪事件状态、事件触发者、涉及的令牌、请求的客户端、执行的privacyIDEA服务器以及其他详细信息
支持的机器和应用
– 支持定义客户端的计算机
– 支持定义应用程序的类型(SSH、PAM、LUKS),支持分配令牌到计算机的那些程序、支持脱机身份验证
支持的数据库
– SQLite
– MySQL
– PostgreSQL
– Oracle
– DB2
注:令牌秘钥数据库中使用AES加密
2.安装
yum install mariadb-server httpd mod_wsgi mod_ssl python-virtualenv policycoreutils-python mysql-devel
yum install -y python-devel openjpeg-devel openldap-devel libffi-devel freetype-devel freeradius-perl libpng-devel postgresql-devel perl-libwww-perl perl-Config-IniFiles perl-Try-Tiny perl-Data-Dump perl-JSON perl-LWP-Protocol-https
yum install -y libxslt-devel libxml2-devel
yum install gcc postgresql-devel -yyum install mariadb-server httpd mod_wsgi mod_ssl python-virtualenv policycoreutils-python mysql-devel
yum install -y python-devel openjpeg-devel openldap-devel libffi-devel freetype-devel freeradius-perl libpng-devel postgresql-devel perl-libwww-perl perl-Config-IniFiles perl-Try-Tiny perl-Data-Dump perl-JSON perl-LWP-Protocol-https
yum install -y libxslt-devel libxml2-devel
yum install gcc postgresql-devel -y- 配置ulimit
cat > /etc/security/limits.d/20-nproc.conf <<'EOF'
# Default limit for number of user's processes to prevent
# accidental fork bombs.
# See rhbz #432903 for reasoning.
#nproc
* soft nproc 65535
root soft nproc unlimited
* hard nproc 65535
root hard nproc unlimited
#nofile
* soft nofile 65535
* hard nofile 65535
EOF
#或者
# 修改systemd系统级ulimit
cat >> /etc/systemd/system.conf <<'EOF'
DefaultLimitCORE=infinity
DefaultLimitNOFILE=100000
DefaultLimitNPROC=100000
EOF
# 修改systemd用户级ulimit
cat >> /etc/systemd/user.conf <<'EOF'
DefaultLimitCORE=infinity
DefaultLimitNOFILE=100000
DefaultLimitNPROC=100000
EOF
systemctl daemon-reload
#查看
ulimit -a|egrep 'open files|max user processes'cat > /etc/security/limits.d/20-nproc.conf <<'EOF'
# Default limit for number of user's processes to prevent
# accidental fork bombs.
# See rhbz #432903 for reasoning.
#nproc
* soft nproc 65535
root soft nproc unlimited
* hard nproc 65535
root hard nproc unlimited
#nofile
* soft nofile 65535
* hard nofile 65535
EOF
#或者
# 修改systemd系统级ulimit
cat >> /etc/systemd/system.conf <<'EOF'
DefaultLimitCORE=infinity
DefaultLimitNOFILE=100000
DefaultLimitNPROC=100000
EOF
# 修改systemd用户级ulimit
cat >> /etc/systemd/user.conf <<'EOF'
DefaultLimitCORE=infinity
DefaultLimitNOFILE=100000
DefaultLimitNPROC=100000
EOF
systemctl daemon-reload
#查看
ulimit -a|egrep 'open files|max user processes'配置名称解析
cat /etc/hosts
172.18.106.132 privacyidea privacyidea.freehan.ink freehan.inkcat /etc/hosts
172.18.106.132 privacyidea privacyidea.freehan.ink freehan.ink关闭selinux
setenforce 0
sed -i 's/SELINUX=enforcing/SELINUX=disabled/g' /etc/selinux/configsetenforce 0
sed -i 's/SELINUX=enforcing/SELINUX=disabled/g' /etc/selinux/config配置ntp服务与时区
yum install -y chrony
#启动服务并配置自启动
systemctl start chronyd.service
systemctl enable chronyd.service
注:如果内网有NTP服务器,请根据实际情况修改如下配置,
grep server /etc/chrony.conf
需要修改的参数如下,
server 0.centos.pool.ntp.org iburst
server 1.centos.pool.ntp.org iburst
server 2.centos.pool.ntp.org iburst
server 3.centos.pool.ntp.org iburst
配置时区,
timedatectl set-timezone Asia/Shanghaiyum install -y chrony
#启动服务并配置自启动
systemctl start chronyd.service
systemctl enable chronyd.service
注:如果内网有NTP服务器,请根据实际情况修改如下配置,
grep server /etc/chrony.conf
需要修改的参数如下,
server 0.centos.pool.ntp.org iburst
server 1.centos.pool.ntp.org iburst
server 2.centos.pool.ntp.org iburst
server 3.centos.pool.ntp.org iburst
配置时区,
timedatectl set-timezone Asia/Shanghai配置防火墙
firewall-cmd --permanent --add-service=http --add-service=https
firewall-cmd --reload
firewall-cmd --list-allfirewall-cmd --permanent --add-service=http --add-service=https
firewall-cmd --reload
firewall-cmd --list-all部署开发环境
yum groupinstall -y 'Development Tools'yum groupinstall -y 'Development Tools'$ systemctl enable --now httpd
$ systemctl enable --now mariadb
$systemctl start mariadb.service
$systemctl enable mariadb.service
#初始化数据库
$ mysql_secure_installation
[...]
Enter current password for root (enter for none):
[...]
Set root password? [Y/n] y
New password:******
Re-enter new password:******
[...]
Remove anonymous users? [Y/n] y
[...]
Disallow root login remotely? [Y/n] n
[...]
Remove test database and access to it? [Y/n] y
[...]
