- 阿里云环境
- centos7
- openvpn2.4
1.server端配置
port 10020
proto tcp
dev tun
tun-mtu 9000
sndbuf 393216
rcvbuf 393216
ca ca.crt
cert server.crt
key server.key
dh dh.pem
cipher AES-256-CBC
auth SHA512
tls-auth ta.key 0
topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 114.114.114.114"
push "dhcp-option DNS 1.1.1.1"
push "sndbuf 393216"
push "rcvbuf 393216"
route 192.168.1.0 255.255.255.0
push "route 172.18.106.133 255.255.255.0"
client-to-client
verify-client-cert
keepalive 10 120
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
log-append openvpn.log
verb 3
crl-verify crl.pem
comp-lzo
mute 20
max-clients 100
plugin /usr/lib64/openvpn/plugins/openvpn-plugin-auth-pam.so openvpn
client-cert-not-required
username-as-common-name
reneg-sec 36000port 10020
proto tcp
dev tun
tun-mtu 9000
sndbuf 393216
rcvbuf 393216
ca ca.crt
cert server.crt
key server.key
dh dh.pem
cipher AES-256-CBC
auth SHA512
tls-auth ta.key 0
topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 114.114.114.114"
push "dhcp-option DNS 1.1.1.1"
push "sndbuf 393216"
push "rcvbuf 393216"
route 192.168.1.0 255.255.255.0
push "route 172.18.106.133 255.255.255.0"
client-to-client
verify-client-cert
keepalive 10 120
