1.Wireguard
官方文档:https://www.wireguard.com/performance
简介
WireGuard ®是一种非常简单而现代,快捷的VPN,利用最先进的加密技术。它比IPSec 更快,更简单,更精简,更有用。它比OpenVPN更高效。WireGuard设计为通用VPN,适用于多种不同情况。它是跨平台的,可大规模部署。它已经被认为是业内最安全,最易于使用,最简单的VPN解决方案,目前支持Linux,Windows,mac OS,Android,iOS等主流平台
WireGuard协议作为Linux内核模块运行,所以效率极高。使用了最先进的加密技术(利用Curve25519进行密钥交换,ChaCha20和Poly1305用于数据认证,BLAKE2用于散列),安全性毋庸置疑。WireGuard支持IP地址漫游,也就是网络断开再连,对它不会有影响。
WireGuard使用UDP协议传输数据,在不使用的情况下默认不会传输任何 UDP 数据包,所以比常规VPN省电很多,可以像SS一样一直挂着使用。WireGuard协议的速度瞬秒其它VPN协议
安全性
- Curve25519 目前最高水平的秘钥交换算法。
- ChaCha20 对称加解密算法,比 AES 更快更高效。
- Poly1305 是一种 MAC (Message Authentication Code) 标准,用于验证数据的完整性和消息的真实性。
- BLAKE2 一种更安全的 HASH 算法(类似的有 SHA1, SHA256, MD5)
- SipHash24 另一种 HASH 算法。
- HKDF 一种秘钥衍生算法
- 官方测试结果

2.NAT to NAT VPN
客户端如果想要同时访问多个 nat 只能像图中的 NAT C 客户端一样连接两个 vpn

wireguard 中没有 client/server 的概念,所有 nat 中的某台机器与 gateway 主机建立连接,即可实现共享所有节点的网络资源

- 环境
centos7.9_x64
内核要求,Linux ≥3.10
开启转发
#开启转发
vim /etc/sysctl.conf
net.ipv4.ip_forward = 1
net.ipv4.conf.all.proxy_arp = 1
## 应用修改
sysctl -p#开启转发
vim /etc/sysctl.conf
net.ipv4.ip_forward = 1
net.ipv4.conf.all.proxy_arp = 1
## 应用修改
sysctl -p升级内核
1.rpm
如果你想安装其他内核,你也可以在 这里下载
wget https://pan.cnsre.cn/d/Package/Linux/kernel/kernel-ml-5.15.2-1.el7.elrepo.x86_64.rpm
rpm -ivh kernel-ml-5.15.2-1.el7.elrepo.x86_64.rpmwget https://pan.cnsre.cn/d/Package/Linux/kernel/kernel-ml-5.15.2-1.el7.elrepo.x86_64.rpm
rpm -ivh kernel-ml-5.15.2-1.el7.elrepo.x86_64.rpm2.方式
# 载入公钥
rpm --import https://www.elrepo.org/RPM-GPG-KEY-elrepo.org
# 升级安装 elrepo
rpm -Uvh http://www.elrepo.org/elrepo-release-7.0-5.el7.elrepo.noarch.rpm
# 载入 elrepo-kernel 元数据
yum --disablerepo=\* --enablerepo=elrepo-kernel repolist
# 安装最新版本的内核
yum --disablerepo=\* --enablerepo=elrepo-kernel install kernel-ml.x86_64 -y
# 删除旧版本工具包
yum remove kernel-tools-libs.x86_64 kernel-tools.x86_64 -y# 载入公钥
rpm --import https://www.elrepo.org/RPM-GPG-KEY-elrepo.org
# 升级安装 elrepo
rpm -Uvh http://www.elrepo.org/elrepo-release-7.0-5.el7.elrepo.noarch.rpm
# 载入 elrepo-kernel 元数据
yum --disablerepo=\* --enablerepo=elrepo-kernel repolist
# 安装最新版本的内核
yum --disablerepo=\* --enablerepo=elrepo-kernel install kernel-ml.x86_64 -y
# 删除旧版本工具包
yum remove kernel-tools-libs.x86_64 kernel-tools.x86_64 -y修改默认内核版本
# 查看当前实际启动顺序
grub2-editenv list
# 查看内核插入顺序
grep "^menuentry" /boot/grub2/grub.cfg | cut -d "'" -f2
# 设置默认启动
grub2-set-default 'CentOS Linux (5.15.2-1.el7.elrepo.x86_64) 7 (Core)'
# 重新创建内核配置
grub2-mkconfig -o /boot/grub2/grub.cfg
# 重启服务器
reboot
# 验证当前内核版本
uname -r# 查看当前实际启动顺序
grub2-editenv list
# 查看内核插入顺序
grep "^menuentry" /boot/grub2/grub.cfg | cut -d "'" -f2
# 设置默认启动
grub2-set-default 'CentOS Linux (5.15.2-1.el7.elrepo.x86_64) 7 (Core)'
# 重新创建内核配置
grub2-mkconfig -o /boot/grub2/grub.cfg
# 重启服务器
reboot
# 验证当前内核版本
uname -r内核版本一定要是比较高的,不然启动
WireGuard会有如下报错[#] ip link add wg0 type wireguard RTNETLINK answers: Operation not supported Unable to access interface: Protocol not supported [#] ip link delete dev wg0 Cannot find device "wg0"
server端安装
#标准内核 ,所有节点执行
$ yum install epel-release elrepo-release