Reload privilege tables now? [Y/n] y
[...]$ systemctl enable --now httpd
$ systemctl enable --now mariadb
$systemctl start mariadb.service
$systemctl enable mariadb.service
#初始化数据库
$ mysql_secure_installation
[...]
Enter current password for root (enter for none):
[...]
Set root password? [Y/n] y
New password:******
Re-enter new password:******
[...]
Remove anonymous users? [Y/n] y
[...]
Disallow root login remotely? [Y/n] n
[...]
Remove test database and access to it? [Y/n] y
[...]
Reload privilege tables now? [Y/n] y
[...]配置idea数据库
echo 'create database privacyidea;' | mysql -u root -p
echo 'create user "pi"@"localhost" identified by "privacyideapwd";' | mysql -u root -p
echo 'grant all privileges on privacyidea.* to "privacyidea"@"localhost" identified by "privacyideapwd";' | mysql -u root -p
#测试你的配置
mysql -uprivacyidea -pprivacyideapwdecho 'create database privacyidea;' | mysql -u root -p
echo 'create user "pi"@"localhost" identified by "privacyideapwd";' | mysql -u root -p
echo 'grant all privileges on privacyidea.* to "privacyidea"@"localhost" identified by "privacyideapwd";' | mysql -u root -p
#测试你的配置
mysql -uprivacyidea -pprivacyideapwd配置目录
$ mkdir /etc/privacyidea
$ mkdir /opt/privacyidea
$ mkdir /var/log/privacyidea$ mkdir /etc/privacyidea
$ mkdir /opt/privacyidea
$ mkdir /var/log/privacyidea配置用户
$ useradd -r -M -d /opt/privacyidea privacyidea
$ chown privacyidea:privacyidea /opt/privacyidea /etc/privacyidea /var/log/privacyidea$ useradd -r -M -d /opt/privacyidea privacyidea
$ chown privacyidea:privacyidea /opt/privacyidea /etc/privacyidea /var/log/privacyidea安装
$ su - privacyidea
#Create the virtual environment
$ virtualenv /opt/privacyidea
#activate
$ . /opt/privacyidea/bin/activate
#update pip
(privacyidea)$ pip install -U pip setuptools
#install
(privacyidea)$ export PI_VERSION=3.3.1
(privacyidea)$ pip install -r https://raw.githubusercontent.com/privacyidea/privacyidea/v${PI_VERSION}/requirements.txt
(privacyidea)$pip install MySQL-python
# install the targeted privacyIDEA
(privacyidea)$ pip install privacyidea==${PI_VERSION}$ su - privacyidea
#Create the virtual environment
$ virtualenv /opt/privacyidea
#activate
$ . /opt/privacyidea/bin/activate
#update pip
(privacyidea)$ pip install -U pip setuptools
#install
(privacyidea)$ export PI_VERSION=3.3.1
(privacyidea)$ pip install -r https://raw.githubusercontent.com/privacyidea/privacyidea/v${PI_VERSION}/requirements.txt
(privacyidea)$pip install MySQL-python
# install the targeted privacyIDEA
(privacyidea)$ pip install privacyidea==${PI_VERSION}配置privacyIDEA
(privacyidea)$vim /etc/privacyidea/pi.cfg
# The realm, where users are allowed to login as administrators
SUPERUSER_REALM = ['super', 'administrators']
# Your database
SQLALCHEMY_DATABASE_URI = 'mysql://privacyidea:privacyideapwd@localhost/privacyidea'
# This is used to encrypt the auth_token
SECRET_KEY = 't0p s3cr3t'
# This is used to encrypt the admin passwords
PI_PEPPER = "Never know..."
# This is used to encrypt the token data and token passwords
PI_ENCFILE = '/etc/privacyidea/enckey'
# This is used to sign the audit log
PI_AUDIT_KEY_PRIVATE = '/etc/privacyidea/private.pem'
PI_AUDIT_KEY_PUBLIC = '/etc/privacyidea/public.pem'
PI_LOGFILE = '/var/log/privacyidea/privacyidea.log'
# PI_LOGLEVEL = 20
# PI_INIT_CHECK_HOOK = 'your.module.function'
#
(privacyidea)$ chmod 640 /etc/privacyidea/pi.cfg
# a new PI_PEPPER and SECRET_KEY must be generated
(privacyidea)$ PEPPER="$(tr -dc A-Za-z0-9_ </dev/urandom | head -c24)"
(privacyidea)$ echo "PI_PEPPER = '$PEPPER'" >> /etc/privacyidea/pi.cfg
(privacyidea)$ SECRET="$(tr -dc A-Za-z0-9_ </dev/urandom | head -c24)"
(privacyidea)$ echo "SECRET_KEY = '$SECRET'" >> /etc/privacyidea/pi.cfg
#pi-manage-tool
(privacyidea)$ pi-manage create_enckey # encryption key for the database
(privacyidea)$ pi-manage create_audit_keys # key for verification of audit log entries
(privacyidea)$ pi-manage createdb # create the database structure(privacyidea)$vim /etc/privacyidea/pi.cfg
# The realm, where users are allowed to login as administrators
SUPERUSER_REALM = ['super', 'administrators']
# Your database
SQLALCHEMY_DATABASE_URI = 'mysql://privacyidea:privacyideapwd@localhost/privacyidea'
# This is used to encrypt the auth_token
SECRET_KEY = 't0p s3cr3t'
# This is used to encrypt the admin passwords
PI_PEPPER = "Never know..."
