1. 什么是Dashboard
Dashboard是kubernetes的Web GUI,可用于在kubernetes集群上部署容器化应用,应用排障、管理集群本身及其附加的资源等。它常被管理员用于集群及应用速览,创建或修改单个资源(deployment、jobs和daemonset)以及扩展deployment、启动滚动更新、重启pod或使用部署向导一个新应用等;
这里需注意一点是Dashboard依赖于Metrics-Server完成指标数据的采集和可视化;
官方地址: https://kubernetes.io/docs/tasks/access-application-cluster/web-ui-dashboard/
GitHub地址: https://github.com/kubernetes/dashboard
1.1 下载yaml
bash
wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.6.1/aio/deploy/recommended.yamlwget https://raw.githubusercontent.com/kubernetes/dashboard/v2.6.1/aio/deploy/recommended.yaml1.2 安装
bash
[root@kube-master dashboard]# kubectl apply -f recommended.yaml
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created[root@kube-master dashboard]# kubectl apply -f recommended.yaml
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created- 查看
bash
[root@kube-master dashboard]# kubectl get pods,service -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
pod/dashboard-metrics-scraper-7c857855d9-h46gm 1/1 Running 0 2m20s
pod/kubernetes-dashboard-6b79449649-pcphx 1/1 Running 0 2m20s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/dashboard-metrics-scraper ClusterIP 192.168.159.205 <none> 8000/TCP 2m20s
service/kubernetes-dashboard ClusterIP 192.168.11.25 <none> 443/TCP 2m20s[root@kube-master dashboard]# kubectl get pods,service -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
pod/dashboard-metrics-scraper-7c857855d9-h46gm 1/1 Running 0 2m20s
pod/kubernetes-dashboard-6b79449649-pcphx 1/1 Running 0 2m20s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/dashboard-metrics-scraper ClusterIP 192.168.159.205 <none> 8000/TCP 2m20s
service/kubernetes-dashboard ClusterIP 192.168.11.25 <none> 443/TCP 2m20s修改svc ClusterIP 为NodePort
1.3 创建授权
安装好了,没有账号还是无法访问的。所以要授权;
基于token认证与授权
创建ServiceAccount
创建ServiceAccount然后通过dashboard的token进行验证
bash
kubectl create serviceaccount admin-user -n kubernetes-dashboardkubectl create serviceaccount admin-user -n kubernetes-dashboard绑定用户
bash