$ yum install yum-plugin-elrepo kmod-wireguard wireguard-tools
iptables -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -i wg0 -o wg0 -m conntrack --ctstate NEW -j ACCEPT
iptables -t nat -A POSTROUTING -s 192.168.1.1/24 -o eth0 -j MASQUERADE (根据各个节点虚拟ip写)#标准内核 ,所有节点执行
$ yum install epel-release elrepo-release
$ yum install yum-plugin-elrepo kmod-wireguard wireguard-tools
iptables -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -i wg0 -o wg0 -m conntrack --ctstate NEW -j ACCEPT
iptables -t nat -A POSTROUTING -s 192.168.1.1/24 -o eth0 -j MASQUERADE (根据各个节点虚拟ip写)gateway 配置
cd 到wireguard 目录生成服务器私钥和公钥 privatekey、publickey;
公钥私钥成对出现,如果丢了,可以重新用此命令生成
$ wg genkey | tee privatekey | wg pubkey > publickey
$ cat > wg0.conf <<EOF
[Interface]
ListenPort = 12000
Address = 5.5.5.1/24
PrivateKey = ${GATEWAY_SERVER_PRIVATE_KEY}
DNS = 114.114.114.114
MTU = 1420
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
EOF
$ wg-quick up wg0cd 到wireguard 目录生成服务器私钥和公钥 privatekey、publickey;
公钥私钥成对出现,如果丢了,可以重新用此命令生成
$ wg genkey | tee privatekey | wg pubkey > publickey
$ cat > wg0.conf <<EOF
[Interface]
ListenPort = 12000
Address = 5.5.5.1/24
PrivateKey = ${GATEWAY_SERVER_PRIVATE_KEY}
DNS = 114.114.114.114
MTU = 1420
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
EOF
$ wg-quick up wg0NAT-A 配置
$ cd /etc/wireguard
$ wg genkey | tee privatekey | wg pubkey > publickey
$ cat > wg0.conf <<EOF
[Interface]
Address = 5.5.5.4/24
PrivateKey = ${NAT_A_PRIVATE_KEY}
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = ${GATEWAY_SERVER_PUBLIC_KEY}
AllowedIPs = 5.5.5.0/24
Endpoint = ${GATEWAY_SERVER:12000}
PersistentKeepalive = 10
EOF
#启动服务
$ wg-quick up wg0$ cd /etc/wireguard
$ wg genkey | tee privatekey | wg pubkey > publickey
$ cat > wg0.conf <<EOF
[Interface]
Address = 5.5.5.4/24
PrivateKey = ${NAT_A_PRIVATE_KEY}
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = ${GATEWAY_SERVER_PUBLIC_KEY}
AllowedIPs = 5.5.5.0/24
Endpoint = ${GATEWAY_SERVER:12000}
PersistentKeepalive = 10
EOF
#启动服务
$ wg-quick up wg0NAT-D 配置
$ cd /etc/wireguard
$ wg genkey | tee privatekey | wg pubkey > publickey
$ cat > wg0.conf <<EOF
[Interface]
Address = 5.5.5.2/24
PrivateKey = ${NAT_D_PRIVATE_KEY}
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = ${GATEWAY_SERVER_PUBLIC_KEY}
AllowedIPs = 5.5.5.0/24
Endpoint = ${GATEWAY_SERVER:12000}
PersistentKeepalive = 10
EOF
$ wg-quick up wg0$ cd /etc/wireguard
$ wg genkey | tee privatekey | wg pubkey > publickey
$ cat > wg0.conf <<EOF
[Interface]
Address = 5.5.5.2/24
PrivateKey = ${NAT_D_PRIVATE_KEY}
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = ${GATEWAY_SERVER_PUBLIC_KEY}
AllowedIPs = 5.5.5.0/24
Endpoint = ${GATEWAY_SERVER:12000}
PersistentKeepalive = 10
EOF
$ wg-quick up wg0NAT-C 配置
$ cd /etc/wireguard
$ wg genkey | tee privatekey | wg pubkey > publickey
$ cat > wg0.conf <<EOF
[Interface]
Address = 5.5.5.3/24
PrivateKey = ${NAT_C_PRIVATE_KEY}
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = ${GATEWAY_SERVER_PUBLIC_KEY}
AllowedIPs = 5.5.5.0/24