# This is used to encrypt the token data and token passwords
PI_ENCFILE = '/etc/privacyidea/enckey'
# This is used to sign the audit log
PI_AUDIT_KEY_PRIVATE = '/etc/privacyidea/private.pem'
PI_AUDIT_KEY_PUBLIC = '/etc/privacyidea/public.pem'
PI_LOGFILE = '/var/log/privacyidea/privacyidea.log'
# PI_LOGLEVEL = 20
# PI_INIT_CHECK_HOOK = 'your.module.function'
#
(privacyidea)$ chmod 640 /etc/privacyidea/pi.cfg
# a new PI_PEPPER and SECRET_KEY must be generated
(privacyidea)$ PEPPER="$(tr -dc A-Za-z0-9_ </dev/urandom | head -c24)"
(privacyidea)$ echo "PI_PEPPER = '$PEPPER'" >> /etc/privacyidea/pi.cfg
(privacyidea)$ SECRET="$(tr -dc A-Za-z0-9_ </dev/urandom | head -c24)"
(privacyidea)$ echo "SECRET_KEY = '$SECRET'" >> /etc/privacyidea/pi.cfg
#pi-manage-tool
(privacyidea)$ pi-manage create_enckey # encryption key for the database
(privacyidea)$ pi-manage create_audit_keys # key for verification of audit log entries
(privacyidea)$ pi-manage createdb # create the database structure配置密码
pi-manage admin add admin -e admin@localhost
#测试服务
(privacyidea) -bash-4.2$ pi-manage runserver -h 0.0.0.0 -p 8080
___ ____(_) _____ _______ __/ _/ _ \/ __/ _ |
/ _ \/ __/ / |/ / _ `/ __/ // // // // / _// __ |
/ .__/_/ /_/|___/\_,_/\__/\_, /___/____/___/_/ |_|
/_/ /___/
* Serving Flask app "privacyidea.app" (lazy loading)
* Environment: production
WARNING: This is a development server. Do not use it in a production deployment.
Use a production WSGI server instead.
* Debug mode: off
* Running on http://0.0.0.0:8080/ (Press CTRL+C to quit)pi-manage admin add admin -e admin@localhost