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
log-append openvpn.log
verb 3
crl-verify crl.pem
comp-lzo
mute 20
max-clients 100
plugin /usr/lib64/openvpn/plugins/openvpn-plugin-auth-pam.so openvpn
client-cert-not-required
username-as-common-name
reneg-sec 36000- 关键点
#服务器增加到192.168.4.0/24的路由
route 192.168.4.0 255.255.255.0
#允许客户端子网互通
client-to-client
#让所有客户端都增加到192.168.4.0/24的路由
push "route 192.168.4.0 255.255.255.0"#服务器增加到192.168.4.0/24的路由
route 192.168.4.0 255.255.255.0
#允许客户端子网互通
client-to-client
#让所有客户端都增加到192.168.4.0/24的路由
push "route 192.168.4.0 255.255.255.0"2.client端配置
client
dev tun
proto tcp
tun-mtu 9000
sndbuf 393216
rcvbuf 393216
remote 39.98.112.233 10020
resolv-retry infinite
nobind
persist-key
persist-tun
remote-cert-tls server
auth SHA512
cipher AES-256-CBC
setenv opt block-outside-dns
key-direction 1
comp-lzo
verb 3
auth-nocache
route-method exe
route-delay 2
auth-user-pass
reneg-sec 36000client
dev tun
proto tcp
tun-mtu 9000
sndbuf 393216
rcvbuf 393216
remote 39.98.112.233 10020
resolv-retry infinite
nobind
persist-key
persist-tun
remote-cert-tls server
auth SHA512
cipher AES-256-CBC
setenv opt block-outside-dns
key-direction 1
comp-lzo
verb 3
auth-nocache
route-method exe
route-delay 2