Endpoint = ${GATEWAY_SERVER:12000}
PersistentKeepalive = 10
EOF
$ wg-quick up wg0$ cd /etc/wireguard
$ wg genkey | tee privatekey | wg pubkey > publickey
$ cat > wg0.conf <<EOF
[Interface]
Address = 5.5.5.3/24
PrivateKey = ${NAT_C_PRIVATE_KEY}
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = ${GATEWAY_SERVER_PUBLIC_KEY}
AllowedIPs = 5.5.5.0/24
Endpoint = ${GATEWAY_SERVER:12000}
PersistentKeepalive = 10
EOF
$ wg-quick up wg0gateway 添加 peer
在所有的 wireguard 节点配置好之后,要在 gateway 节点添加 peer 的信息
$ cd /etc/wireguard
$ cat >> wg0.conf <<EOF
[Peer]
PublicKey = ${NAT_A_PUBLIC_KEY}
AllowedIPs = 5.5.5.4/32
PersistentKeepalive = 25
[Peer]
PublicKey = ${NAT_C_PUBLIC_KEY}
AllowedIPs = 5.5.5.3/32
PersistentKeepalive = 25
[Peer]
PublicKey = ${NAT_D_PUBLIC_KEY}
AllowedIPs = 5.5.5.2/32
PersistentKeepalive = 25
$ wg-quick down wg0 && wg-quick up wg0$ cd /etc/wireguard
$ cat >> wg0.conf <<EOF
[Peer]
PublicKey = ${NAT_A_PUBLIC_KEY}
AllowedIPs = 5.5.5.4/32
PersistentKeepalive = 25
[Peer]
PublicKey = ${NAT_C_PUBLIC_KEY}
AllowedIPs = 5.5.5.3/32
PersistentKeepalive = 25
[Peer]
PublicKey = ${NAT_D_PUBLIC_KEY}
AllowedIPs = 5.5.5.2/32
PersistentKeepalive = 25
$ wg-quick down wg0 && wg-quick up wg0连接测试
wireguard 服务操作命令
## 运行
wg-quick up wg0
## 查看连接状态
wg
## 设置开机自启
systemctl enable wg-quick@wg0.service
## 重载 每次加完VPC中继器后运行下 实际上根据经验还是有点问题,新加入的VPC可能连不上,还是需要先down然后up服务端(会引起所有VPC的短暂失联)
systemctl reload wg-quick@wg0
## 停止
wg-quick down wg0
#指定路径
wg-quick up /path/to/wg0.conf
# 删除peer
wg-quick down wg0
wg set wg0 peer $(cat cpublickey1) remove
#最好是到/etc/wireguard/ 执行命令## 运行
wg-quick up wg0
## 查看连接状态
wg
## 设置开机自启
systemctl enable wg-quick@wg0.service
## 重载 每次加完VPC中继器后运行下 实际上根据经验还是有点问题,新加入的VPC可能连不上,还是需要先down然后up服务端(会引起所有VPC的短暂失联)
systemctl reload wg-quick@wg0
## 停止
wg-quick down wg0
#指定路径
wg-quick up /path/to/wg0.conf
# 删除peer
wg-quick down wg0
wg set wg0 peer $(cat cpublickey1) remove
#最好是到/etc/wireguard/ 执行命令热加载
wg-quick并未提供重载相关的指令,但是提供了 strip 指令,可以将 conf 文件转换为 wg 指令可以识别的格式
wg syncconf wg0 <(wg-quick strip wg0)wg syncconf wg0 <(wg-quick strip wg0)配置讲解
[Interface]
PrivateKey = 【客户端私钥】
Address = 10.12.0.2/16
DNS = 114.114.114.114
MTU = 1420
PreUp = iptables -t nat -A POSTROUTING -s 192.168.0.0/16 -o wg0 -j MASQUERADE
PostUp = iptables -A FORWARD -i wg0 -j ACCEPT; iptables -A FORWARD -o wg0 -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i wg0 -j ACCEPT; iptables -D FORWARD -o wg0 -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = 【服务端公钥】
Endpoint = 【服务端IP:51820】
AllowedIPs = 10.12.0.0/16,10.10.0.0/24
PersistentKeepalive = 25[Interface]
PrivateKey = 【客户端私钥】
Address = 10.12.0.2/16
DNS = 114.114.114.114
MTU = 1420
PreUp = iptables -t nat -A POSTROUTING -s 192.168.0.0/16 -o wg0 -j MASQUERADE
PostUp = iptables -A FORWARD -i wg0 -j ACCEPT; iptables -A FORWARD -o wg0 -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i wg0 -j ACCEPT; iptables -D FORWARD -o wg0 -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = 【服务端公钥】
Endpoint = 【服务端IP:51820】
AllowedIPs = 10.12.0.0/16,10.10.0.0/24