#测试服务
(privacyidea) -bash-4.2$ pi-manage runserver -h 0.0.0.0 -p 8080
___ ____(_) _____ _______ __/ _/ _ \/ __/ _ |
/ _ \/ __/ / |/ / _ `/ __/ // // // // / _// __ |
/ .__/_/ /_/|___/\_,_/\__/\_, /___/____/___/_/ |_|
/_/ /___/
* Serving Flask app "privacyidea.app" (lazy loading)
* Environment: production
WARNING: This is a development server. Do not use it in a production deployment.
Use a production WSGI server instead.
* Debug mode: off
* Running on http://0.0.0.0:8080/ (Press CTRL+C to quit)- 访问
配置apache
#退出privacyidea
$ semanage fcontext -a -t httpd_sys_rw_content_t "/var/log/privacyidea(/.*)?"
$ restorecon -R /var/log/privacyidea
$ setsebool -P httpd_can_network_connect_db 1
$ setsebool -P httpd_can_connect_ldap 1#退出privacyidea
$ semanage fcontext -a -t httpd_sys_rw_content_t "/var/log/privacyidea(/.*)?"
$ restorecon -R /var/log/privacyidea
$ setsebool -P httpd_can_network_connect_db 1
$ setsebool -P httpd_can_connect_ldap 1配置权限
chown -R privacyidea:root /etc/privacyidea
/opt/privacyidea/bin/privacyidea-fix-access-rights -f /etc/privacyidea/pi.cfg -u privacyidea
chmod 400 /etc/privacyidea/enckey
chmod 400 /etc/privacyidea/*.pem
chown -R privacyidea:root /var/log/privacyideachown -R privacyidea:root /etc/privacyidea
/opt/privacyidea/bin/privacyidea-fix-access-rights -f /etc/privacyidea/pi.cfg -u privacyidea
chmod 400 /etc/privacyidea/enckey
chmod 400 /etc/privacyidea/*.pem
chown -R privacyidea:root /var/log/privacyideawsgi的配置文件
mkdir -p /var/run/wsgi
cp /opt/privacyidea/etc/privacyidea/privacyideaapp.wsgi /etc/privacyidea