#将sa账户通过clusterrolebinding绑定到cluster-admin集群角色上,以便拥有集群管理员权限
kubectl create clusterrolebinding admin-user --clusterrole=cluster-admin --serviceaccount=kubernetes-dashboard:admin-user#将sa账户通过clusterrolebinding绑定到cluster-admin集群角色上,以便拥有集群管理员权限
kubectl create clusterrolebinding admin-user --clusterrole=cluster-admin --serviceaccount=kubernetes-dashboard:admin-user查看secret
bash
[root@kube-master dashboard]# kubectl describe sa admin-user -n kubernetes-dashboard
Name: admin-user
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: admin-user-token-tjbgz
Tokens: admin-user-token-tjbgz
Events: <none>[root@kube-master dashboard]# kubectl describe sa admin-user -n kubernetes-dashboard
Name: admin-user
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: admin-user-token-tjbgz
Tokens: admin-user-token-tjbgz
Events: <none>- 通过文件创建权限
yaml
[root@kube-master dashboard]# cat 2.admin.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin-user
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kubernetes-dashboard[root@kube-master dashboard]# cat 2.admin.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin-user
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kubernetes-dashboard- 访问
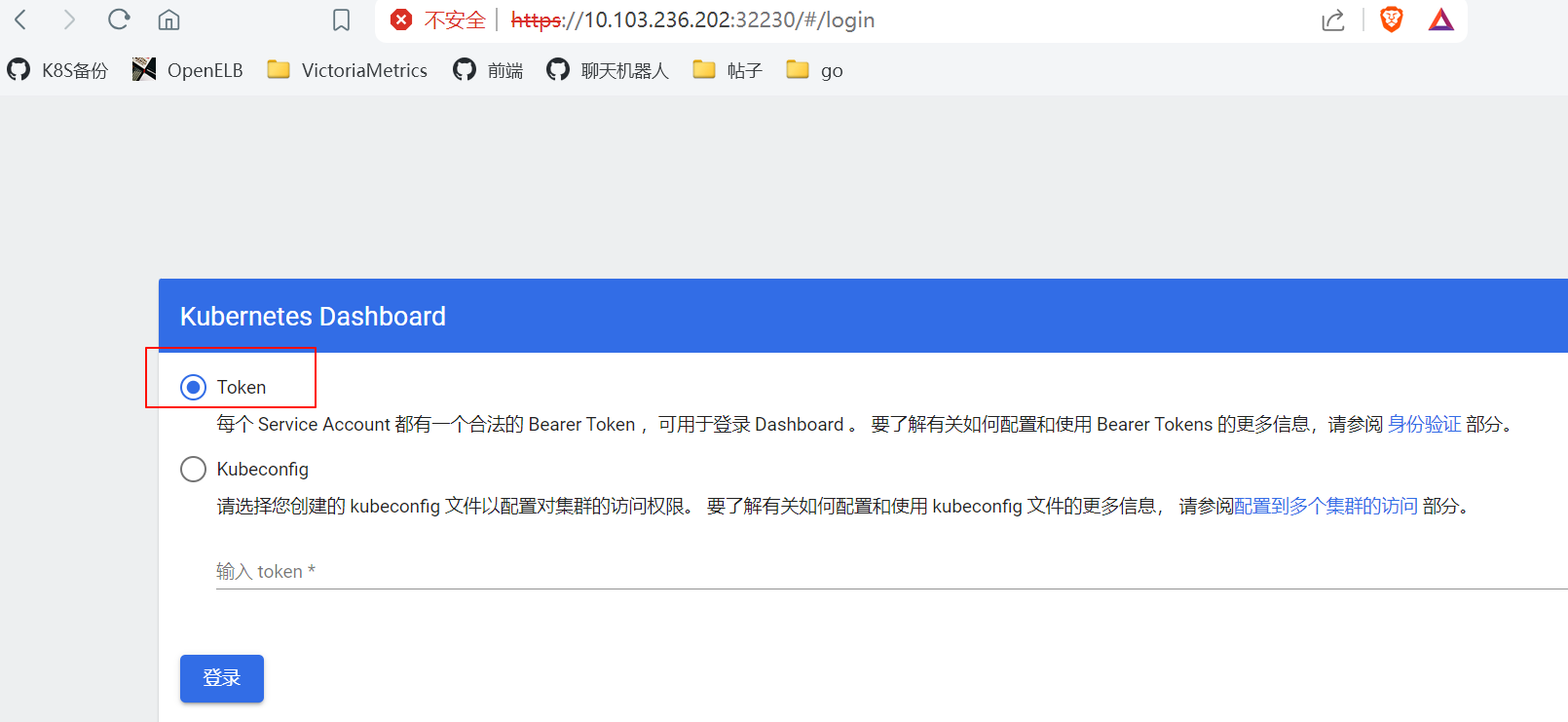
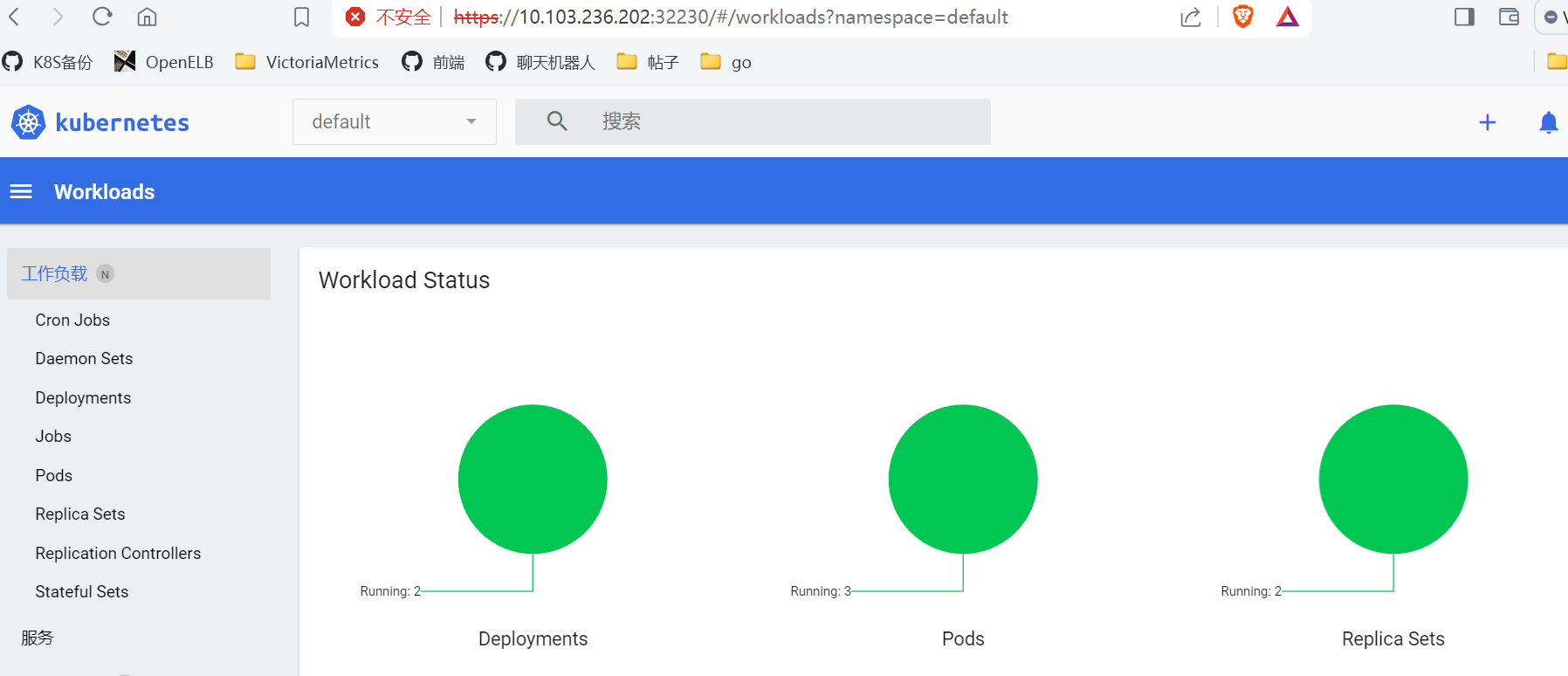
- 获取token
bash
[root@kube-master dashboard]# kubectl describe sa admin-user -n kubernetes-dashboard
Name: admin-user
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: admin-user-token-tjbgz
Tokens: admin-user-token-tjbgz
Events: <none>
[root@kube-master dashboard]# kubectl describe secrets admin-user-token-tjbgz -n kubernetes-dashboard
Name: admin-user-token-tjbgz
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: kubernetes.io/service-account.name: admin-user
kubernetes.io/service-account.uid: cbf8157c-92da-45f3-89f1-23f37c3671df
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1099 bytes