PersistentKeepalive = 25- Address 中继器的 wg 虚拟 IP
- AllowedIPs 第一个 IP 填写的是一样的 10.12.0.0/16 代表 wireguard 的虚拟 IP 网段,后面加的是此 VPC 相访问的其他 VPC 的本地 IP 网段,不能写服务端外网ip段和本机内网ip段,只需要写本机想通过vpn组网要访问到哪个网段
- PersistentKeepalive 是保持连接的间隔
3.转发所有流量
如果你想通过 VPN 转发所有的流量,包括 VPN 子网和公网流量,需要在 [Peer] 的 AllowedIPs 中添加 0.0.0.0/0, ::/0
[Interface]
# Name = phone.example-vpn.dev
Address = 192.0.2.3/32
PrivateKey = <private key for phone.example-vpn.dev>
[Peer]
# Name = public-server1.example-vpn.dev
PublicKey = <public key for public-server1.example-vpn.dev>
Endpoint = public-server1.example-vpn.dev:51820
AllowedIPs = 0.0.0.0/0, ::/0[Interface]
# Name = phone.example-vpn.dev
Address = 192.0.2.3/32
PrivateKey = <private key for phone.example-vpn.dev>
[Peer]
# Name = public-server1.example-vpn.dev
PublicKey = <public key for public-server1.example-vpn.dev>
Endpoint = public-server1.example-vpn.dev:51820
AllowedIPs = 0.0.0.0/0, ::/03.client端
win
https://www.wireguard.com/install/
Windows [7, 8.1, 10, 11, 2008R2, 2012R2, 2016, 2019, 2022 – v0.5.3]
Download Windows InstallerBrowse MSIs
https://ccstudio.com.cn/linux/part3/wg.html
mac
macOS [app store – v1.0.15]
- 参考
https://fuckcloudnative.io/posts/wireguard-docs-practice/
# 允许客户端访问服务器端所有局域网(即PC-to-LAN,一般采用这种模式)
# 基于基本场景还需执行以下设置:## on server:
# 添加vpn网段路由到服务器端企业路由器
# 172.30.0.0/24 via [本机的局域网ip]## on client:
# 添加server端网段到本机路由表
ip route add 10.1.0.0/16 via 172.30.0.1
...
# 允许server端网络访问client端(无需ip link down + up;这里0.0.0.0/0代表所有网络)
wg set wg0 peer dLssxxxxxxxxxxxxxxxxxq98NQKOivi3MN/VM= persistent-keepalive 25 allowed-ips 172.30.0.1/32,0.0.0.0/0 endpoint 192.168.11.29:51820# 允许客户端访问服务器端所有局域网(即PC-to-LAN,一般采用这种模式)
# 基于基本场景还需执行以下设置:## on server:
# 添加vpn网段路由到服务器端企业路由器
# 172.30.0.0/24 via [本机的局域网ip]## on client:
# 添加server端网段到本机路由表
ip route add 10.1.0.0/16 via 172.30.0.1
...
# 允许server端网络访问client端(无需ip link down + up;这里0.0.0.0/0代表所有网络)
wg set wg0 peer dLssxxxxxxxxxxxxxxxxxq98NQKOivi3MN/VM= persistent-keepalive 25 allowed-ips 172.30.0.1/32,0.0.0.0/0 endpoint 192.168.11.29:51820# 将两边的局域网连成一个整体的局域网(即LAN-to-LAN)
# 基于基本场景还需执行以下设置:## on server:
# 添加vpn网段路由到服务器端企业路由器
# 172.30.0.0/24 via [本机的局域网ip]
# 添加client端网段路由到服务器端企业路由器
# 192.168.2.0/24 via [本机的局域网ip]
# ...
# 添加client端网段路由到本机路由表
ip route add 192.168.0.0/16 via 172.30.0.2
...
# 允许client端访问server端网络(无需ip link down + up)
wg set wg0 peer VbR3Kxgxxxxxxxxxxxxxxxxxzq3H4ebdgTng= allowed-ips 172.30.0.2/32,192.168.0.0/24## on client:
# 添加vpn网段路由到客户端企业路由器
# 172.30.0.0/24 via [本机的局域网ip]
# 添加server端网段路由到客户端企业路由器
# 10.1.0.0/16 via [本机的局域网ip]
# ...
# 添加server端网段路由到本机路由表
ip route add 10.1.0.0/16 via 172.30.0.1
...
# 允许server端访问client端网络(无需ip link down + up;0.0.0.0/0代表所有网络)
wg set wg0 peer dLssxxxxxxxxxxxxxxxxx98NQKOivi3MN/VM= persistent-keepalive 25 allowed-ips 172.30.0.1/32,0# 将两边的局域网连成一个整体的局域网(即LAN-to-LAN)
# 基于基本场景还需执行以下设置:## on server:
# 添加vpn网段路由到服务器端企业路由器
# 172.30.0.0/24 via [本机的局域网ip]
# 添加client端网段路由到服务器端企业路由器
# 192.168.2.0/24 via [本机的局域网ip]
# ...
# 添加client端网段路由到本机路由表
ip route add 192.168.0.0/16 via 172.30.0.2
...