mv /etc/httpd/conf.d/welcome.conf /etc/httpd/conf.d/welcome.conf.disabled
# chown -R privacyidea:root /var/run/wsgi
[root@iZ8vbcvjtgyijxs9ixmh6oZ conf.d]# vi /etc/httpd/conf.d/privacyidea.confmkdir -p /var/run/wsgi
cp /opt/privacyidea/etc/privacyidea/privacyideaapp.wsgi /etc/privacyidea
mv /etc/httpd/conf.d/welcome.conf /etc/httpd/conf.d/welcome.conf.disabled
# chown -R privacyidea:root /var/run/wsgi
[root@iZ8vbcvjtgyijxs9ixmh6oZ conf.d]# vi /etc/httpd/conf.d/privacyidea.conf- 配置文件
TraceEnable off
ServerSignature Off
ServerTokens Prod
WSGIPythonHome /opt/privacyidea
WSGISocketPrefix /var/run/wsgi
<VirtualHost _default_:80>
ServerAdmin webmaster@localhost
ServerName localhost
RewriteEngine On
RewriteCond %{HTTPS} !=On
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L]
</VirtualHost>
<VirtualHost _default_:443>
ServerAdmin webmaster@localhost
ServerName localhost
DocumentRoot /var/www
<Directory />
Require all granted
Options FollowSymLinks
AllowOverride None
</Directory>
# The daemon is running as user 'privacyidea'
# This user should have access to the encKey database encryption file
WSGIDaemonProcess privacyidea python-path=/etc/privacyidea:/opt/privacyidea/lib/python2.7/site-packages processes=1 threads=15 display-name=%{GROUP} user=privacyidea
WSGIProcessGroup privacyidea
WSGIPassAuthorization On
WSGIScriptAlias / /etc/privacyidea/privacyideaapp.wsgi
SSLEngine On
SSLProtocol All -SSLv2 -SSLv3
SSLHonorCipherOrder On
SSLCipherSuite EECDH+AES256:DHE+AES256:EECDH+AES:EDH+AES:-SHA1:EECDH+RC4:EDH+RC4:RC4-SHA:AES256-SHA:!aNULL:!eNULL:!EXP:!LOW:!MD5