auth-user-pass
reneg-sec 360003.配置pam
[root@ipa pam.d]# cat openvpn
auth required /usr/lib64/security/pam_google_authenticator.so secret=/etc/openvpn/google-authenticator/${USER} user=gauth forward_pass
auth required pam_ldap.so use_first_pass debug
account required pam_ldap.so[root@ipa pam.d]# cat openvpn
auth required /usr/lib64/security/pam_google_authenticator.so secret=/etc/openvpn/google-authenticator/${USER} user=gauth forward_pass
auth required pam_ldap.so use_first_pass debug
account required pam_ldap.so4.配置防火墙
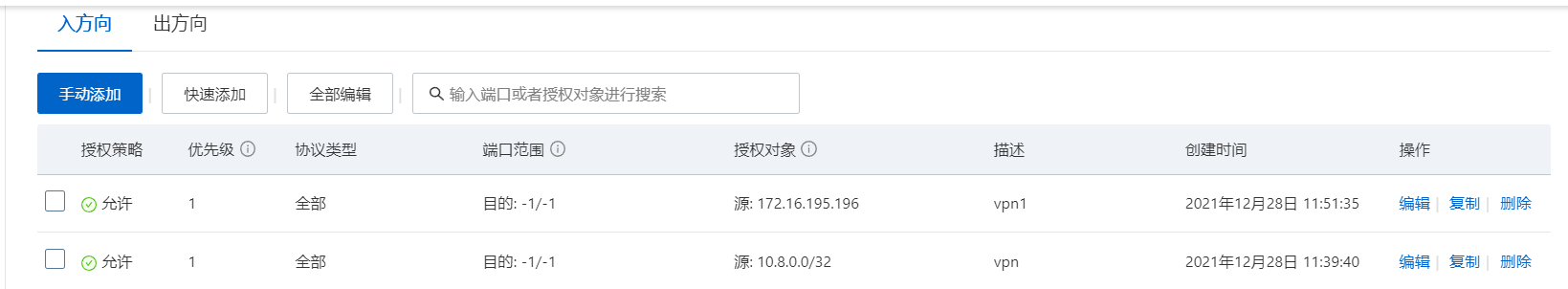
把tun0 地址10.8.0.1 和eth ip地址加入到安全组里面
firewall-cmd --add-masquerade --permanent
firewall-cmd --permanent --add-port=60168/tcp
firewall-cmd --permanent --direct --passthrough ipv4 -t nat -A POSTROUTING -s 10.8.8.0/24 -o eth0 -j MASQUERADE
firewall-cmd --reload
systemctl restart openvpn-server@server.servicefirewall-cmd --add-masquerade --permanent
firewall-cmd --permanent --add-port=60168/tcp
firewall-cmd --permanent --direct --passthrough ipv4 -t nat -A POSTROUTING -s 10.8.8.0/24 -o eth0 -j MASQUERADE
firewall-cmd --reload
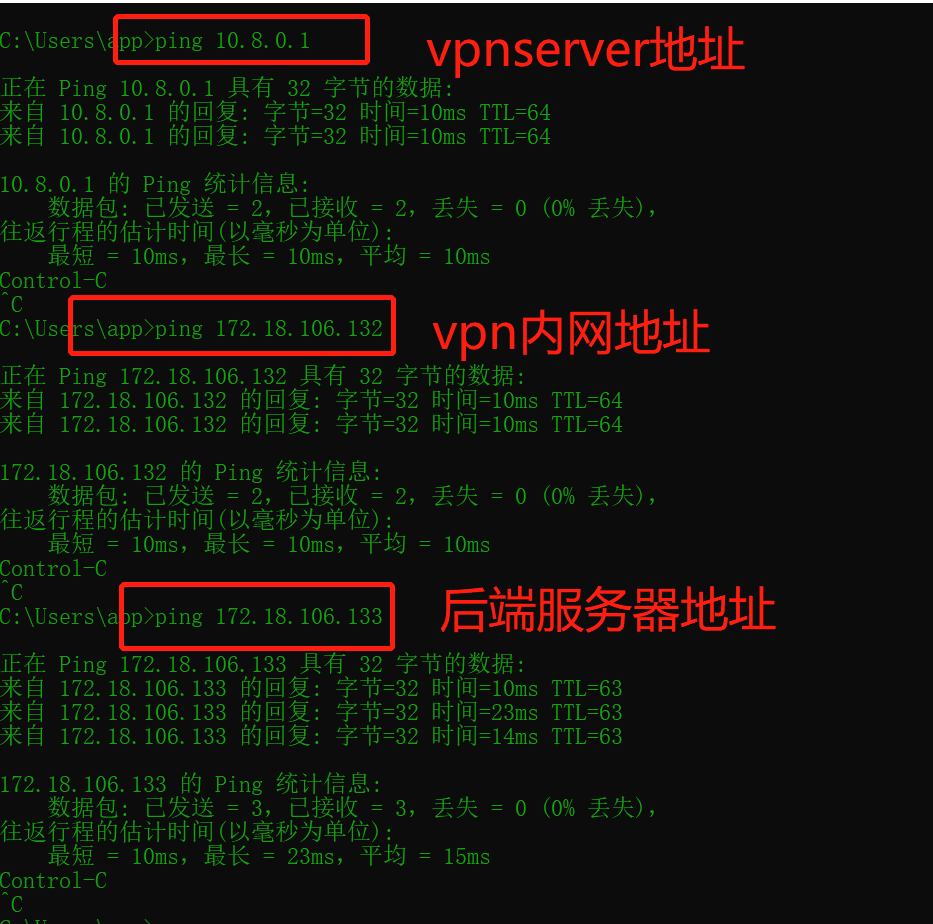
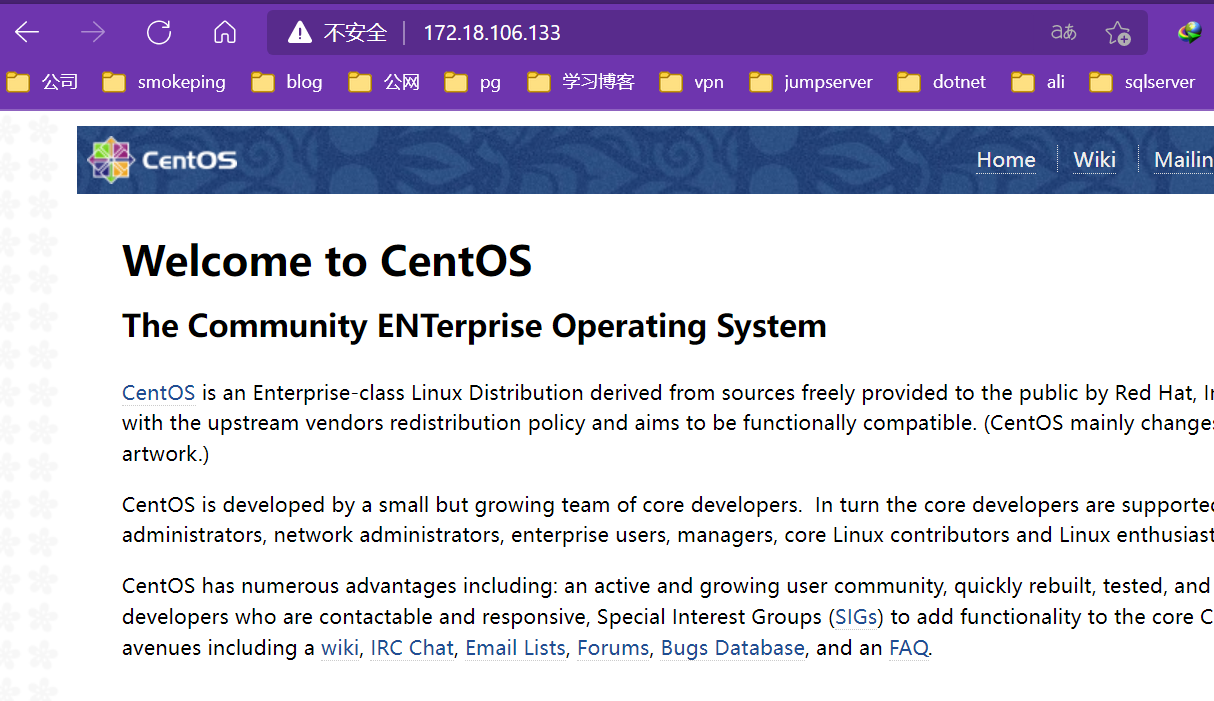
systemctl restart openvpn-server@server.service5.测试