# 允许client端访问server端网络(无需ip link down + up)
wg set wg0 peer VbR3Kxgxxxxxxxxxxxxxxxxxzq3H4ebdgTng= allowed-ips 172.30.0.2/32,192.168.0.0/24## on client:
# 添加vpn网段路由到客户端企业路由器
# 172.30.0.0/24 via [本机的局域网ip]
# 添加server端网段路由到客户端企业路由器
# 10.1.0.0/16 via [本机的局域网ip]
# ...
# 添加server端网段路由到本机路由表
ip route add 10.1.0.0/16 via 172.30.0.1
...
# 允许server端访问client端网络(无需ip link down + up;0.0.0.0/0代表所有网络)
wg set wg0 peer dLssxxxxxxxxxxxxxxxxx98NQKOivi3MN/VM= persistent-keepalive 25 allowed-ips 172.30.0.1/32,0案例
| 云厂商 | 公网IP地址 | 内网IP地址 | 虚拟网络IP地址 | 操作系统 | 内核版本 |
|---|---|---|---|---|---|
| 腾讯云1,master | 42.xx.xx.12 | 10.0.16.8 | 192.168.1.1 | CentOS Linux release 7.9.2009 (Core) | 5.15.2-1 |
| 腾讯云2 | 122.xx.xxx.111 | 10.0.0.6 | 192.168.1.2 | CentOS Linux release 7.9.2009 (Core) | 5.15.2-1 |
| 阿里云 | 122.xx.xx.155 | 172.17.0.3 | 192.168.1.3 | CentOS Linux release 7.9.2009 (Core) | 5.15.2-1 |
# master 节点
cat /etc/wireguard/wg0.conf
[Interface]
PrivateKey = EMWcI01iqM4zkb7xfbaaxxxxxxxxDo2GJUA=
Address = 192.168.1.1
ListenPort = 5418
[Peer]
PublicKey = 3izpVbZgPhlM+S5szOogTDTxxxxxxxxxuKuDGn4=
EndPoint = 122.xx.xxx.111:5418
AllowedIPs = 192.168.1.2/32