SSLCertificateFile /etc/pki/tls/certs/privacyideaserver.pem
SSLCertificateKeyFile /etc/pki/tls/private/privacyideaserver.key
</VirtualHost>TraceEnable off
ServerSignature Off
ServerTokens Prod
WSGIPythonHome /opt/privacyidea
WSGISocketPrefix /var/run/wsgi
<VirtualHost _default_:80>
ServerAdmin webmaster@localhost
ServerName localhost
RewriteEngine On
RewriteCond %{HTTPS} !=On
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L]
</VirtualHost>
<VirtualHost _default_:443>
ServerAdmin webmaster@localhost
ServerName localhost
DocumentRoot /var/www
<Directory />
Require all granted
Options FollowSymLinks
AllowOverride None
</Directory>
# The daemon is running as user 'privacyidea'
# This user should have access to the encKey database encryption file
WSGIDaemonProcess privacyidea python-path=/etc/privacyidea:/opt/privacyidea/lib/python2.7/site-packages processes=1 threads=15 display-name=%{GROUP} user=privacyidea
WSGIProcessGroup privacyidea
WSGIPassAuthorization On
WSGIScriptAlias / /etc/privacyidea/privacyideaapp.wsgi
SSLEngine On
SSLProtocol All -SSLv2 -SSLv3
SSLHonorCipherOrder On
SSLCipherSuite EECDH+AES256:DHE+AES256:EECDH+AES:EDH+AES:-SHA1:EECDH+RC4:EDH+RC4:RC4-SHA:AES256-SHA:!aNULL:!eNULL:!EXP:!LOW:!MD5
SSLCertificateFile /etc/pki/tls/certs/privacyideaserver.pem
SSLCertificateKeyFile /etc/pki/tls/private/privacyideaserver.key
</VirtualHost>- 证书
[root@iZ8vbcvjtgyijxs9ixmh6oZ conf.d]# /opt/privacyidea/bin/privacyidea-create-certificate -f /etc/httpd/conf.d/privacyidea.conf
Creating certificate...