namespace: 20 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IjhPUFdTTy0teFQ3QTVYSnI3Mk1rTU1fUFYyc1oxQUpWMkZ3cER2WkE3NmcifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi11c2VyLXRva2VuLXRqYmd6Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImFkbWluLXVzZXIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJjYmY4MTU3Yy05MmRhLTQ1ZjMtODlmMS0yM2YzN2MzNjcxZGYiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZXJuZXRlcy1kYXNoYm9hcmQ6YWRtaW4tdXNlciJ9.epaYpJP9qYH_MWqa2nMDgF-TwwaL_EGA9iUBNkiGyy8sstsvC94eRGuNP2891Ht0hYBwYDe7keub03Tn6IwjzBPo2H3GQyYdIDBxJOjcBb4YbZorHm35mFlWzNsSYpBQ80PKlsqFOpmyRZcswr0TjjttKg5NsPgq-jTDJ76j57CTR12Yi29pxAh5AzEmBE0GCarvQDNIhUrHeVv6t21AWQgckBamvOYyxdPoVrPw3I2154e36z4Q2wW7XLSrIrTjFKTc0QwvleR5o3hAs_zq-GC09rZKqPKfRNURxlxkPkefvjtGLph8lcQz3uJqHaQ5cSF0QglNDfZFZ9AOXRr8Ow[root@kube-master dashboard]# kubectl describe sa admin-user -n kubernetes-dashboard
Name: admin-user
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: admin-user-token-tjbgz
Tokens: admin-user-token-tjbgz
Events: <none>
[root@kube-master dashboard]# kubectl describe secrets admin-user-token-tjbgz -n kubernetes-dashboard
Name: admin-user-token-tjbgz
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: kubernetes.io/service-account.name: admin-user
kubernetes.io/service-account.uid: cbf8157c-92da-45f3-89f1-23f37c3671df
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1099 bytes
namespace: 20 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IjhPUFdTTy0teFQ3QTVYSnI3Mk1rTU1fUFYyc1oxQUpWMkZ3cER2WkE3NmcifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi11c2VyLXRva2VuLXRqYmd6Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImFkbWluLXVzZXIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJjYmY4MTU3Yy05MmRhLTQ1ZjMtODlmMS0yM2YzN2MzNjcxZGYiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZXJuZXRlcy1kYXNoYm9hcmQ6YWRtaW4tdXNlciJ9.epaYpJP9qYH_MWqa2nMDgF-TwwaL_EGA9iUBNkiGyy8sstsvC94eRGuNP2891Ht0hYBwYDe7keub03Tn6IwjzBPo2H3GQyYdIDBxJOjcBb4YbZorHm35mFlWzNsSYpBQ80PKlsqFOpmyRZcswr0TjjttKg5NsPgq-jTDJ76j57CTR12Yi29pxAh5AzEmBE0GCarvQDNIhUrHeVv6t21AWQgckBamvOYyxdPoVrPw3I2154e36z4Q2wW7XLSrIrTjFKTc0QwvleR5o3hAs_zq-GC09rZKqPKfRNURxlxkPkefvjtGLph8lcQz3uJqHaQ5cSF0QglNDfZFZ9AOXRr8Ow