[Peer]
PublicKey = 0f0dn60+tBUfYgzw7rIihKbqxxxxxxxxa6Wo=
EndPoint = 122.xx.xx.155:5418
AllowedIPs = 192.168.1.3/32# master 节点
cat /etc/wireguard/wg0.conf
[Interface]
PrivateKey = EMWcI01iqM4zkb7xfbaaxxxxxxxxDo2GJUA=
Address = 192.168.1.1
ListenPort = 5418
[Peer]
PublicKey = 3izpVbZgPhlM+S5szOogTDTxxxxxxxxxuKuDGn4=
EndPoint = 122.xx.xxx.111:5418
AllowedIPs = 192.168.1.2/32
[Peer]
PublicKey = 0f0dn60+tBUfYgzw7rIihKbqxxxxxxxxa6Wo=
EndPoint = 122.xx.xx.155:5418
AllowedIPs = 192.168.1.3/32# node1 节点
cat /etc/wireguard/wg0.conf
[Interface]
PrivateKey = QGdNkzpnIkuvUU+00C6XYxxxxxxxxxK0D82qJVc=
Address = 192.168.1.2
ListenPort = 5418
[Peer]
PublicKey = 0ay8WfGOIHndWklSIVBqrsp5LDWxxxxxxxxxxxxxxQ=
EndPoint = 42.xxx.xx.16:5418
AllowedIPs = 192.168.1.1/32
[Peer]
PublicKey = 0f0dn60+tBUfYgzw7rIihKbqxxxxxxxxa6Wo=
EndPoint = 122.xx.xx.155:5418
AllowedIPs = 192.168.1.3/32# node1 节点
cat /etc/wireguard/wg0.conf
[Interface]
PrivateKey = QGdNkzpnIkuvUU+00C6XYxxxxxxxxxK0D82qJVc=
Address = 192.168.1.2
ListenPort = 5418
[Peer]
PublicKey = 0ay8WfGOIHndWklSIVBqrsp5LDWxxxxxxxxxxxxxxQ=
EndPoint = 42.xxx.xx.16:5418
AllowedIPs = 192.168.1.1/32