Generating a 2048 bit RSA private key
.................................................+++
......+++
writing new private key to '/etc/pki/tls/private/privacyideaserver.key'
-----
created key and cert...
[root@iZ8vbcvjtgyijxs9ixmh6oZ conf.d]# /opt/privacyidea/bin/privacyidea-create-certificate -f /etc/httpd/conf.d/privacyidea.conf
Creating certificate...
Generating a 2048 bit RSA private key
.................................................+++
......+++
writing new private key to '/etc/pki/tls/private/privacyideaserver.key'
-----
created key and cert...修改域名
sed -i 's/#ServerName www.example.com:80/ServerName privacyidea.freehan.ink:80/g' /etc/httpd/conf/httpd.conf
#检查语法
apachectl configtest
[root@iZ8vbcvjtgyijxs9ixmh6oZ conf.d]# ll
total 32
-rw-r--r-- 1 root root 2926 Nov 10 22:26 autoindex.conf.disabled
-rw-r--r-- 1 root root 1293 Dec 2 15:40 privacyidea.conf
-rw-r--r-- 1 root root 366 Nov 10 22:27 README
-rw-r--r-- 1 root root 9443 Sep 30 2020 ssl.conf
-rw-r--r-- 1 root root 1252 Sep 30 2020 userdir.conf.disabled
-rw-r--r-- 1 root root 824 Sep 30 2020 welcome.conf.disabled
#重启服务
systemctl restart httpd.servicesed -i 's/#ServerName www.example.com:80/ServerName privacyidea.freehan.ink:80/g' /etc/httpd/conf/httpd.conf
#检查语法
apachectl configtest
[root@iZ8vbcvjtgyijxs9ixmh6oZ conf.d]# ll
total 32
-rw-r--r-- 1 root root 2926 Nov 10 22:26 autoindex.conf.disabled
-rw-r--r-- 1 root root 1293 Dec 2 15:40 privacyidea.conf
-rw-r--r-- 1 root root 366 Nov 10 22:27 README
-rw-r--r-- 1 root root 9443 Sep 30 2020 ssl.conf
-rw-r--r-- 1 root root 1252 Sep 30 2020 userdir.conf.disabled
-rw-r--r-- 1 root root 824 Sep 30 2020 welcome.conf.disabled
#重启服务
systemctl restart httpd.service
3.其他配置
修正权限
chown -R privacyidea:root /etc/privacyideachown -R privacyidea:root /etc/privacyidea修改管理密码
cd /opt/privacyidea
source bin/activate
pi-manage admin change -p admincd /opt/privacyidea
source bin/activate
pi-manage admin change -p admin升级privacyIDEA
cd /opt/privacyidea
source bin/activate
pip install --upgrade cffi
pip install --upgrade bcrypt
pip install --upgrade privacyideacd /opt/privacyidea
source bin/activate
pip install --upgrade cffi
pip install --upgrade bcrypt
pip install --upgrade privacyidea4.配置freeipa
创建users
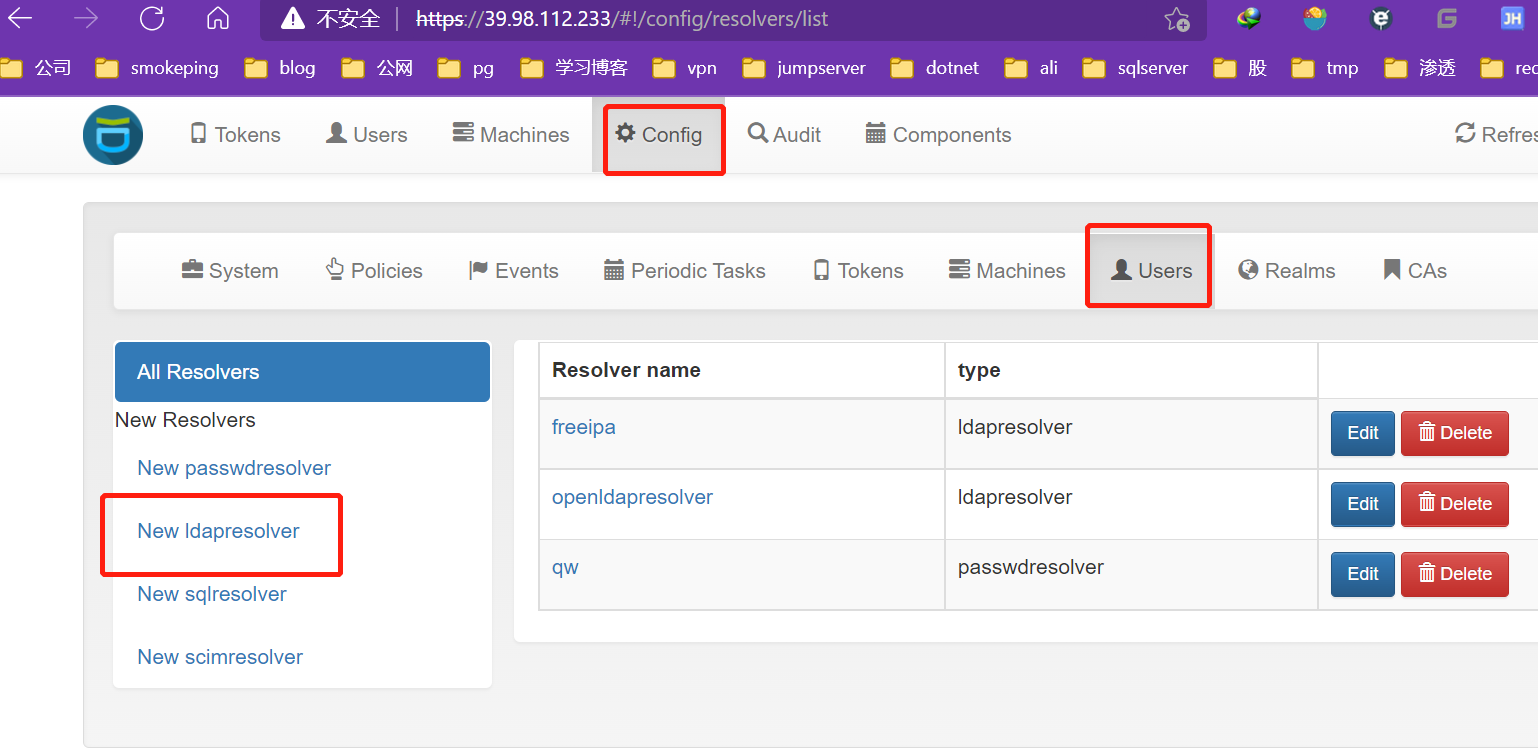
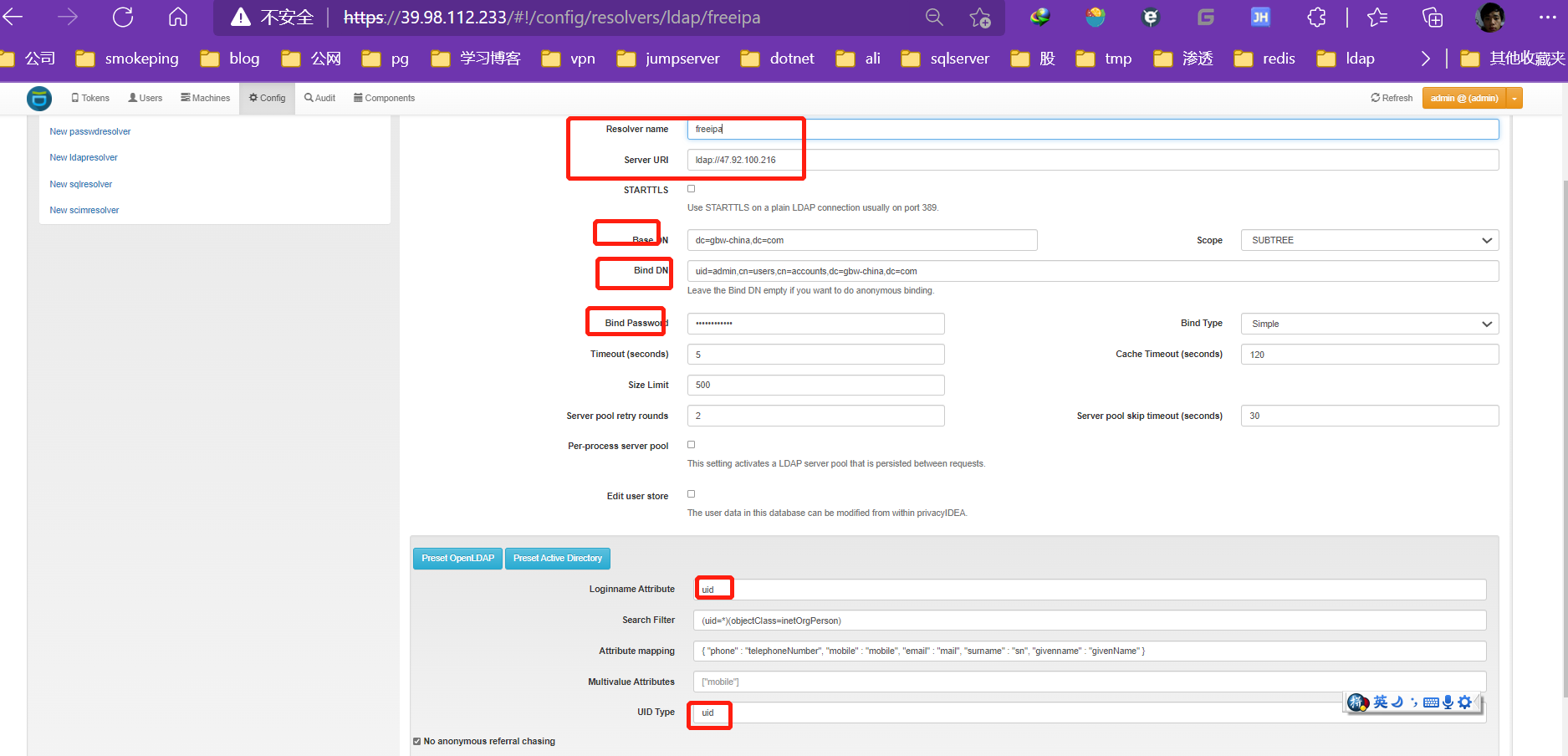
- 注意uid
The UID Type is the unique identifier for the LDAP object. If it is left blank, the distinguished name will be used. In case of OpenLDAP this can be entryUUID and in case of Active Directory objectGUID. For FreeIPA you can use ipaUniqueID
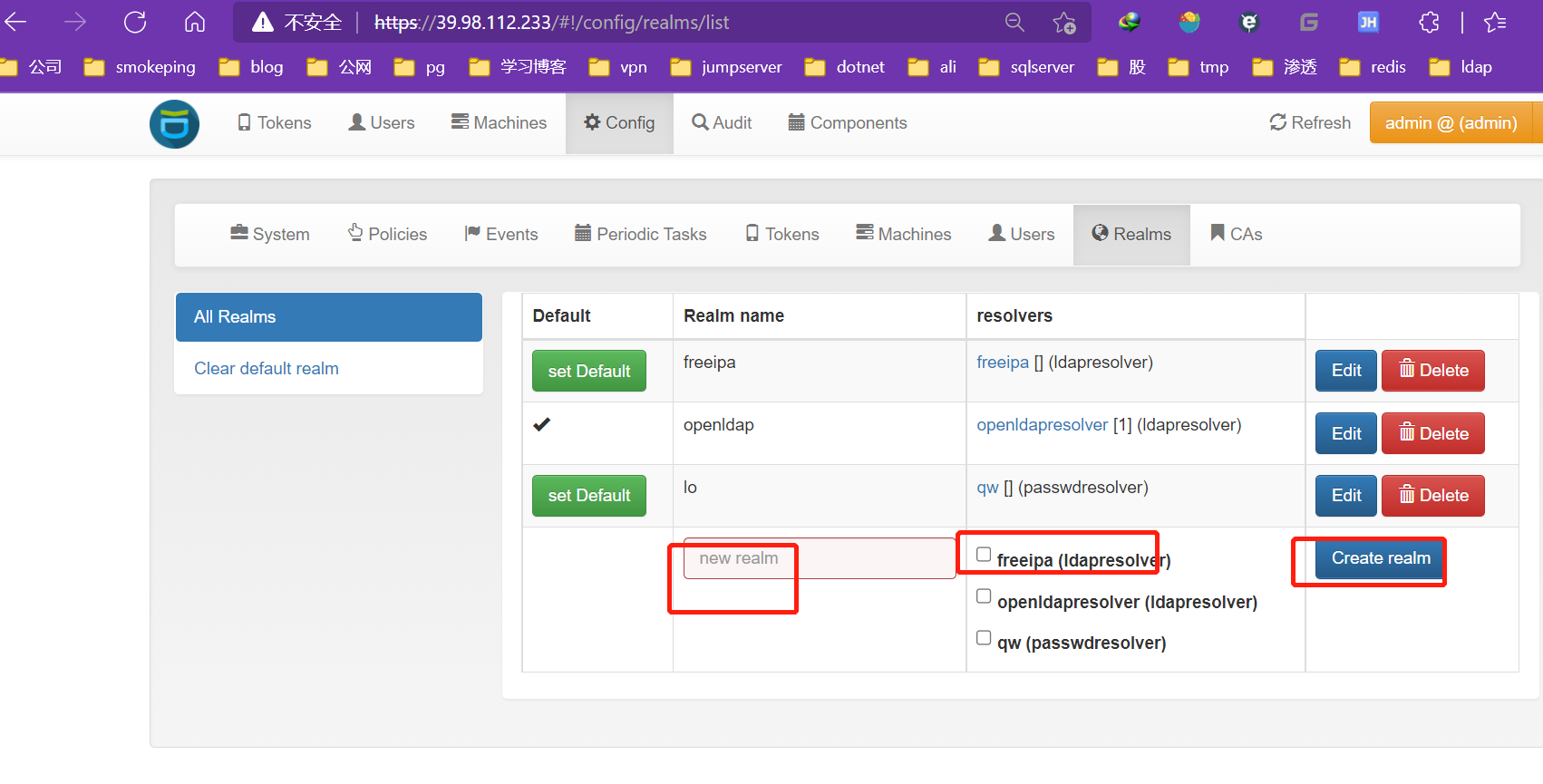
创建realms
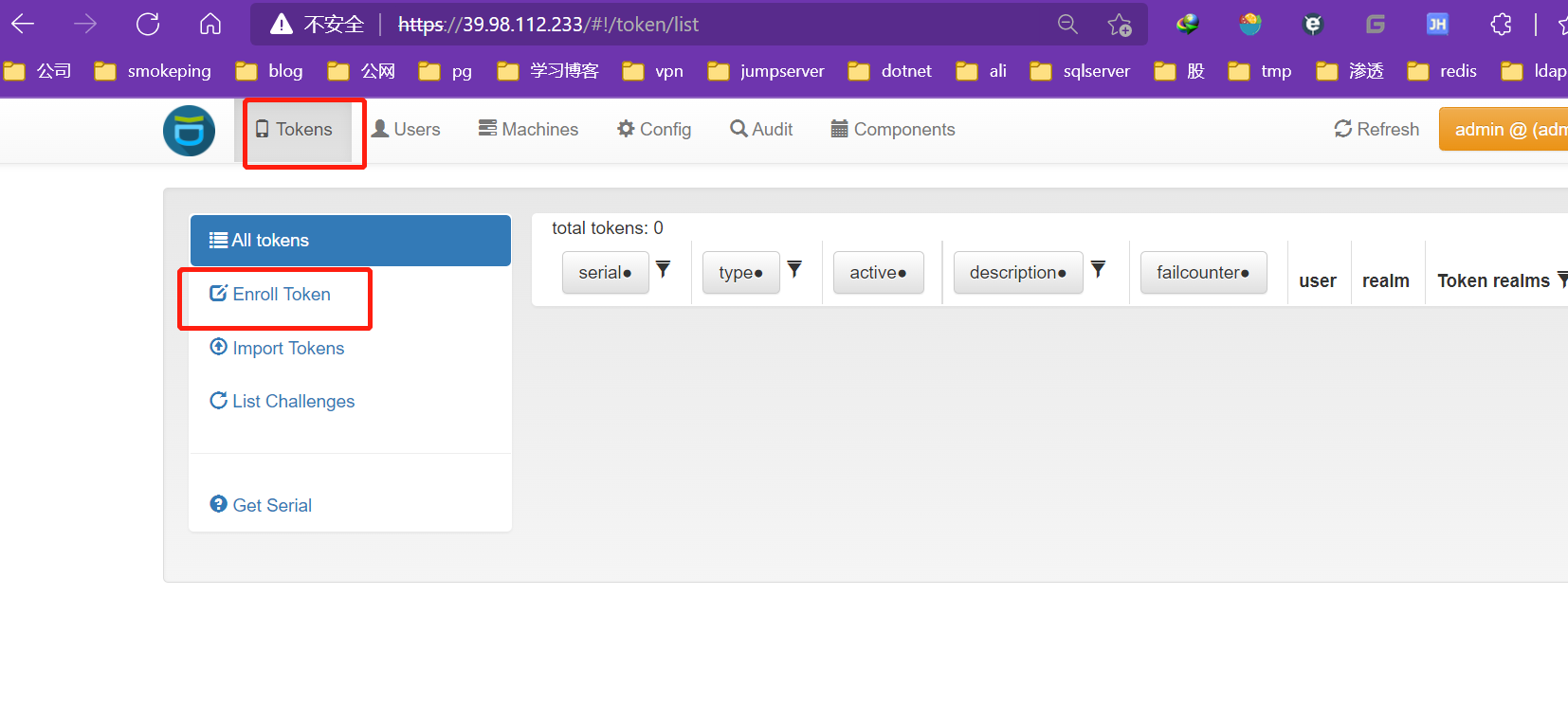
创建google验证
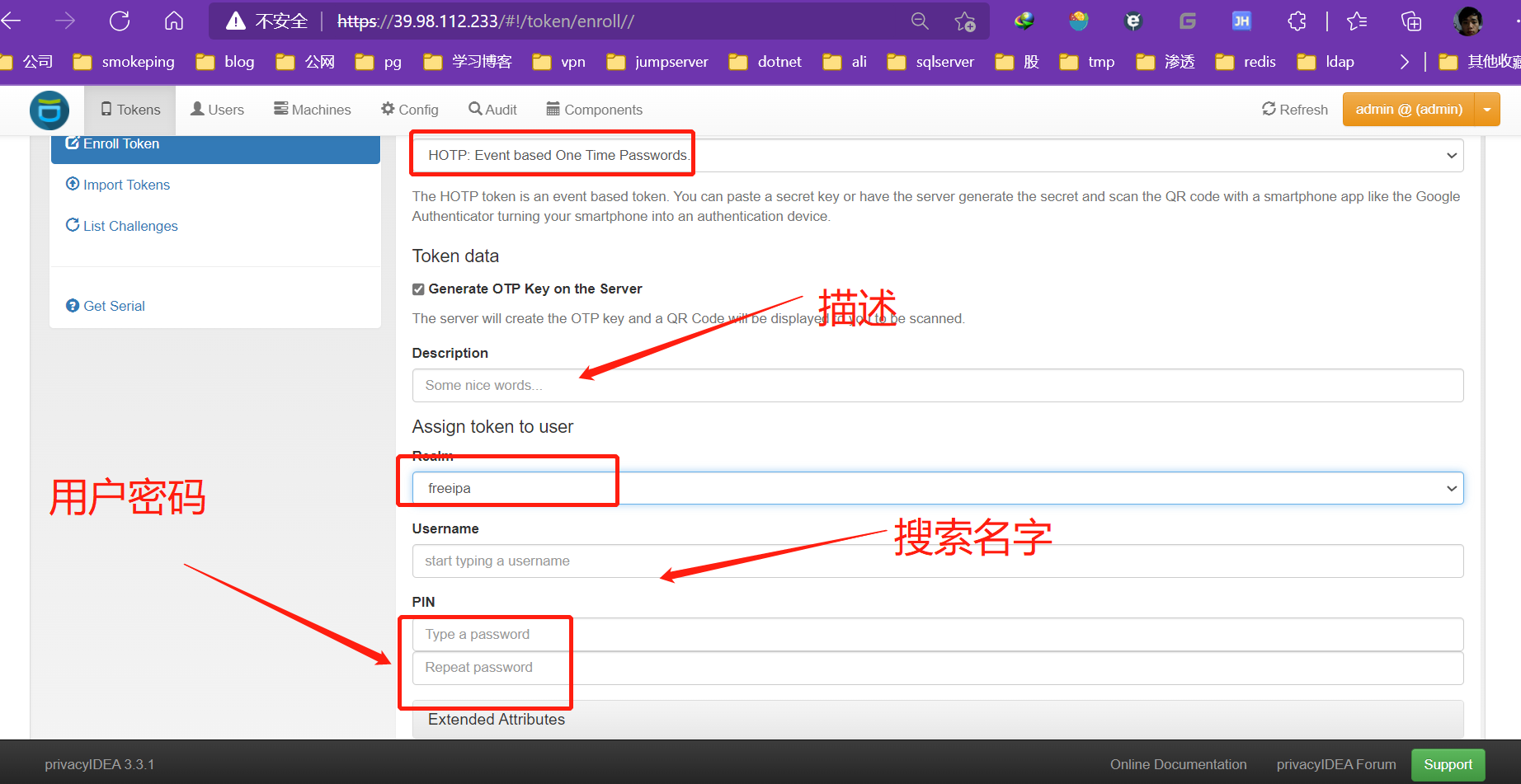
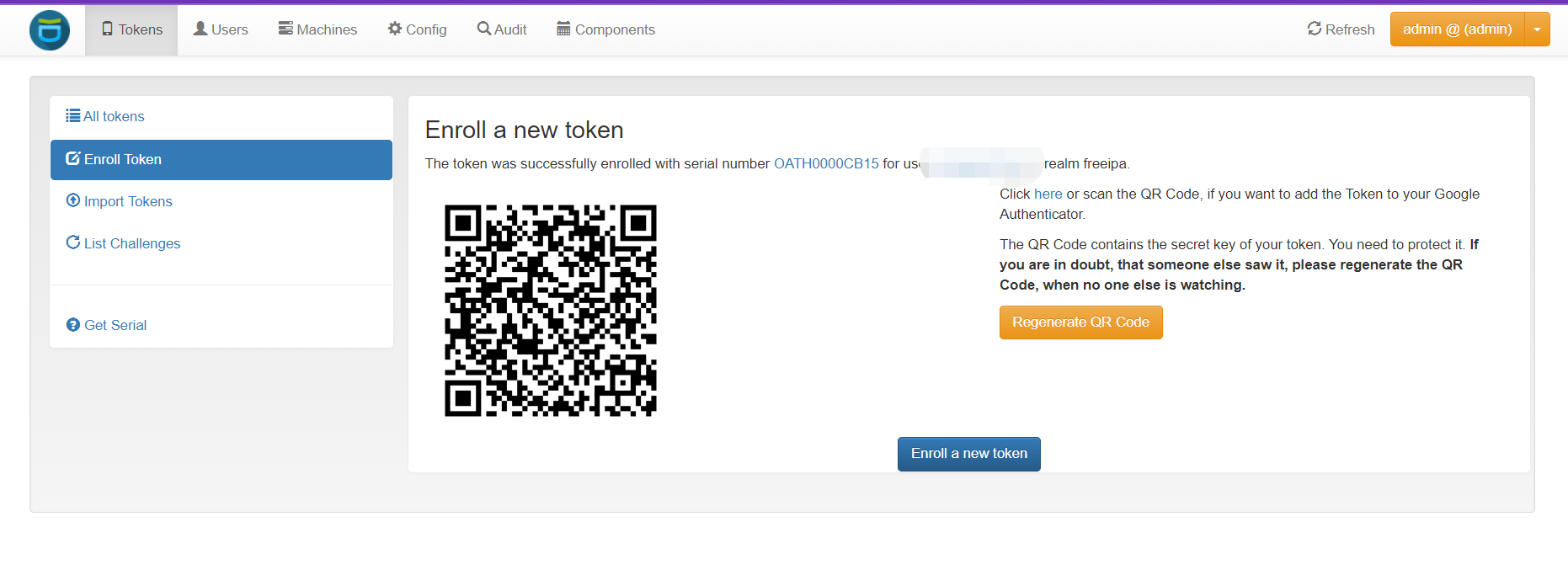
客户端配置
安卓用夸克密码验证器,进行扫码
ios用google验证器,进行扫码
官方网站 ———– https://www.privacyidea.org/
软件的特点 ———– https://www.privacyidea.org/about/features/
privacyIDEA的github ——————- https://github.com/privacyidea/privacyideahttps://www.privacyidea.org/about/the-code/
安装教程 ———— https://www.privacyidea.org/two-factor-authentication-with-otp-on-centos-7/https://privacyidea.readthedocs.io/en/latest/