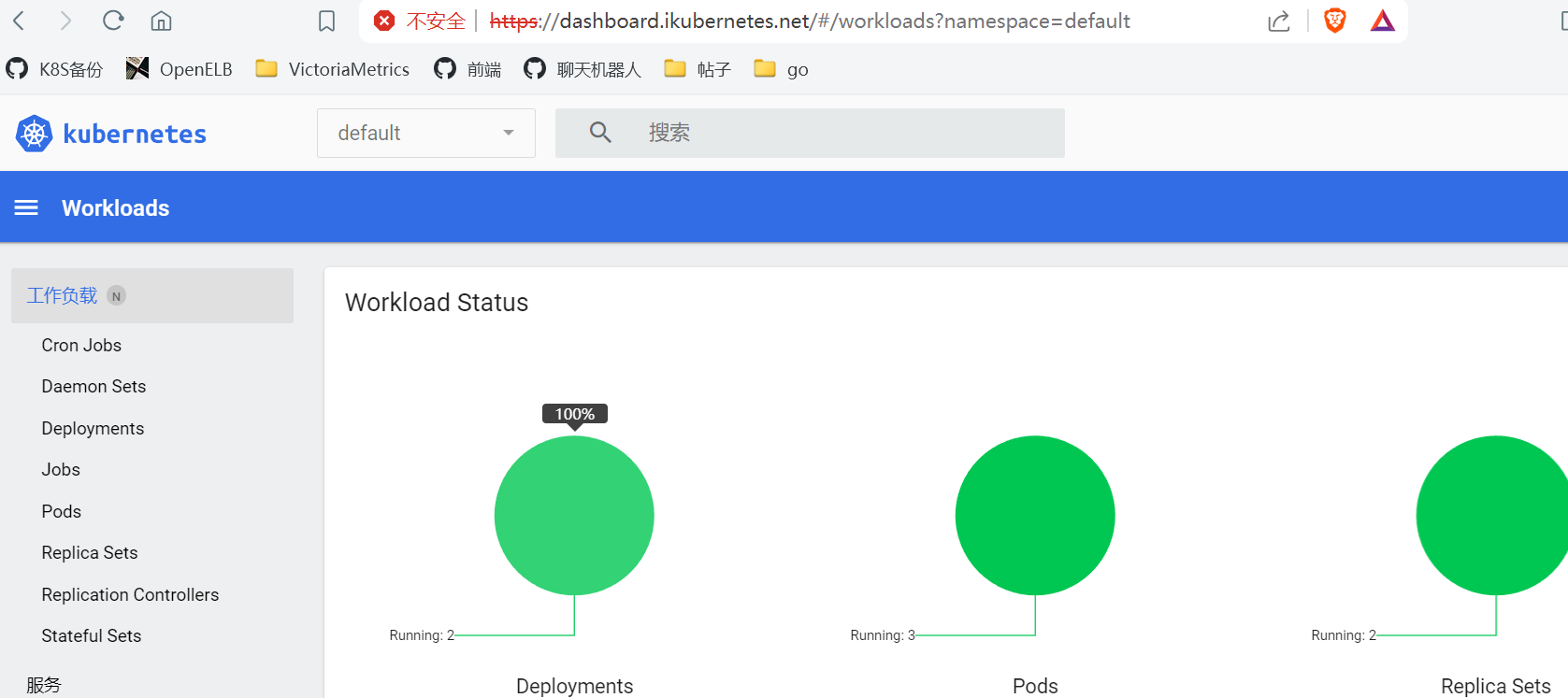
2. 基于ingress发布dashboard
2.1 查看dashboard默认的访问方式
bash
[root@kube-master dashboard]# kubectl get pods,svc -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
pod/dashboard-metrics-scraper-7c857855d9-h46gm 1/1 Running 0 26m
pod/kubernetes-dashboard-6b79449649-pcphx 1/1 Running 0 26m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/dashboard-metrics-scraper ClusterIP 192.168.159.205 <none> 8000/TCP 26m
service/kubernetes-dashboard ClusterIP 192.168.11.25 <none> 443/TCP 26m[root@kube-master dashboard]# kubectl get pods,svc -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
pod/dashboard-metrics-scraper-7c857855d9-h46gm 1/1 Running 0 26m
pod/kubernetes-dashboard-6b79449649-pcphx 1/1 Running 0 26m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/dashboard-metrics-scraper ClusterIP 192.168.159.205 <none> 8000/TCP 26m
service/kubernetes-dashboard ClusterIP 192.168.11.25 <none> 443/TCP 26m2.2 检查Ingress Controller
bash
[root@kube-master dashboard]# kubectl get pods -n ingress-nginx
NAME READY STATUS RESTARTS AGE
ingress-nginx-admission-create-s2zhk 0/1 Completed 0 9d
ingress-nginx-admission-patch-dq5hw 0/1 Completed 0 9d
ingress-nginx-controller-nx4lb 1/1 Running 13 (77m ago) 9d
ingress-nginx-controller-wtftx 1/1 Running 12 (77m ago) 9d[root@kube-master dashboard]# kubectl get pods -n ingress-nginx
NAME READY STATUS RESTARTS AGE
ingress-nginx-admission-create-s2zhk 0/1 Completed 0 9d
ingress-nginx-admission-patch-dq5hw 0/1 Completed 0 9d
ingress-nginx-controller-nx4lb 1/1 Running 13 (77m ago) 9d
ingress-nginx-controller-wtftx 1/1 Running 12 (77m ago) 9d2.3 创建自签证书
自签发证书。当然生产环境中理应当使用机构签发的证书
bash
[root@kube-master dashboard]# openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout kube-dashboard.key -out kube-dashboard.crt -subj "/CN=dashboard.kube.com/O=dashboard.ikubernetes.net"
Generating a 2048 bit RSA private key