[Peer]
PublicKey = 0f0dn60+tBUfYgzw7rIihKbqxxxxxxxxa6Wo=
EndPoint = 122.xx.xx.155:5418
AllowedIPs = 192.168.1.3/32# node2 节点
cat /etc/wireguard/wg0.conf
[Interface]
PrivateKey = WOOObkWINkW/hqaAME9r+xxxxxxxxxm+r2Q=
Address = 192.168.1.3
ListenPort = 5418
[Peer]
PublicKey = 0ay8WfGOIHndWklSIVBqrsp5LDWxxxxxxxxxxxxxxQ=
EndPoint = 42.xxx.xx.16:5418
AllowedIPs = 192.168.1.1/32
[Peer]
PublicKey = 3izpVbZgPhlM+S5szOogTDTxxxxxxxxxuKuDGn4=
EndPoint = 122.xx.xx.155:5418
AllowedIPs = 192.168.1.2/32# node2 节点
cat /etc/wireguard/wg0.conf
[Interface]
PrivateKey = WOOObkWINkW/hqaAME9r+xxxxxxxxxm+r2Q=
Address = 192.168.1.3
ListenPort = 5418
[Peer]
PublicKey = 0ay8WfGOIHndWklSIVBqrsp5LDWxxxxxxxxxxxxxxQ=
EndPoint = 42.xxx.xx.16:5418
AllowedIPs = 192.168.1.1/32
[Peer]
PublicKey = 3izpVbZgPhlM+S5szOogTDTxxxxxxxxxuKuDGn4=
EndPoint = 122.xx.xx.155:5418
AllowedIPs = 192.168.1.2/324.分流案例
官方的WireGuard并没有分流功能,对国内用户实在是不太友好。不过,NekoRay作为基于Sing-box开发的客户端,由于其上游Sing-box核心支持WireGuard的协议且支持分流,故我们可以使用NekoRay这个客户端,加上我们的WARP的WireGuard节点配置文件,就可以将WARP节点作为日常节点使用
- Windows / Linux 的电脑并安装 NekoRay
4.1下载
https://github.com/MatsuriDayo/nekoray/releases