................................................................................................................................+++
.........+++
writing new private key to 'kube-dashboard.key'
-----[root@kube-master dashboard]# openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout kube-dashboard.key -out kube-dashboard.crt -subj "/CN=dashboard.kube.com/O=dashboard.ikubernetes.net"
Generating a 2048 bit RSA private key
................................................................................................................................+++
.........+++
writing new private key to 'kube-dashboard.key'
------ 创建tls类型的Secret为ingress提供配置
bash
#创建
kubectl create secret tls dashboard-tls --key kube-dashboard.key --cert kube-dashboard.crt -n kubernetes-dashboard
#查看
[root@kube-master dashboard]# kubectl get secrets -n kubernetes-dashboard
NAME TYPE DATA AGE
dashboard-tls kubernetes.io/tls 2 32s#创建
kubectl create secret tls dashboard-tls --key kube-dashboard.key --cert kube-dashboard.crt -n kubernetes-dashboard
#查看
[root@kube-master dashboard]# kubectl get secrets -n kubernetes-dashboard
NAME TYPE DATA AGE
dashboard-tls kubernetes.io/tls 2 32s2.4 配置Ingress规则
Nginx Ingress Controller默认使用HTTP协议转发请求到后端业务容器。当您的业务容器为HTTPS协议时,可以通过使用注解nginx.ingress.kubernetes.io/backend-protocol: "HTTPS"来使得Nginx Ingress Controller使用HTTP协议转发请求到后端业务容器
yaml
[root@kube-master dashboard]# cat 3.ingress-dashboard.yaml
# cat ingress-dashboard.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: dashboard-ingress
namespace: kubernetes-dashboard
annotations:
nginx.ingress.kubernetes.io/backend-protocol: "HTTPS" #注意这里:必须指定后端服务为HTTPS服务。
spec:
ingressClassName: "nginx" #控制器的类型为nginx
tls:
- hosts:
- dashboard.ikubernetes.net #主机名
secretName: dashboard-tls #这里引用创建的secrets
rules:
- host: dashboard.ikubernetes.net
http:
paths:
- path: /
pathType: Prefix #起始与根都进行代理。
backend:
service:
name: kubernetes-dashboard #service名称
port: #后端端口
number: 443[root@kube-master dashboard]# cat 3.ingress-dashboard.yaml
# cat ingress-dashboard.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: dashboard-ingress
namespace: kubernetes-dashboard
annotations:
nginx.ingress.kubernetes.io/backend-protocol: "HTTPS" #注意这里:必须指定后端服务为HTTPS服务。
spec:
ingressClassName: "nginx" #控制器的类型为nginx
tls:
- hosts:
- dashboard.ikubernetes.net #主机名
secretName: dashboard-tls #这里引用创建的secrets
rules:
- host: dashboard.ikubernetes.net
http:
paths:
- path: /
pathType: Prefix #起始与根都进行代理。
backend:
service:
name: kubernetes-dashboard #service名称
port: #后端端口
number: 443bash
加载配置文件
# kubectl apply -f 3.ingress-dashboard.yaml
#检查Ingress配置文件
[root@kube-master dashboard]# kubectl describe ingress -n kubernetes-dashboard
Name: dashboard-ingress
Namespace: kubernetes-dashboard
Address: 10.103.236.70
Default backend: default-http-backend:80 (<error: endpoints "default-http-backend" not found>)
TLS:
dashboard-tls terminates dashboard.ikubernetes.net
Rules:
Host Path Backends
---- ---- --------
dashboard.ikubernetes.net
/ kubernetes-dashboard:443 (172.30.0.163:8443)
Annotations: nginx.ingress.kubernetes.io/backend-protocol: HTTPS
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal Sync 7m43s (x2 over 7m51s) nginx-ingress-controller Scheduled for sync
Normal Sync 7m42s (x2 over 7m51s) nginx-ingress-controller Scheduled for sync加载配置文件
# kubectl apply -f 3.ingress-dashboard.yaml
#检查Ingress配置文件
[root@kube-master dashboard]# kubectl describe ingress -n kubernetes-dashboard
Name: dashboard-ingress
Namespace: kubernetes-dashboard
Address: 10.103.236.70
Default backend: default-http-backend:80 (<error: endpoints "default-http-backend" not found>)
TLS:
dashboard-tls terminates dashboard.ikubernetes.net
Rules:
Host Path Backends
---- ---- --------
dashboard.ikubernetes.net
/ kubernetes-dashboard:443 (172.30.0.163:8443)
Annotations: nginx.ingress.kubernetes.io/backend-protocol: HTTPS
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal Sync 7m43s (x2 over 7m51s) nginx-ingress-controller Scheduled for sync
Normal Sync 7m42s (x2 over 7m51s) nginx-ingress-controller Scheduled for sync- 访问