- 打开Nekoray客户端,依次进入“程序”→“首选项”→“基本设置”→“核心”--->"选中sing-box"
- 依次进入“程序”→“首选项”→“路由设置”
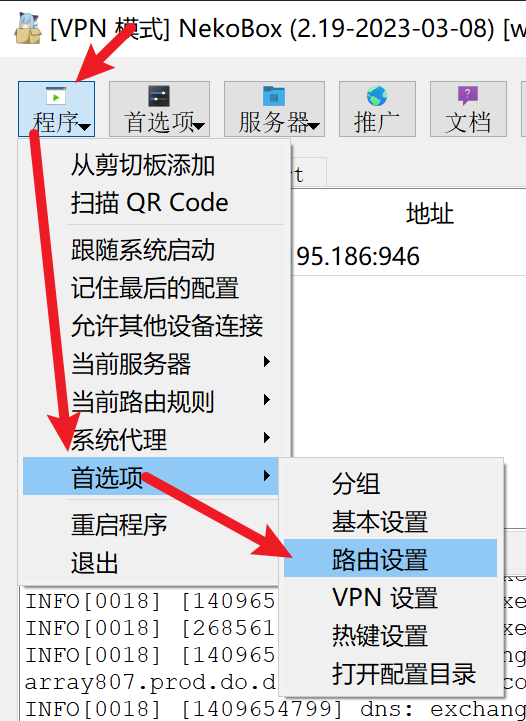
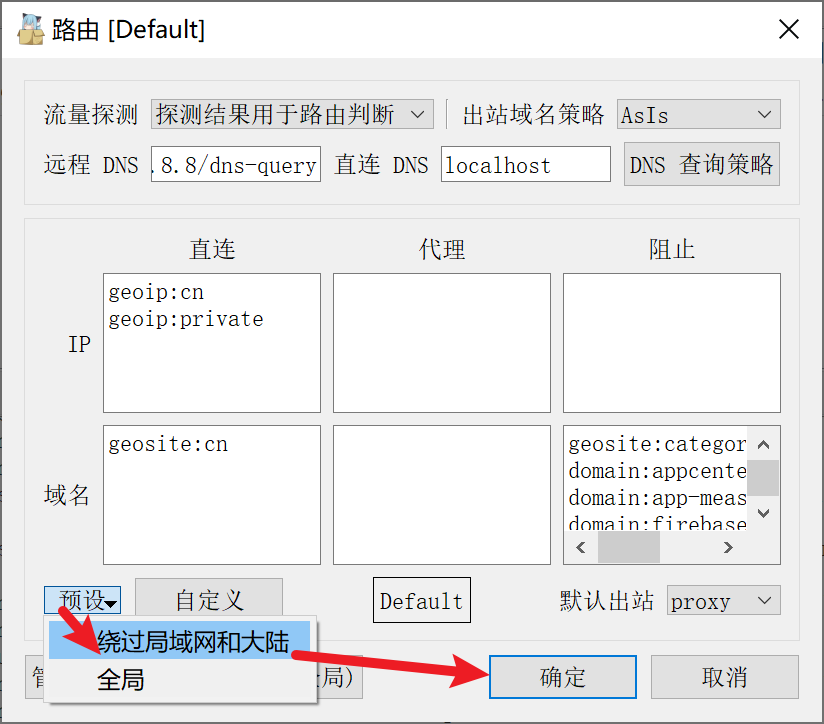
- 点击预设中的“绕过局域网和大陆”,然后点击“确定”保存
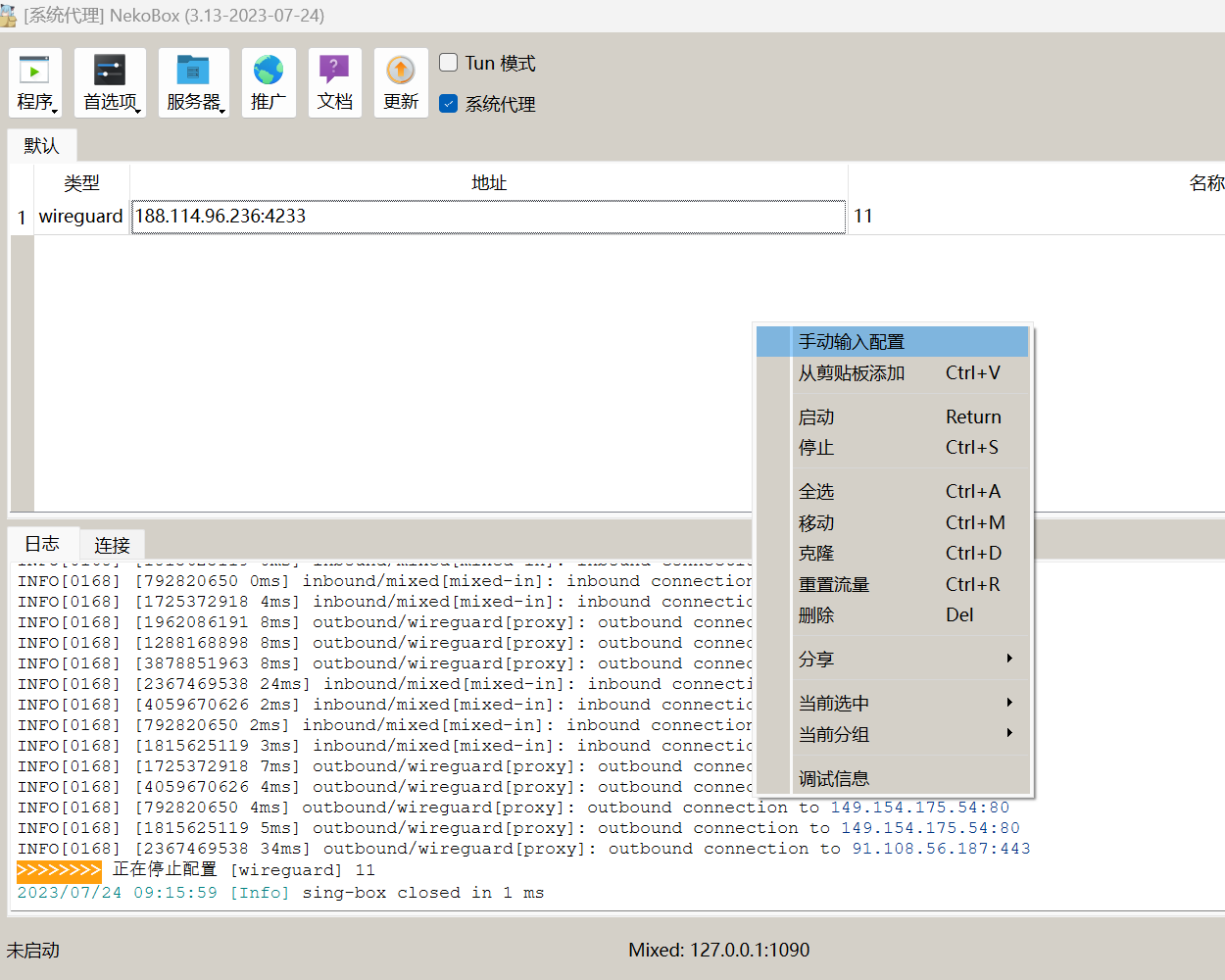
- 在主界面空白处右键,点击“手动输入配置”
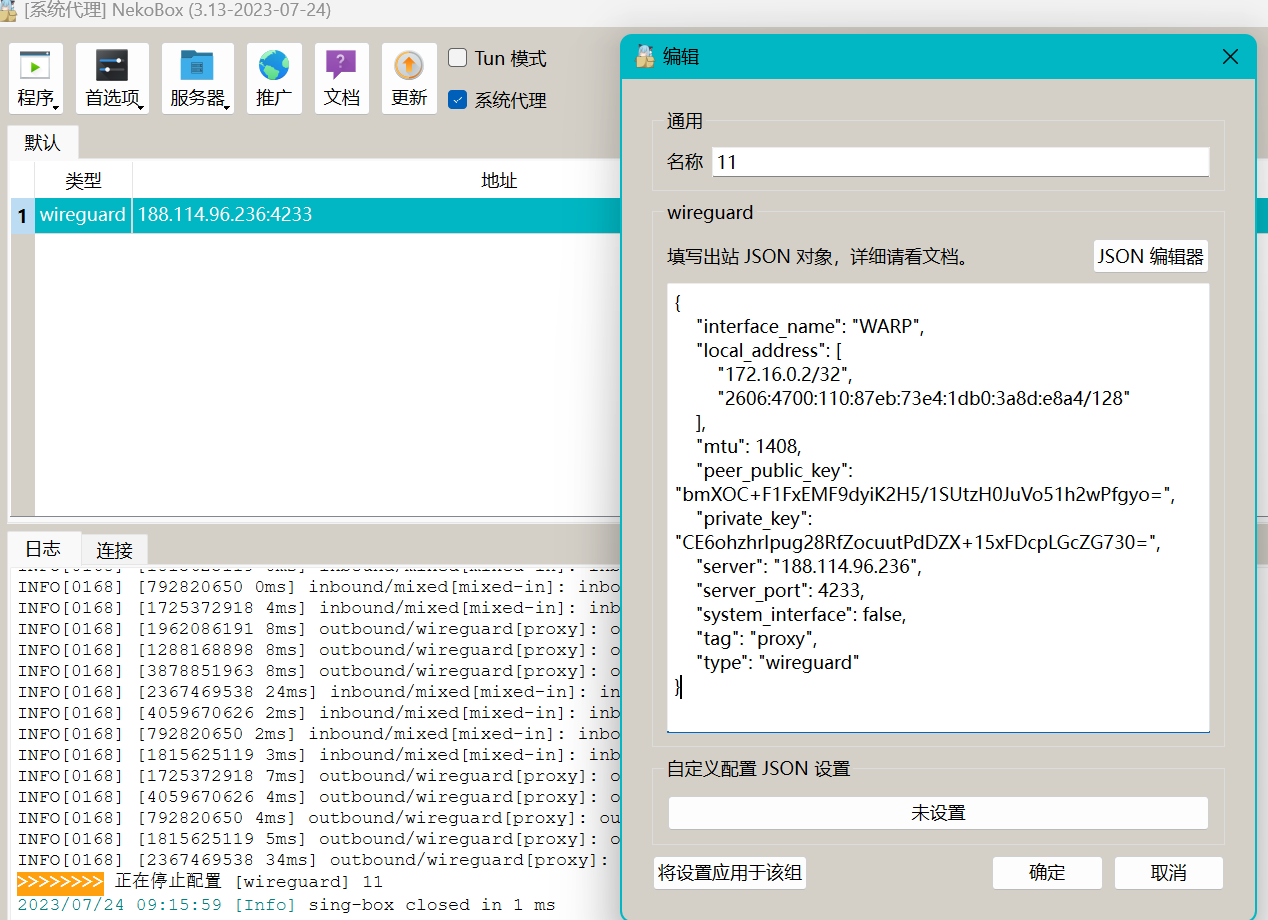
- 类型选择“自定义(Sing-box出站)”,名称自定义,然后底下的json内容可参考下方的模板【主要是替换优选Endpoint IP、公私钥和内网IP地址
{
"interface_name": "WARP",
"local_address": [
"172.16.0.2/32",
"2606:4700:110:87eb:73e4:1db0:3a8d:e8a4/128"
],
"mtu": 1408,
"peer_public_key": "bmXOC+F1FxEMF9dyiK2H5/1SUtzH0JuVo51h2wPfgyo=",
"private_key": "CE6ohzhrIpug28RfZocuutPdDZX+15xFDcpLGcZG730=",
"server": "188.114.96.236",
"server_port": 4233,
"system_interface": false,
"tag": "proxy",
"type": "wireguard"
}{
"interface_name": "WARP",
"local_address": [
"172.16.0.2/32",
"2606:4700:110:87eb:73e4:1db0:3a8d:e8a4/128"
],
"mtu": 1408,
"peer_public_key": "bmXOC+F1FxEMF9dyiK2H5/1SUtzH0JuVo51h2wPfgyo=",
"private_key": "CE6ohzhrIpug28RfZocuutPdDZX+15xFDcpLGcZG730=",
"server": "188.114.96.236",
"server_port": 4233,
"system_interface": false,
"tag": "proxy",
"type": "wireguard"
}
- 启动
右键配置,启动
- 测试是否分流
参考文档: